Cisco Conducting Forensic Analysis and Incident Response Using Cisco CyberOps Technologies 300-215 CBRFIR Exam Questions
Which scripts will search a log file for the IP address of 192.168.100.100 and create an output file named parsed_host.log while printing results to the console?


Answer : B
To determine the correct script, we evaluate the following requirements:
The script must search for the IP address 192.168.100.100.
The output should be written to a file named parsed_host.log.
The matching lines should be printed to the console.
Analysis of the options:
Option A: Correct IP regex used and correct output filename, but reads from parsed_host.log instead of a source log file like test_log.log (not ideal for initial parsing).
Option C: The IP address used is 192.168.100.101 instead of 192.168.100.100 --- incorrect.
Option D: Same IP address and logic as Option B, but uses print statement without parentheses, which is not valid in Python 3 unless using Python 2 --- not ideal.
Option B:
Uses correct IP: '192.168.100.100'
Reads from test_log.log (presumably the source log file).
Writes to output/parsed_host.log.
Prints each matching line and writes to output file --- satisfying all conditions.
ChatGPT said:
An engineer is analyzing a DoS attack and notices that the perpetrator used a different IP address to hide their system IP address and avoid detection. Which anti-forensics technique did the perpetrator use?
Answer : B
Using a different IP address to disguise the origin of an attack is the definition of IP spoofing.
''Spoofing involves falsifying data, such as IP or MAC addresses, to hide the source of malicious activity.'' --- Cisco CyberOps guide
An incident responder reviews a log entry that shows a Microsoft Word process initiating an outbound network connection followed by PowerShell execution with obfuscated commands. Considering the machine's role in a sensitive data department, what is the most critical action for the responder to take next to analyze this output for potential indicators of compromise?
Answer : C
When dealing with suspected malicious activity involving obfuscated PowerShell scripts---especially when launched from Microsoft Word documents---behavioral analysis is the most critical next step. This approach helps in determining if the process chain is part of a known attack pattern, such as a phishing attempt using malicious macros that launch PowerShell for data exfiltration or payload download.
As highlighted in the CyberOps Technologies (CBRFIR) 300-215 study guide, understanding behavior and deobfuscating PowerShell scripts is an essential part of the forensic and incident response process. Specifically:
During the detection and analysis phase, if PowerShell is used with obfuscated or encoded commands, responders should investigate the intent and behavior of the command.
Deobfuscation allows analysts to see what the script is doing (e.g., downloading files, creating persistence mechanisms, or opening a reverse shell).
The guide states:
''For example, if the threat is malware, the compromised system should be immediately isolated and the malware should be placed in a sandbox or a detonation chamber to understand what it is trying to do''.
This confirms that understanding execution behavior (such as what the PowerShell script intends to perform) is key to uncovering indicators of compromise (IoCs).
Thus, option C---conducting a behavioral analysis and deobfuscating PowerShell---is the most critical and effective response at this stage.
A threat actor has successfully attacked an organization and gained access to confidential files on a laptop. What plan should the organization initiate to contain the attack and prevent it from spreading to other network devices?
Answer : C
Once an incident has occurred, the appropriate course of action is to engage the organization's Incident Response (IR) plan. This is a structured approach to contain, analyze, and eradicate threats before they spread across the network.
The Cisco CyberOps Associate study guide emphasizes:
''Incident response and handling are essential within an organization... The main objective of implementing an incident handling process is to reduce the impact of a cyber-attack, ensure the damages caused are assessed, and implement recovery procedures''.
In particular, the containment phase of IR is focused on isolating the threat and preventing lateral movement or further compromise.
Options such as 'root cause' or 'attack surface' are relevant at later stages of analysis and mitigation, not immediate containment. Therefore, the correct answer is C.
Refer to the exhibit.
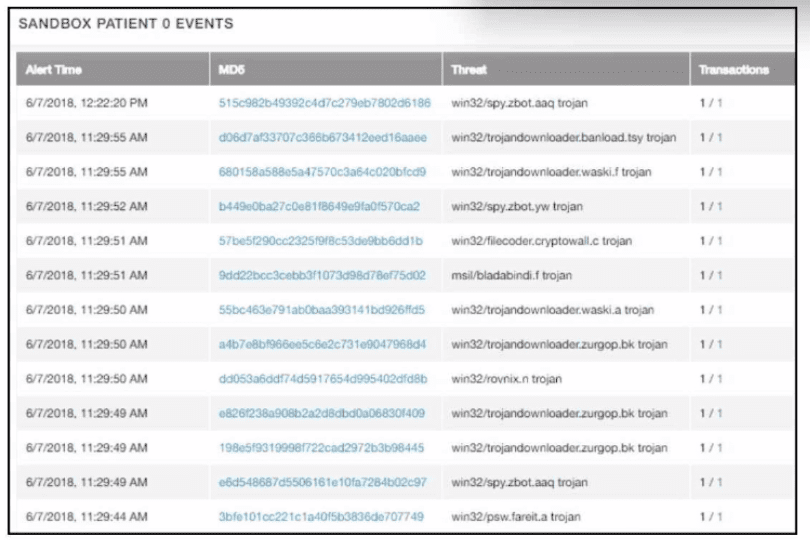
multiple machines behave abnormally. A sandbox analysis reveals malware. What must the administrator determine next?
Answer : D
The key goal during lateral movement analysis is to determine whether the malware spread or attempted to spread beyond the initially compromised system. This is crucial for containment and scoping of the incident. Logs, sandbox behavior, or network activity may show if Patient 0 initiated outbound connections to other systems, potentially propagating malware across the environment.
Correct answer: D. if Patient 0 tried to connect to another workstation.
In a secure government communication network, an automated alert indicates the presence of anomalous DLL files injected into the system memory during a routine update of communication protocols. These DLL files are exhibiting beaconing behavior to a satellite IP known for signal interception risks. Concurrently, there is an uptick in encrypted traffic volumes that suggests possible data exfiltration. Which set of actions should the security engineer prioritize?
Answer : A
In highly sensitive environments such as secure government networks, the presence of anomalous DLL injection, beaconing to known interception points, and signs of encrypted data exfiltration constitutes a critical incident. The appropriate response in such classified contexts involves:
Invoking a pre-established, classified incident response protocol,
Immediately notifying national cyber defense operatives (such as national CERT or military cyber command),
Prioritizing containment to stop lateral spread,
Proceeding with eradication of malware or backdoors.
This response sequence aligns with the high-severity, immediate-response model described in the Cisco CyberOps Associate v1.2 curriculum under national defense and classified incident frameworks. The study guide emphasizes the importance of stakeholder communication and multi-agency coordination during advanced persistent threat (APT) intrusions involving critical infrastructure or defense systems.
Refer to the exhibit.
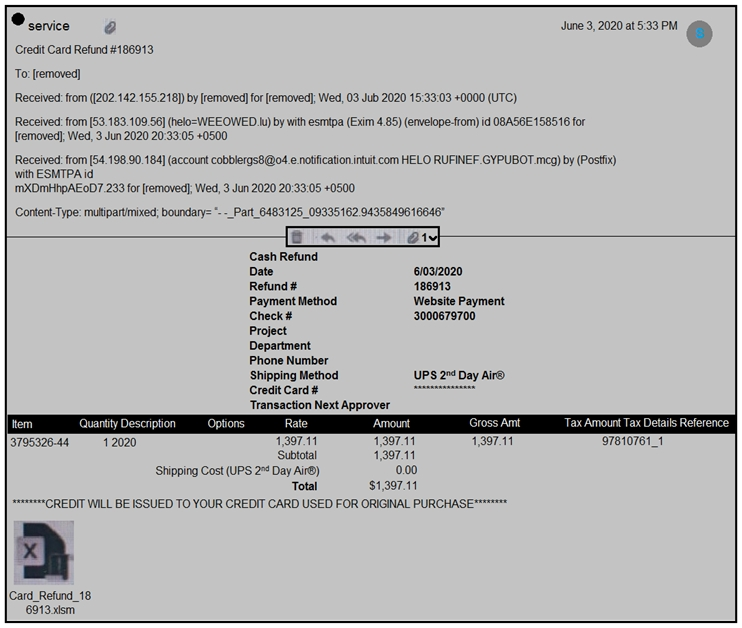
Which element in this email is an indicator of attack?
Answer : C
According to the Cisco Certified CyberOps Associate guide (Chapter 5 - Identifying Attack Methods), attachments in emails---especially with file extensions like .xlsm---are high-risk indicators when analyzing suspicious or phishing emails. Malicious actors often use macro-enabled Excel files (.xlsm) as a payload delivery mechanism for malware or other exploits. These attachments are typically disguised as legitimate content such as refunds or invoices to trick the recipient into opening them.
The presence of ''Card_Refund_18_6913.xlsm'' is a strong Indicator of Compromise (IoC), as .xlsm files can contain VBA macros capable of executing malicious code. This matches exactly with examples provided in the study material discussing how macro-based payloads are delivered and recognized.
Hence, option C is the most direct indicator of attack in this email.