Cisco Implementing and Operating Cisco Security Core Technologies 350-701 SCOR Exam Questions
[Security Concepts]
When network telemetry is implemented, what is important to be enabled across all network infrastructure devices to correlate different sources?
Answer : B
Network telemetry is the collection, measurement, and analysis of data related to the behavior and performance of a network1. It involves gathering information about routers, switches, servers, and applications to gain insights into how they function and how data moves through them. To correlate different sources of network telemetry data, it is important to enable Network Time Protocol (NTP) across all network infrastructure devices.NTP is a protocol that synchronizes the clocks of network devices to a common reference time source2. This ensures that the network telemetry data has consistent timestamps and can be compared and correlated accurately. NTP also helps with troubleshooting network issues, as it allows network administrators to pinpoint the exact time of events and anomalies.NTP is a core security technology that is covered in the Implementing and Operating Cisco Security Core Technologies (SCOR) course3, which helps you prepare for the Cisco CCNP Security and CCIE Security certifications and for senior-level security roles.Reference:1:Network Telemetry Explained: Frameworks, Applications & Standards - Splunk2:
[Network Time Protocol (NTP) - Cisco]3:Implementing and Operating Cisco Security Core Technologies (SCOR) v1.0
[Security Concepts]
Which API is used for Content Security?
Answer : D
Content Security is a term that encompasses various security features and solutions that protect the data and applications from threats such as malware, ransomware, phishing, data loss, and unauthorized access. Content Security includes products such as Cisco Email Security, Cisco Web Security, Cisco Cloudlock, and Cisco Umbrella. These products use the AsyncOS API, which is a RESTful API that allows administrators and developers to programmatically interact with the content security appliances and services. The AsyncOS API enables tasks such as configuration, reporting, monitoring, troubleshooting, and automation of content security policies and actions. The AsyncOS API is based on the HTTP protocol and uses JSON or XML as the data format. The AsyncOS API also supports authentication, authorization, rate limiting, and error handling mechanisms. The AsyncOS API documentation provides the details of the available resources, methods, parameters, and responses for each content security product.Reference:=
Cisco Content Security Products
AsyncOS API Overview
AsyncOS API Documentation
1: https://www.cisco.com/c/en/us/products/security/content-security/index.html2: https://www.cisco.com/c/en/us/td/docs/security/esa/esa13-0/API/b_ESA_API_13_0_1/b_ESA_API_13_0_1_chapter_01.html3: https://developer.cisco.com/docs/email-security/#!asyncos-api-overview
[Security Concepts]
With which components does a southbound API within a software-defined network architecture communicate?
Answer : D
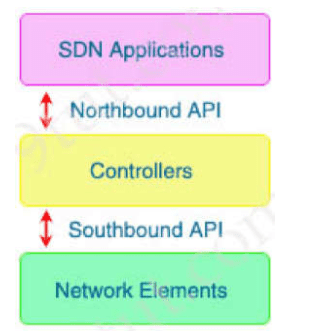
The Southbound API is used to communicate between Controllers and network devices.
[Security Operations]
What are two benefits of Flexible NetFlow records? (Choose two)
Answer : A, D
NetFlow is typically used for several key customer applications, including the following:
...
Billing and accounting. NetFlow data provides fine-grained metering (for instance, flow data includes details such as IP addresses, packet and byte counts, time stamps, type of service (ToS), and application ports) for highly flexible and detailed resource utilization accounting. Service providers may use the information for billing based on time of day, bandwidth usage, application usage, quality of service, and so on. Enterprise customers may use the information for departmental charge back or cost allocation for resource utilization.
[Security Concepts]
What is the default action before identifying the URL during HTTPS inspection in Cisco Secure Firewall Threat Defense software?
Answer : C
Before identifying the URL during HTTPS inspection in Cisco Secure Firewall Threat Defense software, the default action is to 'pass.' This means that the traffic is allowed through without inspection until the URL can be identified, at which point appropriate security policies can be applied based on the URL categorization and reputation.
[Security Concepts]
A company identified a phishing vulnerability during a pentest. What are two ways the company can protect employees from the attack? (Choose two.)
Answer : B, E
Refer to the exhibit.
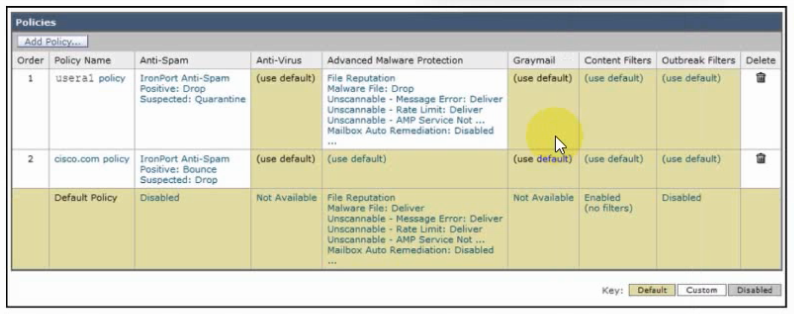
Refer to the exhibit. An engineer must configure an incoming mail policy so that each email sent from usera1@example.com to a domain of @cisco.com is scanned for antispam and advanced malware protection. All other settings will use the default behavior. What must be configured in the incoming mail policy to meet the requirements?
Answer : B