Arcitura Education Cloud Technology Lab C90.03 Exam Practice Test
Cloud Provider X has deployed a virtualization environment in Cloud X comprised of Physical Server A hosting Virtual Servers A and B. Cloud Provider X implements Cloud Service A on Virtual Server A and makes it available to Cloud Service Consumer A, which interacts with Cloud Service A by sending and receiving messages (1, 2). Cloud Provider Y has deployed a virtualization environment comprised of Physical Server B hosting Virtual Servers C and D. Virtual Server C is made available to Cloud Service Consumer B, which interacts with Virtual Server C (3,4) in order to prepare for the deployment of a new cloud service that will be used internally by Cloud Provider Y to process data obtained from Cloud Service A .
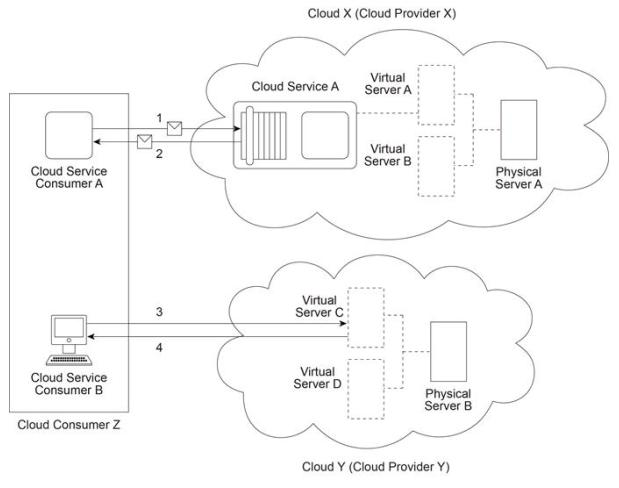
Cloud Consumer Z and Cloud Provider X belong to the same organization. Cloud Provider Y is a third-party organization. Which of the following statements provides a valid scenario that accurately describes the involvement of cloud deployment models, cloud delivery models, roles and/or boundaries? (Note that the correct answer represents one of multiple valid scenarios that can exist.)
Answer : D
A cloud consumer is interested in leasing cloud-based virtual servers. It compares the virtual servers offered by Cloud Provider X and Cloud Provider Y. Cloud X (owned by Cloud Provider X) and Cloud Y (owned by Cloud Provider Y) both provide shared physical servers that host multiple virtual servers for other cloud consumers. The virtual servers on Cloud X are accessed directly, whereas the virtual servers on Cloud Y are accessed via an automated scaling listener. On Cloud X, virtual servers are pre-configured to support a specific amount of concurrent cloud service consumers. When this threshold is exceeded, cloud service consumer requests are rejected. Due to the use of the automated scaling listener, virtual servers on Cloud Y can provide a greater level of elasticity.
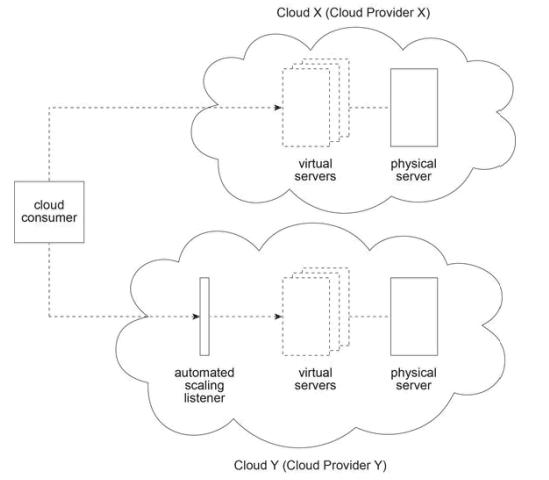
The hourly cost to the cloud consumer to use a virtual server on Cloud X is half that of the cost to use a virtual server on Cloud Y. Within a one month period, Cloud Provider X bases its hourly charge on the maximum number of virtual servers used. Within a one month period, Cloud Provider Y bases its hourly charges on actual virtual server usage. Cloud Provider Y charges $20 for each hour that a cloud consumer uses a virtual server. The cloud consumer predicts its monthly usage requirements to be as follows:
Number Of Virtual Servers
Usage
3
20 Hours
4
30 Hours
5
50 Hours
The cloud consumer is required to choose the cloud provider with the lowest on-going cost, based on its predicted usage. Which of the following statements accurately calculates the on-going usage costs of Cloud Providers X and Y and correctly states the cloud provider that the cloud consumer must choose?
Answer : D
Cloud X (owned by Cloud Provider X) provides Physical Server A which hosts Virtual Servers A and B. Virtual Server B hosts Ready-Made Environments A and B. Cloud Service Consumer A uses Virtual Server A as part of an IaaS leasing agreement in which Cloud Consumer A is charged a fixed monthly fee for unlimited access. Cloud Service Consumers B and C use Ready-Made Environments A and B respectively as part of a PaaS leasing agreement based on per-minute usage fees. In both cases, access is monitored via Pay-For-Use Monitor A, which keeps track of log-in and log-out times in order to calculate the usage charges that are billed to Cloud Consumers B and C . Virtual Server A begins generating a series of exceptions. Soon thereafter, Virtual Server B becomes destabilized, resulting in further exceptions being raised in Ready-Made Environments A and B. Cloud Service Consumers B and C receive a series of error messages until both of their connections are dropped Finally, Physical Server A shuts down completely. A subsequent investigation reveals that Virtual Server A was the victim of a security attack performed by a malicious cloud service consumer, the attacker generated increased loads of external communication requests on Virtual Server A and the underlying network, causing Physical Server A (along with Virtual Server B) to eventually shut down.
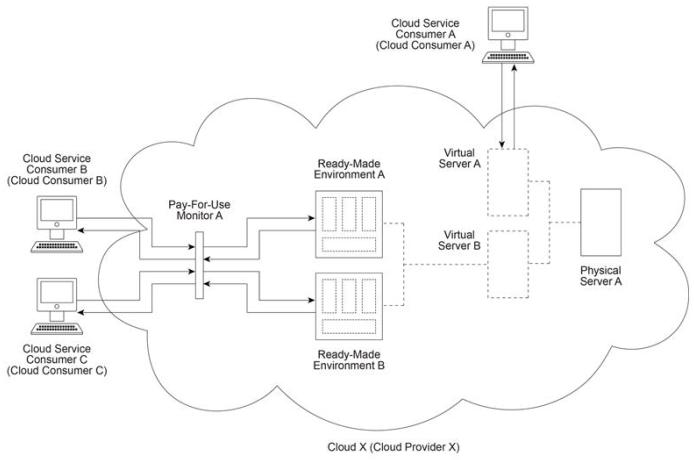
Which of the following statements accurately identifies the type of security threat that corresponds to the described attack - and -provides a solution that can directly mitigate this type of security threat within Cloud X?
Answer : C
A cloud consumer is interested in leasing cloud-based virtual servers. It compares the virtual servers offered by Cloud Provider X and Cloud Provider Y. Cloud X (owned by Cloud Provider X) and Cloud Y (owned by Cloud Provider Y) both provide shared physical servers that host multiple virtual servers for other cloud consumers. The virtual servers on Cloud X are accessed directly, whereas the virtual servers on Cloud Y are accessed via an automated scaling listener. On Cloud X, virtual servers are pre-configured to support a specific amount of concurrent cloud service consumers. When this threshold is exceeded, cloud service consumer requests are rejected. Due to the use of the automated scaling listener, virtual servers on Cloud Y can provide a greater level of elasticity. The hourly cost to the cloud consumer to use a virtual server on Cloud X is half that of the cost to use a virtual server on Cloud Y. Within a one month period, Cloud Provider X bases its hourly charge on the maximum number of virtual servers used. Within a one month period, Cloud Provider Y bases its hourly charges on actual virtual server usage. Cloud Provider Y charges $20 for each hour that a cloud consumer uses a virtual server.
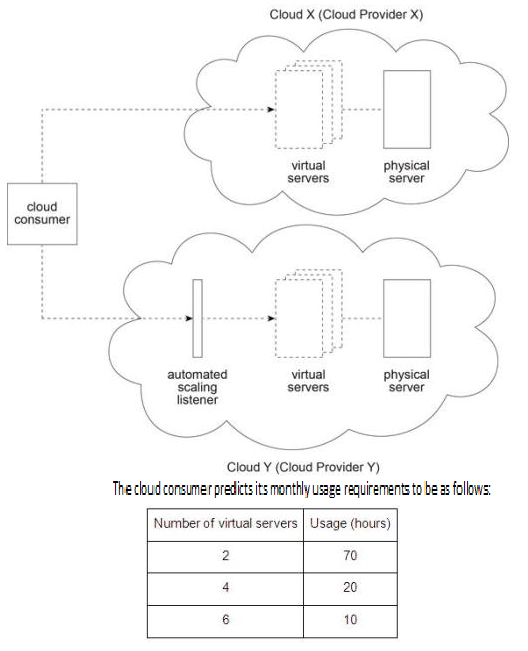
The cloud consumer is required choose the cloud provider with the lowest on-going cost based on its predicted usage. Which of the following statements accurately calculates the on-going usage costs of Cloud Providers X and Y and correctly states the cloud provider that the cloud consumer must choose?
Answer : A
Cloud Provider X (which owns Cloud X) deploys two physical servers (Physical Servers A and B) and two databases (Databases A and B). Virtual Servers A and B are hosted by Physical Server A and Ready-Made Environments A and B are hosted by Virtual Server B . Virtual Servers C and D are hosted by Physical Server B . Cloud Service Consumer A regularly accesses Virtual Server D in order to test and deploy a new cloud service that was developed on-premise by the cloud consumer organization operating Cloud Service Consumer A . Cloud Service Consumer B (operated by a different cloud consumer organization) has been regularly accessing Ready-Made Environment A in order to develop and deploy a different new cloud service. The cloud consumer organizations that own and operate Cloud Service Consumers A and B will soon be ready to launch their respective cloud services for use by their customers. Both cloud consumer organizations are concerned that Cloud X does not provide sufficient security and they demand that Cloud Provider X take the necessary steps to mitigate the denial of service, insufficient authorization and overlapping trust boundaries security threats.
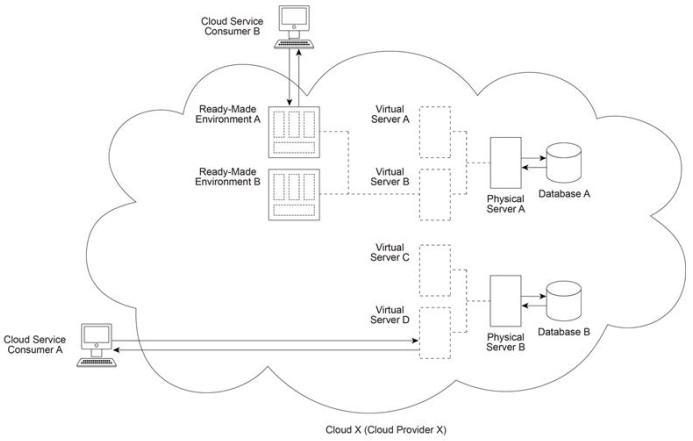
Which of the following statements accurately describes the cloud delivery models used now by the cloud service consumers and in the future by their customers - and - further describes a solution that fulfills the identified security requirements by implementing a single cloud security mechanism?
Answer : C
Organization A has been expanding and, as a result, is outgrowing the processing capacity of its on-premise Service A implementation. It is determined that this is due to usage thresholds of Service A and complex data processing limitations in Database A . The diagram depicts Organization A's current on-premise environment, where Service Consumers A . B and C attempt to access Service A at the same time. Service Consumer A successfully accesses Service A, which then successfully retrieves the requested data (1). Service Consumer B successfully accesses Service A, but due to the complex data structure, the request for the data times out and fails (2). Finally, Service Consumer C attempts to access Service A, but is rejected because Service A is unable to accept more concurrent requests.
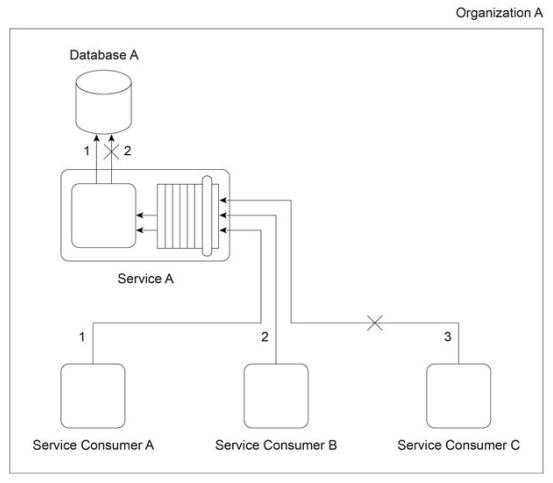
Organization A is required to continue using its on-premise Service A implementation, with the exception of Database A, which does not need to remain on-premise. Database A is dedicated to Service A and is comprised of relational data. Which of the following statements provides a solution that uses cloud-based IT resources to solve the performance limitations of Service A and Database A?
Answer : D
Cloud Provider X has deployed a virtualization environment in Cloud X comprised of Physical Server A hosting Virtual Servers A and B. Cloud Provider X implements Cloud Service A on Virtual Server A and makes it available to Cloud Service Consumer A, which interacts with Cloud Service A by sending and receiving messages (1, 2). Cloud Provider Y has deployed a virtualization environment comprised of Physical Server B hosting Virtual Servers C and D. Virtual Server C is made available to Cloud Service Consumer B, which interacts with Virtual Server C (3,4) in order to prepare for the deployment of a new cloud service that will be used internally by Cloud Provider Y to process data obtained from Cloud Service A .
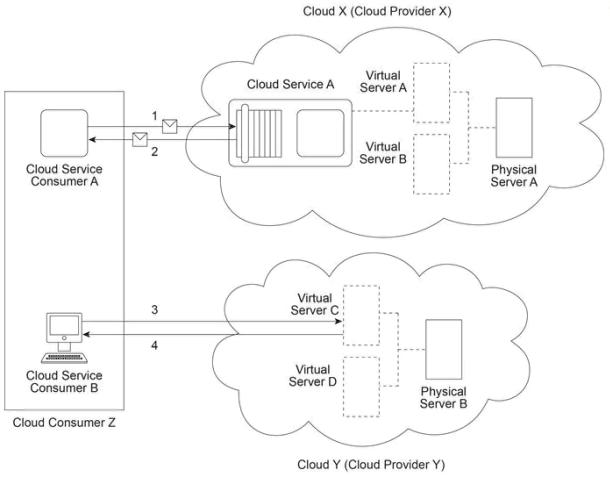
Cloud X is administered by a group of organizations and makes Cloud Service A available only to cloud service consumers from that group. Cloud Consumer Z belongs to one of the organizations within this group. Cloud Y and Cloud Consumer Z are owned by the same organization. Which of the following statements provides a valid scenario that accurately describes the involvement of cloud deployment models, cloud delivery models, roles and/or boundaries? (Note that the correct answer represents one of multiple valid scenarios that can exist.)
Answer : C