Amazon AWS Certified Developer - Associate DVA-C02 Exam Practice Test
A developer is designing a fault-tolerant environment where client sessions will be saved.
How can the developer ensure that no sessions are lost if an Amazon EC2 instance fails?
Answer : C
An ecommerce company is planning to migrate an on-premises Microsoft SQL Server database to the AWS Cloud. The company needs to migrate the database to SQL Server Always On availability groups. The cloud-based solution must be highly available.
Which solution will meet these requirements?
Answer : C
Why Option C is Correct:
SQL Server Always On availability groups require a shared storage solution. Amazon FSx for Windows File Server provides the shared storage necessary to implement Always On availability groups in a highly available configuration.
Why Other Options are Incorrect:
Option A: A single EBS volume cannot provide shared storage for Always On availability groups.
Option B: RDS does not support SQL Server Always On availability groups.
Option D: S3 is not a suitable storage tier for SQL Server database operations.
AWS Documentation Reference:
Amazon FSx for Windows File Server
A developer has an application that makes batch requests directly to Amazon DynamoDB by using the BatchGetItem low-level API operation. The responses frequently return values in the UnprocessedKeys element.
Which actions should the developer take to increase the resiliency of the application when the batch response includes values in UnprocessedKeys? (Choose two.)
Answer : B, C
The UnprocessedKeys element indicates that the BatchGetItem operation did not process all of the requested items in the current response. This can happen if the response size limit is exceeded or if the table's provisioned throughput is exceeded. To handle this situation, the developer should retry the batch operation with exponential backoff and randomized delay to avoid throttling errors and reduce the load on the table. The developer should also use an AWS SDK to make the requests, as the SDKs automatically retry requests that return UnprocessedKeys.
[BatchGetItem - Amazon DynamoDB]
[Working with Queries and Scans - Amazon DynamoDB]
[Best Practices for Handling DynamoDB Throttling Errors]
Users are reporting errors in an application. The application consists of several micro services that are deployed on Amazon Elastic Container Serves (Amazon ECS) with AWS Fargate.
When combination of steps should a developer take to fix the errors? (Select TWO)
Answer : A, E
The combination of steps that the developer should take to fix the errors is to deploy AWS X-Ray as a sidecar container to the microservices and instrument the ECS task to send the stdout and stderr output to Amazon CloudWatch Logs. This way, the developer can use AWS X-Ray to analyze and debug the performance of the microservices and identify any issues or bottlenecks. The developer can also use CloudWatch Logs to monitor and troubleshoot the logs from the ECS task and detect any errors or exceptions. The other options either involve using AWS X-Ray as a daemon set, which is not supported by Fargate, or using the PutTraceSegments API call, which is not necessary when using a sidecar container.
An application is processing clickstream data using Amazon Kinesis. The clickstream data feed into Kinesis experiences periodic spikes. The PutRecords API call occasionally fails and the logs show that the failed call returns the response shown below:
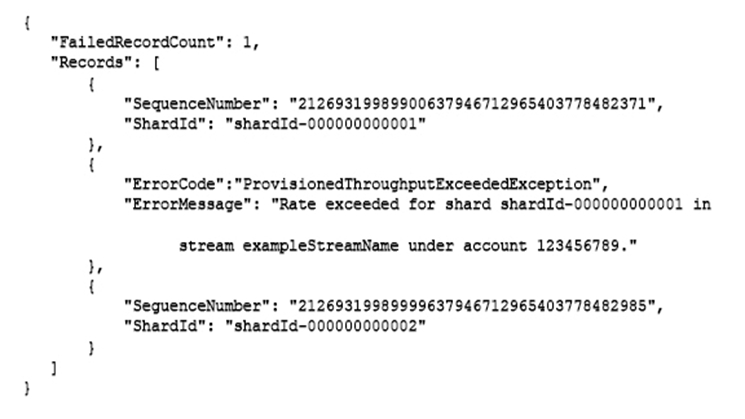
Which techniques will help mitigate this exception? (Choose two.)
Answer : A, C
The response from the API call indicates that the ProvisionedThroughputExceededException exception has occurred. This exception means that the rate of incoming requests exceeds the throughput limit for one or more shards in a stream. To mitigate this exception, the developer can use one or more of the following techniques:
Implement retries with exponential backoff. This will introduce randomness in the retry intervals and avoid overwhelming the shards with retries.
Reduce the frequency and/or size of the requests. This will reduce the load on the shards and avoid throttling errors.
Increase the number of shards in the stream. This will increase the throughput capacity of the stream and accommodate higher request rates.
Use a PutRecord API instead of PutRecords. This will reduce the number of records per request and avoid exceeding the payload limit.
[ProvisionedThroughputExceededException - Amazon Kinesis Data Streams Service API Reference]
[Best Practices for Handling Kinesis Data Streams Errors]
A developer is creating a mobile app that calls a backend service by using an Amazon API Gateway REST API. For integration testing during the development phase, the developer wants to simulate different backend responses without invoking the backend service.
Which solution will meet these requirements with the LEAST operational overhead?
A team of developed is using an AWS CodePipeline pipeline as a continuous integration and continuous delivery (CI/CD) mechanism for a web application. A developer has written unit tests to programmatically test the functionality of the application code. The unit tests produce a test report that shows the results of each individual check. The developer now wants to run these tests automatically during the CI/CD process.
Answer : C
The solution that will meet the requirements is to add a new stage to the pipeline. Use AWS CodeBuild as the provider. Add the new stage before the stage that deploys code revisions to the test environment. Write a buildspec that fails the CodeBuild stage if any test does not pass. Use the test reports feature of CodeBuild to integrate the report with the CodeBuild console. View the test results in CodeBuild. Resolve any issues. This way, the developer can run the unit tests automatically during the CI/CD process and catch any bugs before deploying to the test environment. The developer can also use the test reports feature of CodeBuild to view and analyze the test results in a graphical interface. The other options either involve running the tests manually, running them after deployment, or using a different provider that requires additional configuration and integration.