CompTIA A+ Certification Exam: Core 2 220-1202 Practice Questions
A technician is 3-D printing high-strength, carbon fiber-based filament parts for a customer order. Which of the following is the most important for the technician to use?
Answer : B
Comprehensive and Detailed Explanation From Exact Extract:
Carbon fiber filamentcan producefine particles or fumesduring printing, which may be harmful when inhaled. Wearing anair filter maskis essential to protect the respiratory system.
FromQuentin Docter -- CompTIA A+ Complete Study Guide:
''When working with advanced materials like carbon fiber, always use appropriate personal protective equipment such as air filter masks to prevent inhalation of dangerous particles.''
A technician wants to prevent electrical damage while disassembling a device. The technician turns off the device. Which of the following should the technician do next?
Answer : D
The correct answer is D. Connect a wrist strap to a metal frame, because this action directly prevents electrostatic discharge (ESD), which is one of the most common causes of accidental hardware damage during device disassembly. Even when a device is powered off, static electricity stored in the technician's body can discharge into sensitive components such as RAM, CPUs, and system boards.
According to the Quentin Docter -- CompTIA A+ Complete Study Guide, the most effective way to prevent ESD is to equalize electrical potential between the technician and the device. An ESD wrist strap, when connected to a grounded metal surface such as a computer chassis, safely dissipates static electricity before it can damage components.
The Travis Everett & Andrew Hutz -- All-in-One Exam Guide explains that while antistatic mats and bags are useful, they are secondary controls. The wrist strap provides continuous grounding throughout the repair process, whereas mats and bags only protect components when they are placed on or inside them.
The Mike Meyers / Mark Soper Lab Manual reinforces that working on plastic surfaces does not guarantee grounding, and placing components in antistatic bags is something done after removal, not immediately after powering down.
Therefore, once the device is turned off, the next and most important step is to connect a wrist strap to a metal frame, making D the correct answer.
A town clerk wants to work from home and access documents on a town hall server. What should a technician set up?
Answer : C
AVPN (Virtual Private Network)creates a secure tunnel between the clerk's home device and the town server, ensuring private and authenticated access.
FromQuentin Docter -- CompTIA A+ Complete Study Guide:
''VPNs are essential for remote access to internal resources, providing secure connections over public networks.''
A secretary receives an email from the CEO requesting immediate vendor payment. Later, the CEO says they never sent it. Which social engineering tactic is this?
Answer : D
Comprehensive and Detailed Explanation From Exact Extract:
Spear phishingtargets a specific individual using personalized tactics, as seen in emails impersonating a CEO to deceive a secretary.
FromQUENTIN DOCTER - COMPTIA A+ COMPLETE study GUIDE:
''Spear phishing targets specific individuals or roles within an organization using tailored messages to increase success rates.''
A user is experiencing issues with outdated images while browsing websites. Which of the following settings should a technician use to correct this issue?
Answer : C
Comprehensive and Detailed Explanation From Exact Extract:
Outdated images and website data often result from cached files in the browser. The Internet Options panel in Windows (specifically under the General tab) allows users to clear browsing history, including cached images and files, which forces the browser to load the most current versions of web content.
A . Administrative Tools is used for advanced system management, not browser settings.
B . Windows Defender Firewall controls network traffic and security rules, not caching.
D . Ease of Access provides accessibility features for users with disabilities --- unrelated to web browsing issues.
CompTIA A+ 220-1102 Objective 3.3: Troubleshoot common software and application issues.
Study Guide Section: Internet Options and browser cache clearing for display issues
A technician is setting up a computer for a new user. A requirement is that the user's documents are stored on a network location and not locally on the computer. Which of the following should the technician configure?
Answer : D
The correct answer is D. Folder redirection, because folder redirection allows specific user folders---such as Documents, Desktop, and Downloads---to be stored on a network share rather than the local computer. This ensures centralized storage, easier backups, and improved data security.
According to the Quentin Docter -- CompTIA A+ Complete Study Guide, folder redirection is commonly used in domain environments to store user data on file servers. This prevents data loss if a workstation fails and allows users to access their files from multiple systems.
The Travis Everett & Andrew Hutz -- All-in-One Exam Guide explains that folder redirection works seamlessly with roaming profiles and Group Policy, ensuring that users do not need to manually save files to network drives.
The Mike Meyers / Mark Soper Lab Manual clarifies that file attributes only affect file behavior, UAC controls privilege elevation, and security groups control access permissions---but none of these determine where user folders are stored.
Because the requirement is to store documents on a network location instead of locally, configuring folder redirection is the correct and intended solution, making D the correct answer.
SIMULATION
Multiple users are reporting audio issues as well as performance issues after downloading unauthorized software. You have been dispatched to identify and resolve any issues on the network using best practice procedures.
INSTRUCTIONS
Quarantine and configure the appropriate device(s) so that the users' audio issues are resolved using best practice procedures.
Multiple devices may be selected for quarantine.
Click on a host or server to configure services.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
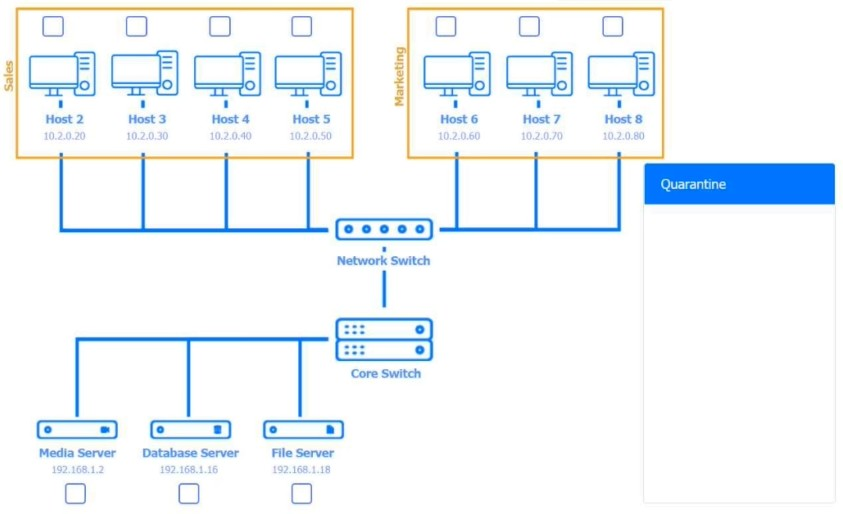
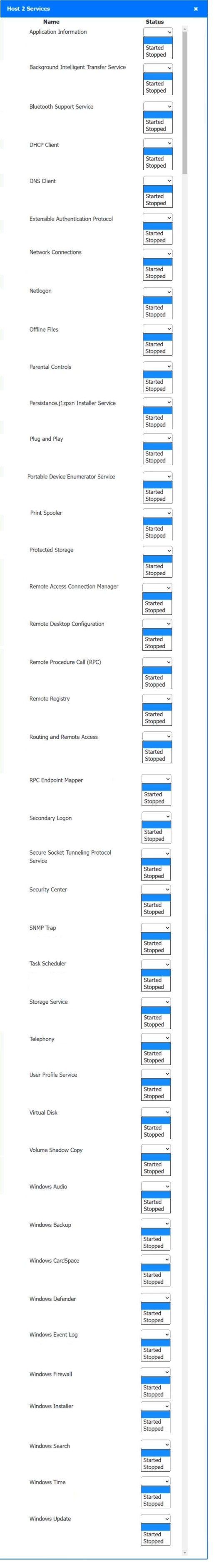
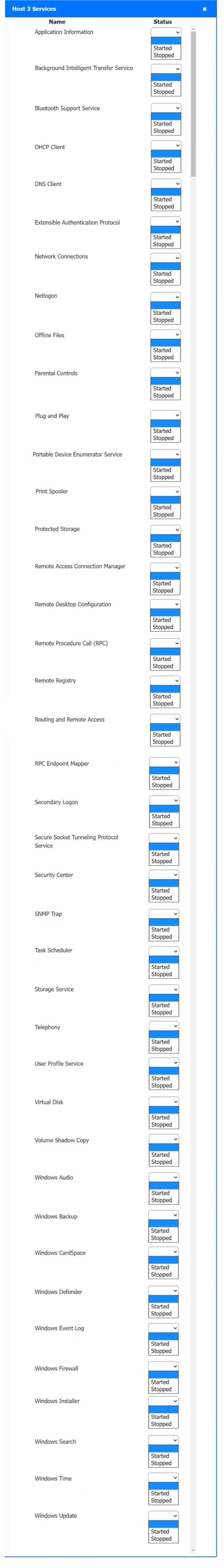
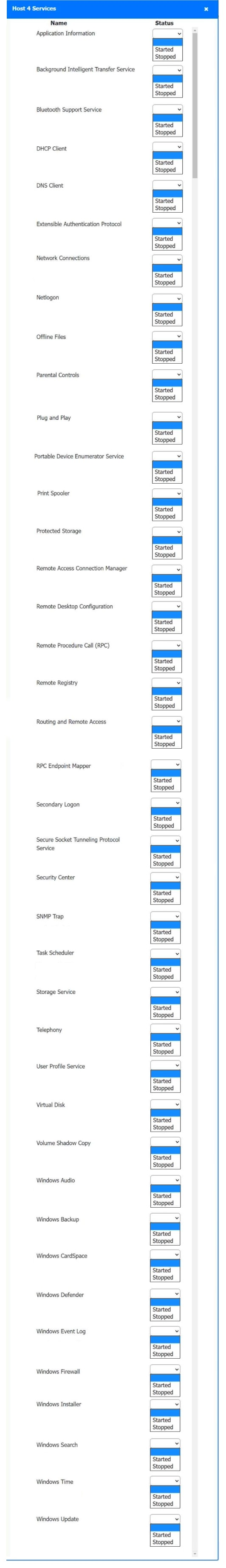






Answer : A
Host 2, Host 3, Host 4 , Host 5 ,Host 6, Host 7, Host 8 , Media Server - Stop All unwanted and malicious service (Persistance.j1zpxn Installer Service) from all the listed host and Media servers