F5 Networks TMOS Administration 201 Exam Practice Test
A BIG-IP Administrator defines a device Self IP . The Self IP is NOT reachable from the network. What should the BIG-IP Administrator verify first?
Answer : B
Refer of the exhibit.
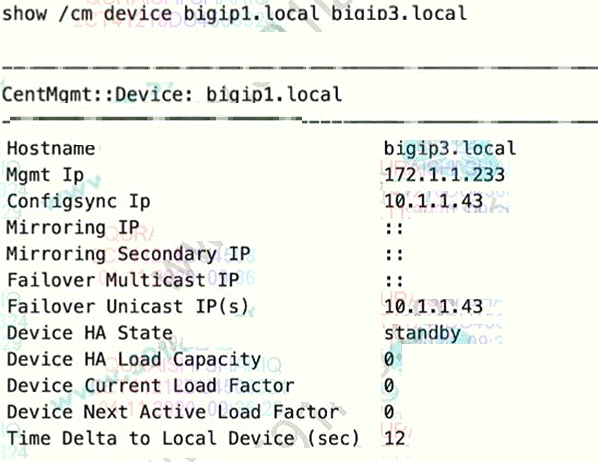
The 816-IP Administrator runs the command shown and observes a device trust issue between BIG-IP
devices in a device group. The issue prevents config sync on device bigip3.local.
What is preventing the config sync?
Answer : A
Option A should be bioip3.local?. if choose bigip3.local, you should choose A.
A BIG-IP Administrator suspects that one of the BIG-IP device power supplies is experiencing power
outages.
Which log file should the BIG-IP Administrator check to verify the suspicion?
Answer : C
A BIG-IP has a virtual server at 150.150.10.10:80 with SNAT automap configured. This BIG-IP also has a SNAT at 150.150.10.11 set for a source address range of 200.200.1.0 / 255.255.255.0. All other settings are at
their default states. If a client with the IP address 200.200.1.1 sends a request to the virtual server, what is the source IP address when the associated packet is sent to the pool member?
Answer : C
A BIG-IP Administrator wants to add the ASM Module to an HA pair of BIG-IP devices. The BIG-IP Administrator has already installed a new Add-On License on both devices in the HA pair. What should the BIG-IP Administrator do next to use the module?
Answer : A
Refer to the exhibit.

During a planned upgrade lo a BIG-IP HA pair running Active/Standby, an outage to application traffic is reported shortly after the Active unit is forced to Standby Reverting the flower resolves the outage. What should the BIG-IP Administrator modify to avoid an outage during the next for over event?
Answer : A
A BIG-IP Administrator creates a new VLAN on BIG-IP Cluster Member A and attaches an Interface to it. Although the Auto Config Sync is in place, the new VLAN does NOT show up on Cluster Member B. What should the BIG-IP Administrator do to ensure the new VLAN is configured on each Cluster Member?
Answer : A