Blockchain BTA Certified Blockchain Security Professional CBSP Exam Practice Test
If an attacker can find two values that hash to the same output what is it called?
Answer : C
A blockchain-based solution best achieves which of the following goals?
Answer : C
Which smart contract auditing strategy involves graphing how the code executes and looks for anomalies?
Answer : C
This sample code is vulnerable to which of the following attacks?
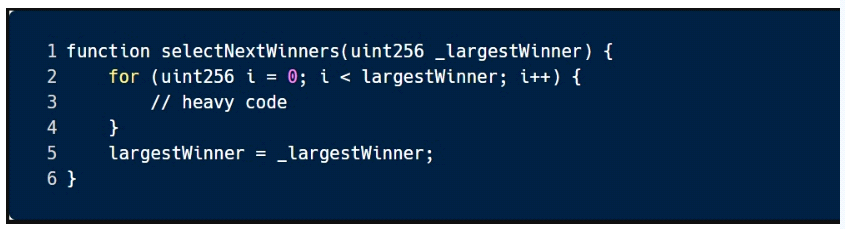
Answer : A
Which of the following are common inputs to the algorithm to select the next block creator in Proof of Stake? Select all that apply
Answer : B, C, D
Which of the following blockchains does NOT tie real-world identity to public keys on the blockchain?
Answer : B
Which of the following blockchains separates transaction validation and ordering of transactions in blocks into separate steps?
Answer : A