CIW Web Security Associate 1D0-571 Exam Questions
Irina has contracted with a company to provide Web design consulting services. The company has asked her to use several large files available via an HTTP server. The IT department has provided Irina with user name and password, as well as the DNS name of the HTTP server. She then used this information to obtain the files she needs to complete her task using Mozilla Firefox. Which of the following is a primary risk factor when authenticating with a standard HTTP server?
Answer : A
Consider the following image of a packet capture:
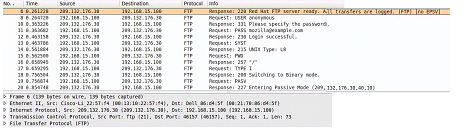
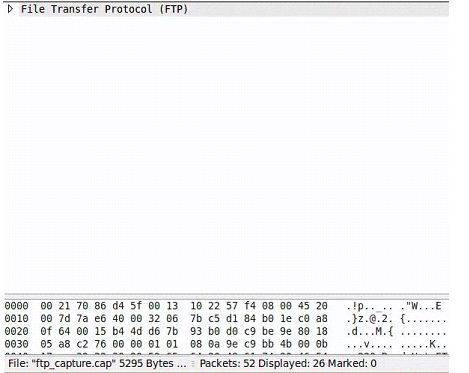
Which of the following best describes the protocol used, along with its primary benefit?
Answer : A
A new video conferencing device has been installed on the network. You have been assigned to troubleshoot a connectivity problem between remote workers and the central company. Specifically, remote workers are having problems making any connection at all. Which technique will most likely help you solve this problem while retaining the existing level of security at the firewall?
Answer : B
A distributed denial-of-service (DDOS) attack has occurred where both ICMP and TCP packets have crashed the company's Web server. Which of the following techniques will best help reduce the severity of this attack?
Answer : A
You have been asked to encrypt a large file using a secure encryption algorithm so you can send it via e-mail to your supervisor. Encryption speed is important. The key will not be transmitted across a network. Which form of encryption should you use?
Answer : D
Requests for Web-based resources have become unacceptably slow. You have been assigned to implement a solution that helps solve this problem. Which of the following would you recommend?
Answer : B
Which of the following activities is the most effective at keeping the actions of nae end users from putting the company's physical and logical. Which of the following activities is the most effective at keeping the actions of na?e end users from putting the company's physical and logical resources at risk?
Answer : B