Fortinet NSE8_812 Fortinet NSE 8 - Written Exam Practice Test
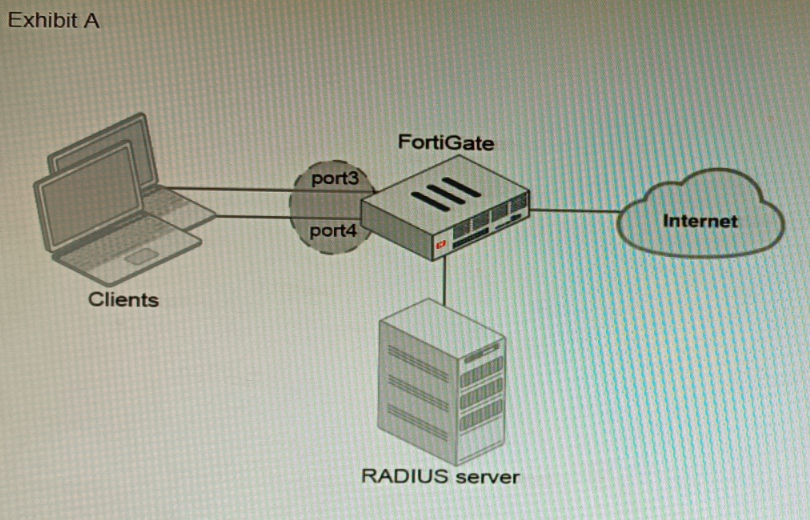
Refer to the exhibit.
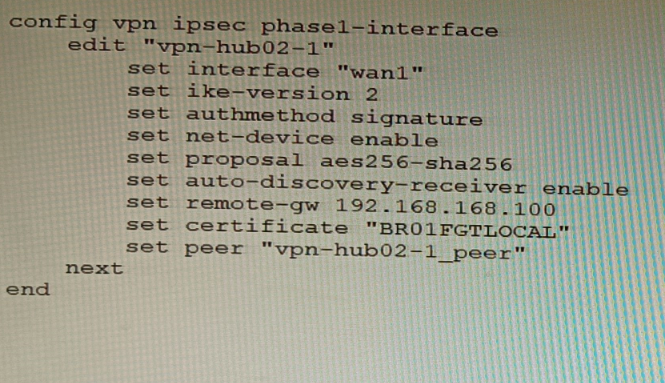
To facilitate a large-scale deployment of SD-WAN/ADVPN with FortiGate devices, you are tasked with configuring the FortiGate devices to support injecting of IKE routes on the ADVPN shortcut tunnels.
Which three commands must be added or changed to the FortiGate spoke config vpn ipsec phasei-interface options referenced in the exhibit for the VPN interface to enable this capability? (Choose three.)
Answer : B, D, E
Bmust be set to enable mode-cfg, which is required for injecting IKE routes on the ADVPN shortcut tunnels.
Dmust be set to enable add-route, which is the command that actually injects the IKE routes.
Emust be set to enable mode-cfg-allow-client-selector, which allows custom phase 2 selectors to be configured.
The other options are incorrect. Option A is incorrect because net-device disable is not required for injecting IKE routes on the ADVPN shortcut tunnels. Option C is incorrect because IKE version 1 is not supported for ADVPN.
References:
Phase 2 selectors and ADVPN shortcut tunnels | FortiGate / FortiOS 7.2.0
Configuring SD-WAN/ADVPN with FortiGate | FortiGate / FortiOS 7.2.0
A remote worker requests access to an SSH server inside the network. You deployed a ZTNA Rule to their FortiClient. You need to follow the security requirements to inspect this traffic.
Which two statements are true regarding the requirements? (Choose two.)
Which two statements are correct on a FortiGate using the FortiGuard Outbreak Protection Service (VOS)? (Choose two.)
Answer : C, E
c) The antivirus database queries FortiGuard with the hash of a scanned file. This is how the FortiGuard VOS service works. The FortiGate queries FortiGuard with the hash of a scanned file, and FortiGuard returns a list of known malware signatures that match the hash.
e) The hash signatures are obtained from the FortiGuard Global Threat Intelligence database. This is where the FortiGuard VOS service gets its hash signatures from. The FortiGuard Global Threat Intelligence database is updated regularly with new malware signatures.
Refer to the exhibit, which shows the high availability configuration for the FortiAuthenticator (FAC1).
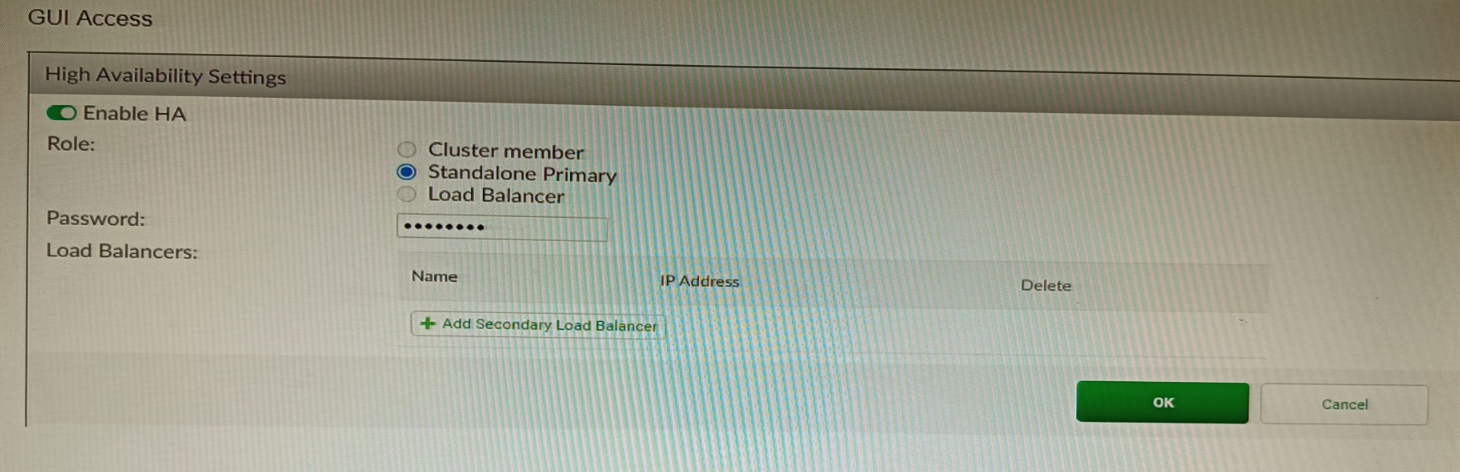
Based on this information, which statement is true about the next FortiAuthenticator (FAC2) member that will join an HA cluster with this FortiAuthenticator (FAC1)?
A customer is planning on moving their secondary data center to a cloud-based laaS. They want to place all the Oracle-based systems Oracle Cloud, while the other systems will be on Microsoft Azure with ExpressRoute service to their main data center.
They have about 200 branches with two internet services as their only WAN connections. As a security consultant you are asked to design an architecture using Fortinet products with security, redundancy and performance as a priority.
Which two design options are true based on these requirements? (Choose two.)
Answer : A, C
a) Systems running on Azure will need to go through the main data center to access the services on Oracle Cloud. This is because the Oracle Cloud is not directly connected to the Azure Cloud. The traffic will need to go through the main data center in order to reach the Oracle Cloud.
c) Branch FortiGate devices must be configured as VPN clients for the branches' internal network to be able to access Oracle services without using public IPs. This is because the Oracle Cloud does not allow direct connections from the internet. The traffic will need to go through the FortiGate devices in order to reach the Oracle Cloud.
The other options are not correct.
b) Use FortiGate VM for IPSEC over ExpressRoute, as traffic is not encrypted by Azure. This is not necessary. Azure does encrypt traffic over ExpressRoute.
d) Two ExpressRoute services to the main data center are required to implement SD-WAN between a FortiGate VM in Azure and a FortiGate device at the data center edge. This is not necessary. A single ExpressRoute service can be used to implement SD-WAN between a FortiGate VM in Azure and a FortiGate device at the data center edge.