CyberArk Sentry - Privilege Cloud CPC-SEN Exam Practice Test
You are configuring firewall rules between the Privilege Cloud components and the Privilege Cloud. Which firewall rules should be set up to allow connections?
Answer : C
When configuring firewall rules for CyberArk Privilege Cloud, it is essential to allow bi-directional communication between the Privilege Cloud components and the CyberArk Privilege Cloud. This ensures that all necessary communications for operations and management can occur securely in both directions.
CyberArk documentation on system requirements for outbound traffic network and port requirements1.
CyberArk documentation on connecting to organization firewalls
How should you configure PSM for SSH to support load balancing?
Answer : A
To support load balancing for PSM for SSH, the configuration should be done by using a network load balancer. This method involves placing a network load balancer in front of multiple PSM for SSH servers to distribute incoming SSH traffic evenly among them. This setup enhances the availability and scalability of PSM for SSH by ensuring that no single server becomes a bottleneck, thereby improving performance and reliability during high usage scenarios.
What creating a new safe, what is the default number of password versions stored if using 'Save latest account versions' within version management settings?
Answer : B
When creating a new safe and configuring the 'Save latest account versions' within version management settings, the default number of password versions stored is 10. This setting allows the safe to maintain up to 10 past versions of each password managed within it. This capability is essential for ensuring that previous password states can be accessed if needed, such as for audit purposes or rollback scenarios in the event of an update error or compromise.
What is a supported certificate format for retrieving the LDAPS certificate when not using the Cyberark provided LDAPS certificate tool?
Answer : A
For retrieving the LDAPS certificate when not using the CyberArk provided LDAPS certificate tool, the supported certificate format is .der. The DER (Distinguished Encoding Rules) format is a binary form of a certificate rather than the ASCII PEM format. This format is widely supported across various systems for securing LDAP connections by providing a mechanism for LDAP servers to authenticate themselves to users. This information can be verified by checking LDAP configuration guides and CyberArk's secure implementation documentation which outline supported certificate formats for LDAP integrations.
Refer to the exhibit.
You set up your LDAP Directory in CyberArk Identity, but encountered an error during the connection test.
Which scenarios could represent a valid misconfiguration? (Choose 2.)
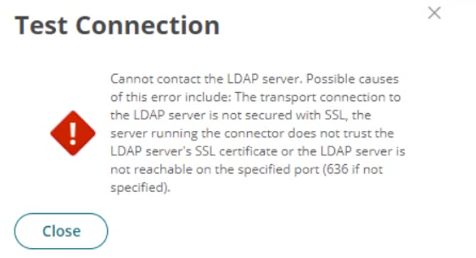
Answer : A, C
From the error message provided, two likely scenarios could represent valid misconfigurations:
TCP Port 636 could be blocked by a network firewall, preventing communication between the CyberArk Identity Connector and the LDAP Server (A). This is a common issue where firewall settings prevent the secure communication port (typically 636 for LDAPS) from transmitting data between the server and the connector, thus blocking the connection attempt.
'Verify Server Certificate' is activated but the provided hostname is not listed as a Subject Alternative Name (SAN) in the LDAP server's certificate (C). This scenario occurs when SSL/TLS security measures are stringent, requiring that the hostname used to connect to the LDAP server must match one listed in the server's SSL certificate. If the hostname does not match, the connection will fail due to SSL certificate validation errors.
You are planning to configure Multi-Factor Authentication (MFA) for your CyberArk Privilege Cloud Shared Service. What are the available authentication methods?
Answer : B
In CyberArk Privilege Cloud, Multi-Factor Authentication (MFA) can be configured to enhance security by requiring multiple methods of authentication from independent categories of credentials to verify the user's identity. The available authentication methods include:
Windows Authentication: Leverages the user's Windows credentials.
PKI (Public Key Infrastructure): Utilizes certificates to authenticate.
RADIUS (Remote Authentication Dial-In User Service): A networking protocol that provides centralized Authentication, Authorization, and Accounting management.
CyberArk: Uses CyberArk's own authentication methods.
LDAP (Lightweight Directory Access Protocol): Protocol for accessing and maintaining distributed directory information services.
SAML (Security Assertion Markup Language): An open standard that allows identity providers to pass authorization credentials to service providers.
OpenID Connect (OIDC): An authentication layer on top of OAuth 2.0, an authorization framework.
Reference for this can be found in the CyberArk Privilege Cloud documentation, which details the integration and setup of MFA using these methods.
During CPM hardening, which locally created users are granted Logon as a Service rights in the local group policy? (Choose 2.)
Answer : A, D
During the Central Policy Manager (CPM) hardening process, the locally created users that are granted 'Logon as a Service' rights in the local group policy are typically PasswordManager and PasswordManagerUser. These accounts are crucial for the CPM's operation as they handle password management tasks and require the ability to log on as a service to perform their functions effectively. This configuration is established to ensure that these service accounts can operate under service control manager without interruption, which is critical for automated password rotations and other security processes managed by the CPM. This detail is typically outlined in the CyberArk CPM installation and configuration guide.