Eccouncil Certified Application Security Engineer (CASE) JAVA 312-96 Exam Practice Test
Which line of the following example of Java Code can make application vulnerable to a session attack?

Answer : B
A US-based ecommerce company has developed their website www.ec-sell.com to sell their products online. The website has a feature that allows their customer to search products based on the price. Recently, a bug bounty has discovered a security flaw in the Search page of the website, where he could see all products from the database table when he altered the website URL http://www.ec-sell.com/products.jsp?val=100 to http://www.ec-sell.com/products.jsp?val=200 OR '1'='1 -. The product.jsp page is vulnerable to
Answer : C
Which of the following state management method works only for a sequence of dynamically generated forms?
Answer : C
During his secure code review, John, an independent application security expert, found that the developer has used Java code as highlighted in the following screenshot. Identify the security mistake committed by the developer?
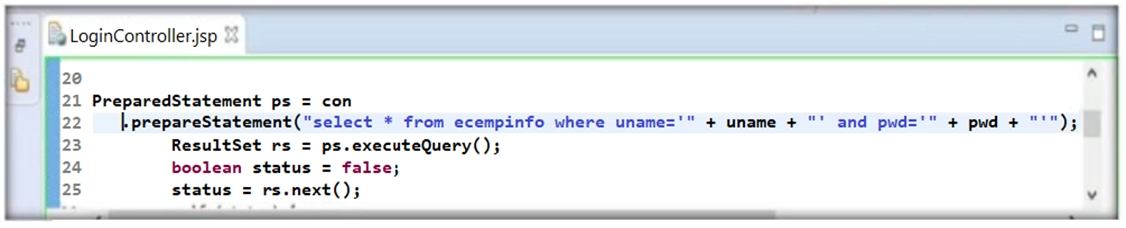
Answer : B
Oliver is a web server admin and wants to configure the Tomcat server in such a way that it should not serve index pages in the absence of welcome files. Which of the following settings in CATALINA_HOME/conf/ in web.xml will solve his problem?
Answer : B
Which of the following elements in web.xml file ensures that cookies will be transmitted over an encrypted channel?
Answer : D
Alice works as a Java developer in Fygo software Services Ltd. He is given the responsibility to design a bookstore website for one of their clients. This website is supposed to store articles in .pdf format. Alice is advised by his superior to design ArticlesList.jsp page in such a way that it should display a list of all the articles in one page and should send a selected filename as a query string to redirect users to articledetails.jsp page.
Alice wrote the following code on page load to read the file name.
String myfilename = request.getParameter("filename");
String txtFileNameVariable = myfilename;
String locationVariable = request.getServletContext().getRealPath("/");
String PathVariable = "";
PathVariable = locationVariable + txtFileNameVariable;
BufferedInputStream bufferedInputStream = null;
Path filepath = Paths.get(PathVariable);
After reviewing this code, his superior pointed out the security mistake in the code and instructed him not repeat the same in future. Can you point the type of vulnerability that may exist in the above code?
Answer : D