Eccouncil Certified Security Analyst (ECSA) v10 ECSAv10 ECSA v10 Exam Questions
Which of the following attributes has a LM and NTLMv1 value as 64bit + 64bit + 64bit and NTLMv2 value as 128 bits?
Answer : B
Which of the following statement holds true for TCP Operation?
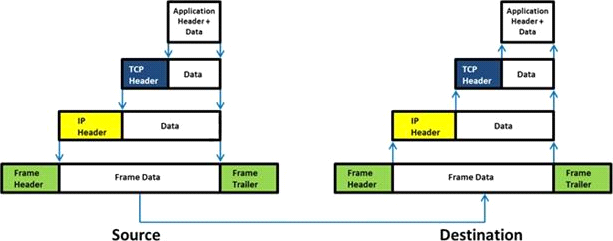
Answer : D
How many bits is Source Port Number in TCP Header packet?
Answer : D
Why is a legal agreement important to have before launching a penetration test?
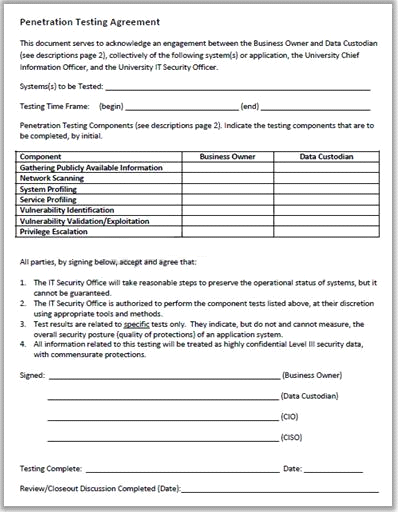
Answer : C
In which of the following IDS evasion techniques does IDS reject the packets that an end system accepts?
Answer : D
Identify the person who will lead the penetration-testing project and be the client point of contact.
Answer : C
Identify the framework that comprises of five levels to guide agency assessment of their security programs and assist in prioritizing efforts for improvement:
Answer : D