Fortinet FCP - FortiAnalyzer 7.4 Administrator FCP_FAZ_AD-7.4 Exam Practice Test
Which two statement are true regardless initial Logs sync and Log Data Sync for Ha on FortiAnalyzer?
Answer : B, C
Which two statements are true regarding FortiAnalyzer log forwarding? (Choose two.)
Answer : A, C
A) FortiAnalyzer_7.0_Study_Guide-Online.pdf page 148: The log communication between devices can be protected by encryption, with the desired encryption level, using the commands shown on the slide. (You need to interpret this. 'Real time' and 'aggregation' is about the 'moment' when Fortigate sends the logs. However, no matter the moment, Fortigate will upload logs encrypted or unencrypted based on previous / differente config).
C) FortiAnalyzer_7.0_Study_Guide-Online.pdf page 147: Aggregation: Logs and content files stored and uploaded at scheduled time.
What is the purpose of the following CLI command?
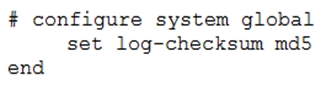
Answer : A
https://docs2.fortinet.com/document/fortianalyzer/6.0.3/cli-reference/849211/global
FortiAnalyzer reports are dropping analytical data from 15 days ago, even though the data policy setting for
analytics logs is 60 days.
What is the most likely problem?
Answer : B
Which process caches logs on FortiGate when FortiAnalyzer is not reachable?
Answer : B
What statements are true regarding disk log quota? (Choose two)
Answer : C, D
What is the purpose of employing RAID with FortiAnalyzer?
Answer : A
https://en.wikipedia.org/wiki/RAID#:~:text=RAID%20(%22Redundant%20Array%20of%20Inexpensive,%2C%20performance%20improvement%2C%20or%20both.