CyberArk Defender Access ACCESS-DEF Exam Practice Test
A user's account information required for multi-factor authentication is not set up properly and is preventing the user from logging in.
What should you do?
Answer : A
Which protocols can CyberArk provide MFA for VPN? (Choose two.)
Answer : A, B
Where can MFA filters be used? (Choose three.)
Answer : A, B, D
Which dashboard can display the applications launched by users, the application type, and the number of times they were launched?
Answer : A
Refer to the exhibit.
This exhibit shows the base authentication policy for ACME Corporation. You must edit the policy to allow users to authenticate once if they fulfill certain authentication criteria.
How should you configure this policy to support BOTH?
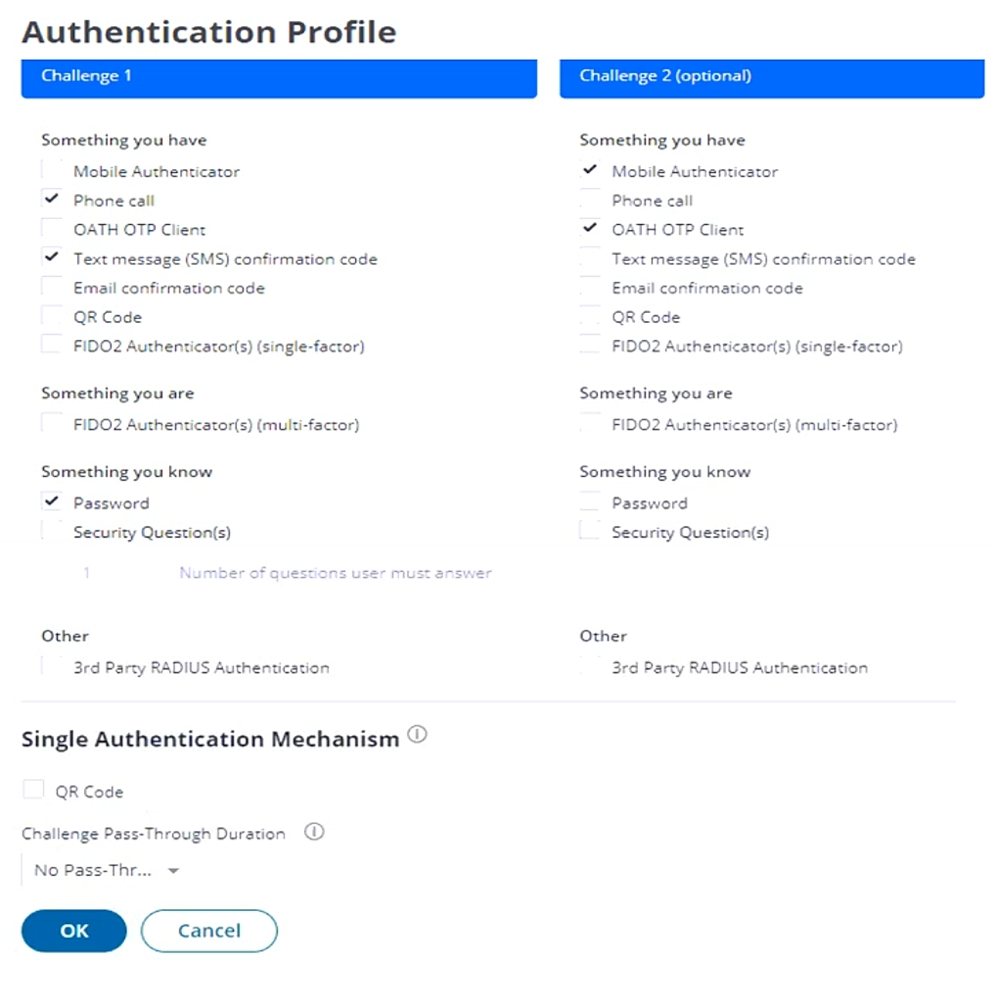
Answer : D
Your organization wants to implement passwordless authentication for business critical web applications. CyberArk Identity manages access to these applications.
What can you do to facilitate the enforcement of this passwordless authentication initiative? (Choose two.)
Answer : A, C
When logging on to the User Portal, which authentication methods can enable the user to bypass authentication rules and default profile? (Choose two.)
Answer : B, D