CompTIA A+ Certification Exam: Core 2 220-1202 Exam Practice Test
A Windows 11 Home device is receiving constant pop-ups about an urgent need to update antivirus software to remove a detected threat. The user has been clicking the "X" button in the window frame but it always reappears. The pop-up includes an "OK" button to install the update and remove the threat. Which of the following should the user do next?
Answer : D
Comprehensive and Detailed Explanation From Exact Extract:
This is likely arogue antivirusor scareware tactic. The user shouldnot click 'OK'and instead check Windows Security (or third-party antivirus) status and ensure real-time protection is enabled.
FromMark Soper -- Mike Meyers' Lab Manual:
''Users should verify security center settings if receiving suspicious pop-ups. Clicking unknown software updates can install malware. It's safer to validate protection through legitimate system tools.''
SIMULATION
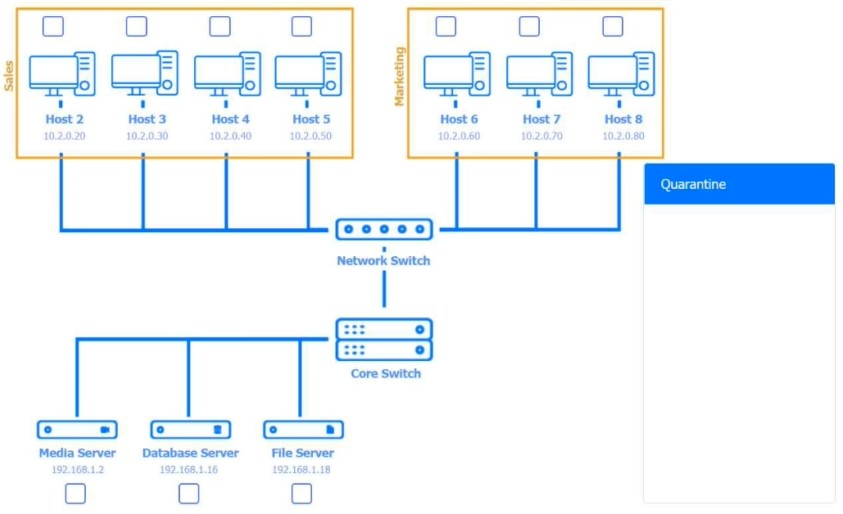
Multiple users are reporting audio issues as well as performance issues after downloading unauthorized software. You have been dispatched to identify and resolve any issues on the network using best practice procedures.
INSTRUCTIONS
Quarantine and configure the appropriate device(s) so that the users' audio issues are resolved using best practice procedures.
Multiple devices may be selected for quarantine.
Click on a host or server to configure services.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
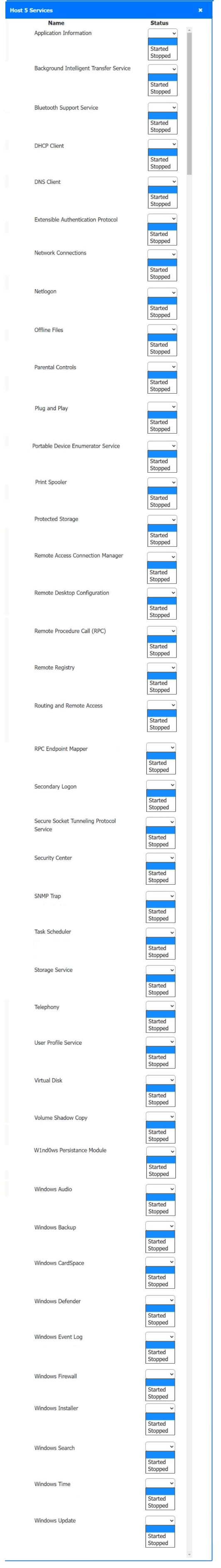






Answer : A
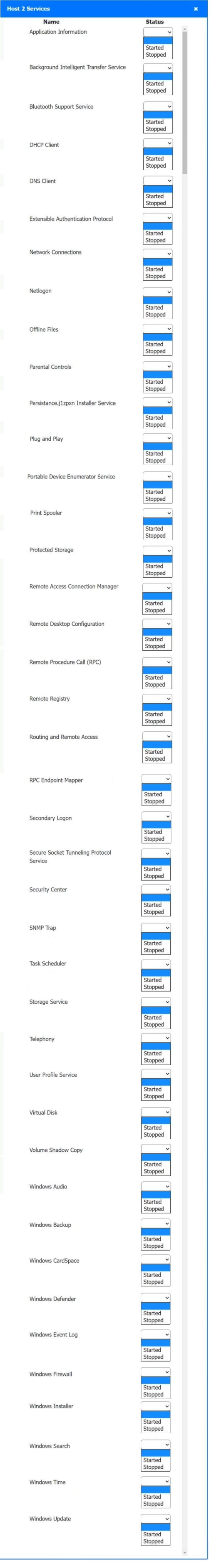
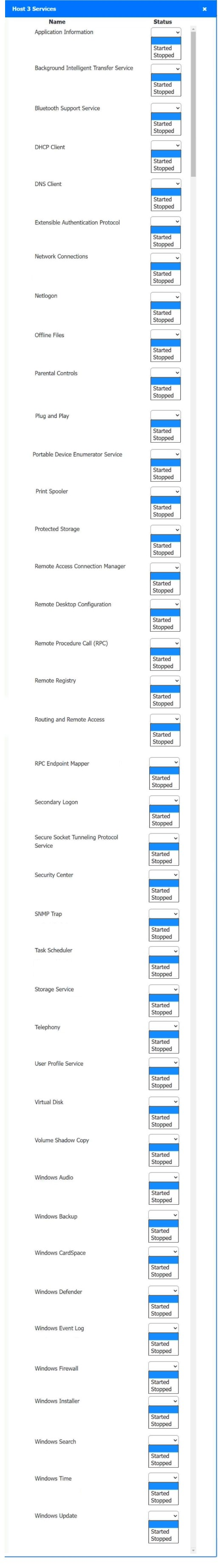
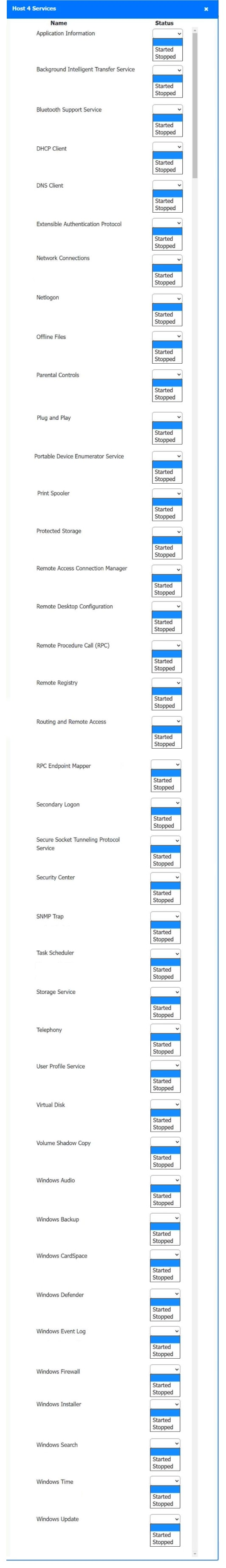
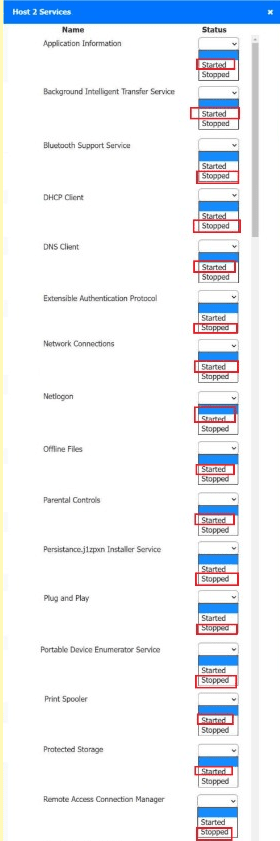
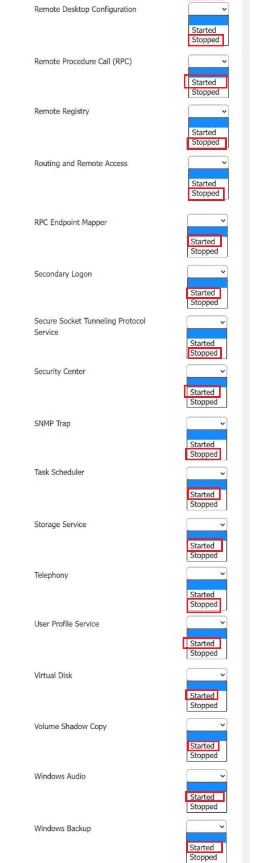
Host 2, Host 3, Host 4 , Host 5 ,Host 6, Host 7, Host 8 , Media Server - Stop All unwanted and malicious service (Persistance.j1zpxn Installer Service) from all the listed host and Media servers
Refer screenshot below on the required service started/stopped on host2, same service to be started and stopped across all host servers.
Users are reporting that an unsecured network is broadcasting with the same name as the normal wireless network. They are able to access the internet but cannot connect to the file share servers. Which of the following best describes this issue?
Answer : D
Comprehensive and Detailed Explanation From Exact Extract:
This scenario describes a rogue access point --- a malicious or unauthorized wireless access point that uses the same SSID as the legitimate network. Users may connect to it unknowingly, which can result in limited network access, data interception, or redirection of traffic. The inability to reach internal file servers supports this being an unauthorized AP with no connection to internal resources.
A . A DNS issue would impact name resolution, not connectivity to file servers directly.
B . VLAN issues generally affect segmentation, not mimic SSID problems.
C . An incorrect IP address could cause connectivity issues, but not in the presence of a malicious AP broadcasting the same SSID.
CompTIA A+ 220-1102 Objective 2.4: Compare and contrast wireless and physical security threats.
Study Guide Section: Rogue access points and their detection
===========================
A user logs in daily and cannot print a report. Help desk fixes it each day, but the issue recurs. What should be done so the issue doesn't recur? (Select two)
Answer : D, E
Comprehensive and Detailed Explanation From Exact Extract:
For persistent printing issues due to spooler service, ensure theprint spooler is started and set to Automatic. This maintains print capability across reboots.
FromMike Meyers' Lab Manual:
''If users lose printing capabilities on reboot, the print spooler service must be configured to start automatically and be confirmed as running.''
When a corporate laptop is connected to the company network, it can reach external websites. However, it cannot reach any internal websites, displaying the error message ''Cannot reach this page.'' Which of the following should a technician configure?
Answer : B
Comprehensive and Detailed Explanation From Exact Extract:
If internal resources (such as intranet or internal apps) can't be accessed but external sites work, this often points to aDNS issue, where the system isn't resolving internal domain names correctly.
FromAll-in-One Exam Guide:
''When internet access is functional but internal sites fail to load, the issue usually lies with DNS resolution. Internal resources often require internal DNS servers, which may not be configured correctly.''
An administrator must rename the administrator account on a Windows desktop. Which tool is best for this?
Answer : A
The Local Users and Groups Manager (lusrmgr.msc) is the utility for managing user accounts, including renaming the default Administrator.
From Quentin Docter -- Complete Study Guide:
''The lusrmgr.msc snap-in allows renaming and managing local user accounts, including the default administrator.'' .
A technician is securing a newly deployed workstation. Only authorized users should access it. Which actions should the technician take? (Select two)
Answer : C, F
Screensaver lockshelp protect unattended workstations.
BIOS passwordsprevent unauthorized changes at startup or during boot.
FromQUENTIN DOCTER - COMPTIA A+ COMPLETE study GUIDE:
''Applying a BIOS password adds a pre-boot security layer. Screensaver locks help protect logged-in sessions during idle times.''