Arcitura Education SOA Security Lab S90.20 Exam Practice Test
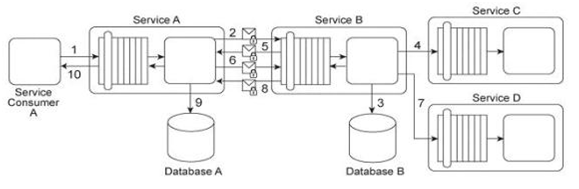
Service Consumer A sends a request message to Service A (1), after which Service A sends a request message with security credentials to Service B (2). Service B authenticates the request and, if the authentication is successful, writes data from the request message into Database B (3). Service B then sends a request message to Service C (4), which is not required to issue a response message. Service B then sends a response message back to Service A (5). After processing Service B's response, Service A sends another request message with security credentials to Service B (6). After successfully authenticating this second request message from Service A, Service B sends a request message to Service D (7). Service D is also not required to issue a response message. Finally, Service B sends a response message to Service A (8), after which Service A records the response message contents in Database A (9) before sending its own response message to Service Consumer A (10). To use Service A, Service Consumer A is charged a per usage fee. The owner of Service Consumer A has filed a complaint with the owner of Service A, stating that the bills that have been issued are for more usage of Service A than Service Consumer A actually used. Additionally, it has been discovered that malicious intermediaries are intercepting and modifying messages being sent from Service B to Services C and D .Because Services C and D do not issue response messages, the resulting errors and problems were not reported back to Service B .Which of the following statements describes a solution that correctly addresses these problems?
Answer : A
Service A provides a data access capability that can be used by a variety of service consumers. The database records accessed by Service A are classified as either private or public. There are two types of service consumers that use Service A:
Service consumers with public access permissions (allowed to access only public data records) and service consumers with private access permissions (allowed to access all data records). For performance reasons the Service A architecture uses a single database, named Database A .Each record in Database A is classified as either private or public. After Service A is invoked by a service consumer (1), it authenticates the request message using an identity store and retrieves the corresponding authorization (2, 3). Once authorized, the service consumer's request is submitted to Database A (4), which then returns the requested data (5) If the service consumer has private access permissions, all of the returned data is included in Service A's response message (6). If the service consumer has public access permissions, then Service A first filters the data in order to remove all unauthorized private data records, before sending to the response message to the service consumer (6). An investigation recently detected that private data has been leaked to unauthorized service consumers. An audit of the Service A architecture revealed that Service A's filtering logic is flawed, resulting in situations where private data was accidentally shared with service consumers that only have public access permissions. Further, it was discovered that attackers have been monitoring response messages sent by Service A in order to capture private data. It is subsequently decided to split Database A into two databases:
one containing only private data (the Private Database) and the other containing only public data (the Public Database). What additional changes are necessary to address these security problems?

Answer : A
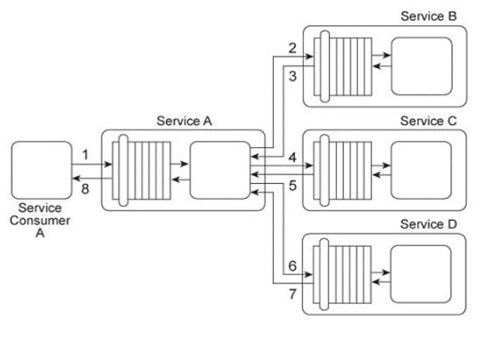
Service A provides a data retrieval capability that can be used by a range of service consumers, including Service Consumer A, In order to retrieve the necessary data. Service Consumer A first sends a request message to Service A (1). Service A then exchanges request and response messages with Service B (2, 3). Service C (4, 5), and Service D (6. 7). After receiving all three response messages from Services B .C .and D, Service A assembles the collected data into a response message that it returns to Service Consumer A (8). The Service A data retrieval capability has been suffering from poor performance, which has reduced its usefulness to Service Consumer A .Upon studying the service composition architecture, it is determined that the performance problem can be partially attributed to redundant validation by service contracts for compliance to security policies. Services B and C have service contracts that contain the same two security policies. And, Service D has a service contract that contains a security policy that is also part of Service A's service contract. What changes can be made to the service contracts in order to improve the performance of the service composition while preserving the security policy compliance requirements?

Answer : B
Service Consumer A sends a request message to Service A (1), after which Service A sends a request message with security credentials to Service B (2). Service B authenticates the request and, if the authentication is successful, writes data from the request message into Database B (3). Service B then sends a request message to Service C (4), which is not required to issue a response message. Service B then sends a response message back to Service A (5). After processing Service B's response, Service A sends another request message with security credentials to Service B (6). After successfully authenticating this second request message from Service A, Service B sends a request message to Service D (7). Service D is also not required to issue a response message. Finally, Service B sends a response message to Service A (8), after which Service A records the response message contents in Database A (9) before sending its own response message to Service Consumer A (10).

Services A and B use digital certificates to support message integrity and authentication. With every message exchange between the two services (2, 5, 6, 8), the digital certificates are used. It has been determined that both Databases A and B are vulnerable to malicious attackers that may try to directly access sensitive data records. Furthermore, performance logs have revealed that the current exchange of digital certificates between Services A and B is unacceptably slow. How can the integrity and authenticity of messages exchanged between Services A and B be maintained, but with improved runtime performance - and - how can Databases A and B be protected with minimal additional impact on performance?
Answer : B
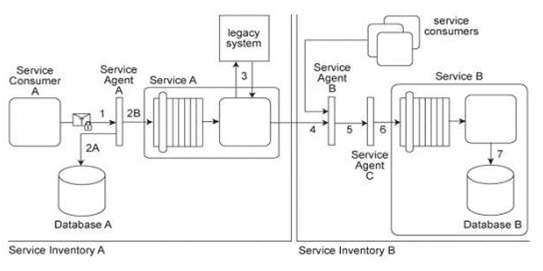
Service Consumer A sends a request message with an authentication token to Service A, but before the message reaches Service A, it is intercepted by Service Agent A (1). Service Agent A validates the security credentials and also validates whether the message is compliant with Security Policy A .If either validation fails, Service Agent A rejects the request message and writes an error log to Database A (2A). If both validations succeed, the request message is sent to Service A (2B). Service A retrieves additional data from a legacy system (3) and then submits a request message to Service B Before arriving at Service B, the request message is intercepted by Service Agent B (4) which validates its compliance with Security Policy SIB then Service Agent C (5) which validates its compliance with Security Policy B .If either of these validations fails, an error message is sent back to Service A .that then forwards it to Service Agent A so that it the error can be logged in Database A (2A). If both validations succeed, the request message is sent to Service B (6). Service B subsequently stores the data from the message in Database B (7). Service A and Service Agent A reside in Service Inventory A .Service B and Service Agents B and C reside in Service Inventory B .Security Policy SIB is used by all services that reside in Service Inventory B .Service B can also be invoked by other service consumers from Service Inventory B .Request messages sent by these service consumers must also be compliant with Security Policies SIB and B .Access to the legacy system in Service Inventory A is currently only possible via Service A, which means messages must be validated for compliance with Security Policy A .A new requirement has emerged to allow services from Service Inventory B to access the legacy system via a new perimeter service that will be dedicated to processing request messages from services residing in Service Inventory B .Because the legacy system has no security features, all security processing will need to be carried out by the perimeter service. However, there are parts of Security Policy A that are specific to Service A and do not apply to the legacy system or the perimeter service. Furthermore, response messages sent by the perimeter service to services from Service Inventory B will still need to be validated for compliance to Security Policy B and Security Policy SIB .How can the Policy Centralization pattern be correctly applied without compromising the policy compliance requirements of services in both service inventories?
Answer : C
Service A provides a data retrieval capability that can be used by a range of service consumers, including Service Consumer A .In order to retrieve the necessary data, Service Consumer A first sends a request message to Service A (1). Service A then exchanges request and response messages with Service B (2, 3), Service C (4, 5), and Service D (6. 7). After receiving all three response messages from Services B .C .and D, Service A assembles the collected data into a response message that it returns to Service Consumer A (8). The owner of Service A charges service consumers for each usage of the data retrieval capability. Recently, the owner of Service Consumer A has complained that the data returned by Service A is incorrect, incomplete, and from invalid sources. As evidence, the Service Consumer A owner has presented the owner of Service A with sample messages containing the incorrect and incomplete contents. As a result, the Service Consumer A owner has refused to pay the usage fees. Subsequent to an internal investigation, the owner of Service A determines that the data returned by Service A is consistently correct and complete. There are suspicions that the Service Consumer A owner is altering the original messages and issuing these complaints fraudulently in order to avoid paying the usage fees. How can the owner of Service A prove that Service A is returning correct and complete data and that this data originated from the correct sources?
Answer : B
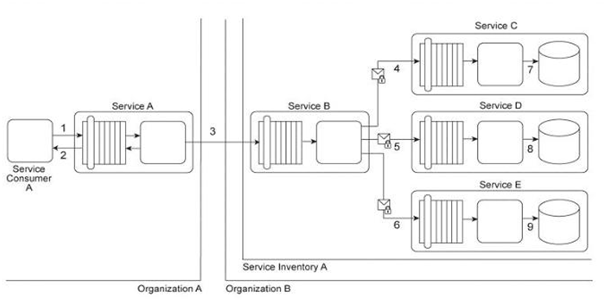
Service Consumer A sends a request to Service A (1). Service A replies with an acknowledgement message (2) and then processes the request and sends a request message to Service B (3). This message contains confidential financial data. Service B sends three different request messages together with its security credentials to Services C, D, and E (4, 5, 6). Upon successful authentication, Services C, D, and E store the data from the message in separate databases (7, 8, 9) Services B, C, D, and E belong to Service Inventory A, which further belongs to Organization B .Service Consumer A and Service A belong to Organization A .The service contracts of Services A and B both comply with the same XML schema. However, each organization employs different security technologies for their service architectures. To protect the confidential financial data sent by Service A to Service B, each organization decides to independently apply the Data Confidentiality and the Data Origin Authentication patterns to establish message-layer security for external message exchanges. However, when an encrypted and digitally signed test message is sent by Service A to Service B, Service B was unable to decrypt the message. Which of the following statements describes a solution that solves this problem?
Answer : A