Eccouncil Certified SOC Analyst 312-39 Exam Practice Test
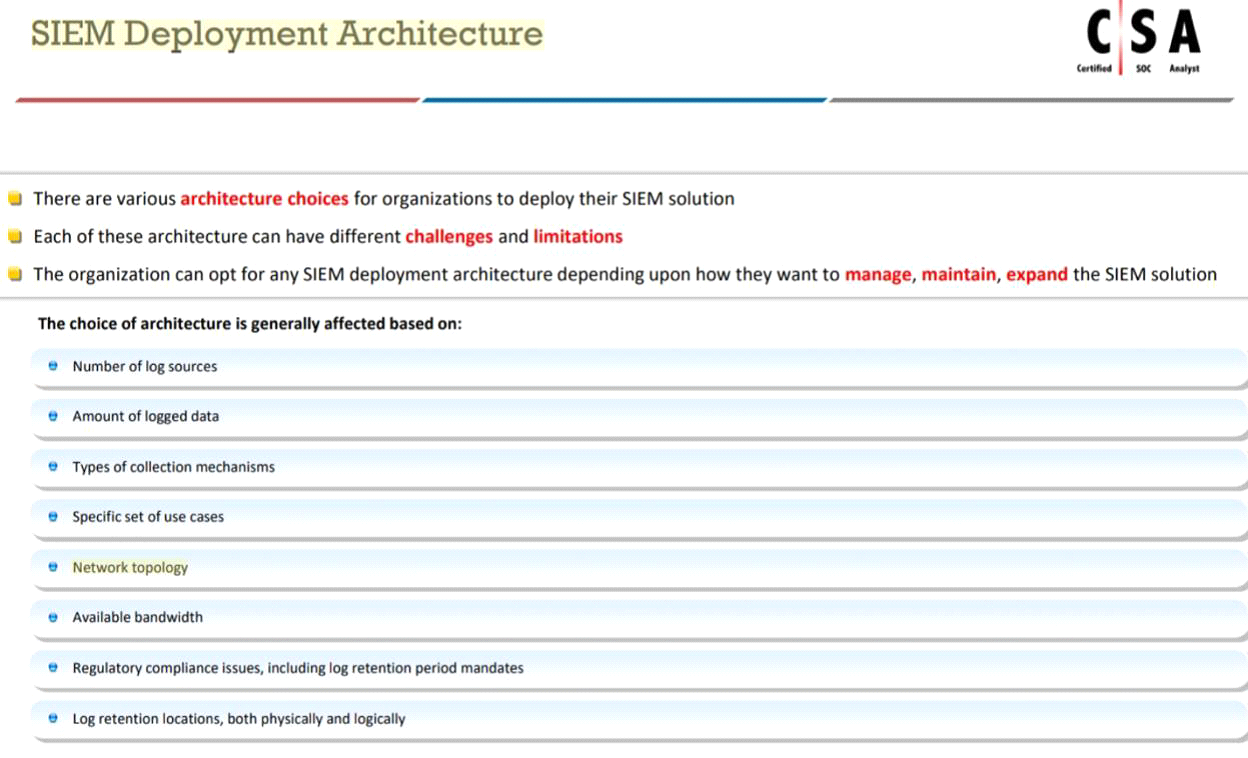
Which of the following factors determine the choice of SIEM architecture?
Answer : D
Which of the following service provides phishing protection and content filtering to manage the Internet experience on and off your network with the acceptable use or compliance policies?
Answer : C
Peter, a SOC analyst with Spade Systems, is monitoring and analyzing the router logs of the company and wanted to check the logs that are generated by access control list numbered 210.
What filter should Peter add to the 'show logging' command to get the required output?
Answer : C
Identify the event severity level in Windows logs for the events that are not necessarily significant, but may indicate a possible future problem.
Answer : B
Which of the following command is used to view iptables logs on Ubuntu and Debian distributions?
Answer : B
Which of the following technique involves scanning the headers of IP packets leaving a network to make sure
that the unauthorized or malicious traffic never leaves the internal network?
Answer : A
Chloe, a SOC analyst with Jake Tech, is checking Linux systems logs. She is investigating files at /var/log/ wtmp.
What Chloe is looking at?
Answer : D