CIW v5 Database Design Specialist 1D0-541 Exam Questions
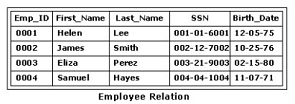
Consider the table for an employee database shown in the exhibit. What is the degree of the
table?

Answer : B
Which mechanism provides database users with controlled access to the database through the
use of virtual tables?
Answer : A
Which three pieces of information did E. F. Codd describe as necessary to retrieve a data value
from a relational database?
Answer : D
Consider the following SQL statement and the Orders relation shown in the exhibit:
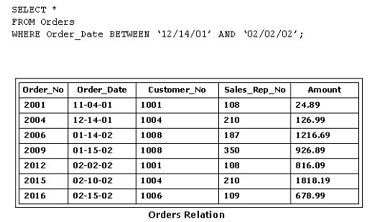
How many records should be returned?
Answer : C
Consider the following table as well as the Dept1_Parts and Dept2_Parts relations shown in
the exhibit:
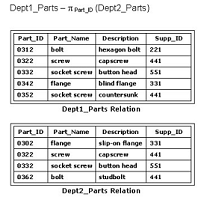
Which of the following relational algebraic expressions would result in the given table?
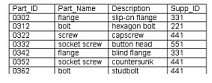
Answer : A
Consider the Orders relation shown in the exhibit. Which of the following SQL statements
would return all complete tuples for order dates in 2002, arranged by amount from lowest to
highest?
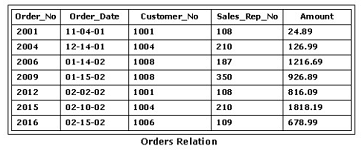
Answer : D
Consider the table for an employee database shown in the exhibit. What is the cardinality of
the table?
Answer : C