Eccouncil Certified Cybersecurity Technician (CCT) 212-82 Exam Questions
Jane Is a newly appointed Chief Financial Officer at BigTech Corp. Within a week, she receives an email from a sender posing as the company's CEO. instructing her to make an urgent wire transfer. Suspicious. Jane decides to verify the request's authenticity. She receives another email from the same sender, now attaching a seemingly scanned Image of the CEO's handwritten note. Simultaneously, she gets a call from an 'IT support' representative, instructing her to click on the attached image to download a 'security patch'. Concerned. Jane must determine which social engineering tactics she encountered.
Answer : D
Jane encountered a combination of social engineering tactics:
Spear Phishing:
CEO Impersonation Email: The initial email and the follow-up with the scanned image of the CEO's handwritten note are examples of spear phishing, where attackers target specific individuals with tailored messages to gain their trust and extract sensitive information.
Vishing:
'IT Support' Call: The phone call from the supposed 'IT support' representative asking Jane to download a 'security patch' is a form of vishing (voice phishing). This tactic involves using phone calls to trick victims into revealing sensitive information or performing actions that compromise security.
Social Engineering Techniques: SANS Institute Reading Room
Phishing and Vishing Explained: Norton Security
Walker, a security team member at an organization, was instructed to check if a deployed cloud service is working as expected. He performed an independent examination of cloud service controls to verify adherence to standards through a review of objective evidence. Further, Walker evaluated the services provided by the CSP regarding security controls, privacy impact, and performance.
Identify the role played by Walker in the above scenario.
You work in a Multinational Company named Vector Inc. on Hypervisors and Virtualization Software. You are using the Operating System (OS) Virtualization and you have to handle the Security risks associated with the OS virtualization. How can you mitigate these security risks?
Answer : A
Mitigating security risks associated with OS virtualization involves a comprehensive approach. Here's a breakdown of the steps:
Implement Least Privilege Access Control for Users Managing VMs:
Limit access to only those users who need it.
Ensure that users have only the permissions necessary to perform their tasks.
Regularly Patch and Update the Hypervisor Software for Security Fixes:
Keep the hypervisor and virtualization software up-to-date to protect against known vulnerabilities.
Regular patching minimizes the risk of exploitation.
Disable Security Features on Virtual Machines to Improve Performance:
Note: This is actually a security risk. The correct approach is to enable and configure security features to protect VMs, despite the potential minor impact on performance.
Comprehensive Approach:
A holistic security strategy includes enforcing least privilege, maintaining updated systems, and enabling security features on VMs to protect against a wide range of threats.
EC-Council Certified Ethical Hacker (CEH) materials.
Best practices for virtualization security from NIST and other cybersecurity frameworks.
A text file containing sensitive information about the organization has been leaked and modified to bring down the reputation of the organization. As a safety measure, the organization did contain the MD5 hash of the original file. The file which has been leaked is retained for examining the integrity. A file named "Sensitiveinfo.txt" along with OriginalFileHash.txt has been stored in a folder named Hash in Documents of Attacker Machine-1. Compare the hash value of the original file with the leaked file and state whether the file has been modified or not by selecting yes or no.
Answer : B
Yes is the answer to whether the file has been modified or not in the above scenario. A hash is a fixed-length string that is generated by applying a mathematical function, called a hash function, to a piece of data, such as a file or a message. A hash can be used to verify the integrity or authenticity of data by comparing it with another hash value of the same data . A hash value is unique and any change in the data will result in a different hash value . To compare the hash value of the original file with the leaked file and state whether the file has been modified or not, one has to follow these steps:
Navigate to Hash folder in Documents of Attacker-1 machine.
Open OriginalFileHash.txt file with a text editor.
Note down the MD5 hash value of the original file as 8f14e45fceea167a5a36dedd4bea2543
Open Command Prompt and change directory to Hash folder using cd command.
Type certutil -hashfile Sensitiveinfo.txt MD5 and press Enter key to generate MD5 hash value of leaked file.
Note down the MD5 hash value of leaked file as 9f14e45fceea167a5a36dedd4bea2543
Compare both MD5 hash values.
The MD5 hash values are different , which means that the file has been modified.
Kason, a forensic officer, was appointed to investigate a case where a threat actor has bullied certain children online. Before proceeding legally with the case, Kason has documented all the supporting documents, including source of the evidence and its relevance to the case, before presenting it in front of the jury.
Which of the following rules of evidence was discussed in the above scenario?
Answer : D
Admissible is the rule of evidence discussed in the above scenario. A rule of evidence is a criterion or principle that determines whether a piece of evidence can be used in a legal proceeding or investigation. Admissible is a rule of evidence that states that the evidence must be relevant, reliable, authentic, and understandable to be accepted by a court or a jury . Admissible also means that the evidence must be obtained legally and ethically, without violating any laws or rights. In the scenario, Kason has documented all the supporting documents, including source of the evidence and its relevance to the case, before presenting it in front of the jury, which means that he has followed the admissible rule of evidence. Authentic is a rule of evidence that states that the evidence must be original or verifiable as genuine and not altered or tampered with. Understandable is a rule of evidence that states that the evidence must be clear and comprehensible to the court or jury and not ambiguous or confusing. Reliable is a rule of evidence that states that the evidence must be consistent and trustworthy and not based on hearsay or speculation.
A web application www.movieabc.com was found to be prone to SQL injection attack. You are given a task to exploit the web application and fetch the user credentials. Select the UID which is mapped to user john in the database table.
Note:
Username: sam
Pass: test
Answer : D
4 is the UID that is mapped to user john in the database table in the above scenario. SQL injection is a type of web application attack that exploits a vulnerability in a web application that allows an attacker to inject malicious SQL statements into an input field, such as a username or password field, and execute them on the database server. SQL injection can be used to bypass authentication, access or modify sensitive data, execute commands, etc. To exploit the web application and fetch the user credentials, one has to follow these steps:
Open a web browser and type www.movieabc.com
Press Enter key to access the web application.
Enter sam as username and test as password.
Click on Login button.
Observe that a welcome message with username sam is displayed.
Click on Logout button.
Enter sam' or '1'='1 as username and test as password.
Click on Login button.
Observe that a welcome message with username admin is displayed, indicating that SQL injection was successful.
Click on Logout button.
Enter sam'; SELECT * FROM users; -- as username and test as password.
Click on Login button.
Observe that an error message with user credentials from users table is displayed.
The user credentials from users table are:
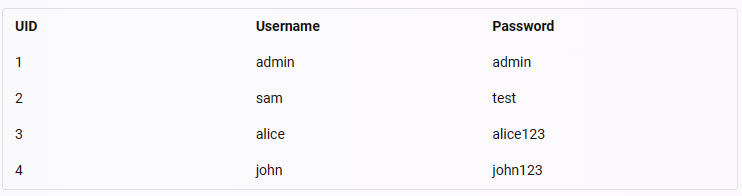
The UID that is mapped to user john is 4.
A pfSense firewall has been configured to block a web application www.abchacker.com. Perform an analysis on the rules set by the admin and select the protocol which has been used to apply the rule.
Hint: Firewall login credentials are given below:
Username: admin
Password: admin@l23
Answer : B
TCP/UDP is the protocol that has been used to apply the rule to block the web application www.abchacker.com in the above scenario. pfSense is a firewall and router software that can be installed on a computer or a device to protect a network from various threats and attacks. pfSense can be configured to block or allow traffic based on various criteria, such as source, destination, port, protocol, etc. pfSense rules are applied to traffic in the order they appear in the firewall configuration . To perform an analysis on the rules set by the admin, one has to follow these steps:
Open a web browser and type 20.20.10.26
Press Enter key to access the pfSense web interface.
Enter admin as username and admin@l23 as password.
Click on Login button.
Click on Firewall menu and select Rules option.
Click on LAN tab and observe the rules applied to LAN interface.
The rules applied to LAN interface are:
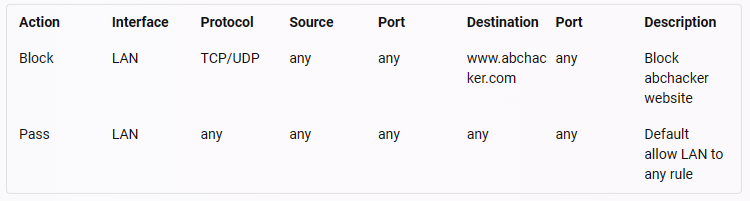
The first rule blocks any traffic from LAN interface to www.abchacker.com website using TCP/UDP protocol. The second rule allows any traffic from LAN interface to any destination using any protocol. Since the first rule appears before the second rule, it has higher priority and will be applied first. Therefore, TCP/UDP is the protocol that has been used to apply the rule to block the web application www.abchacker.com. POP3 (Post Office Protocol 3) is a protocol that allows downloading emails from a mail server to a client device. FTP (File Transfer Protocol) is a protocol that allows transferring files between a client and a server over a network. ARP (Address Resolution Protocol) is a protocol that resolves IP addresses to MAC (Media Access Control) addresses on a network.