Fortinet FCP - FortiClient EMS 7.2 Administrator FCP_FCT_AD-7.2 Exam Practice Test
What does FortiClient do as a fabric agent? (Choose two.)
Answer : C, D
Which statement about FortiClient comprehensive endpoint protection is true?
Answer : D
FortiClient provides comprehensive endpoint protection for your Windows-based, Mac-based, and Linuxbased desktops, laptops, file servers, and mobile devices such as iOS and Android. It helps you to safeguard your systems with advanced security technologies, all of which you can manage from a single management console.
Refer to the exhibit, which shows the Zero Trust Tagging Rule Set configuration.
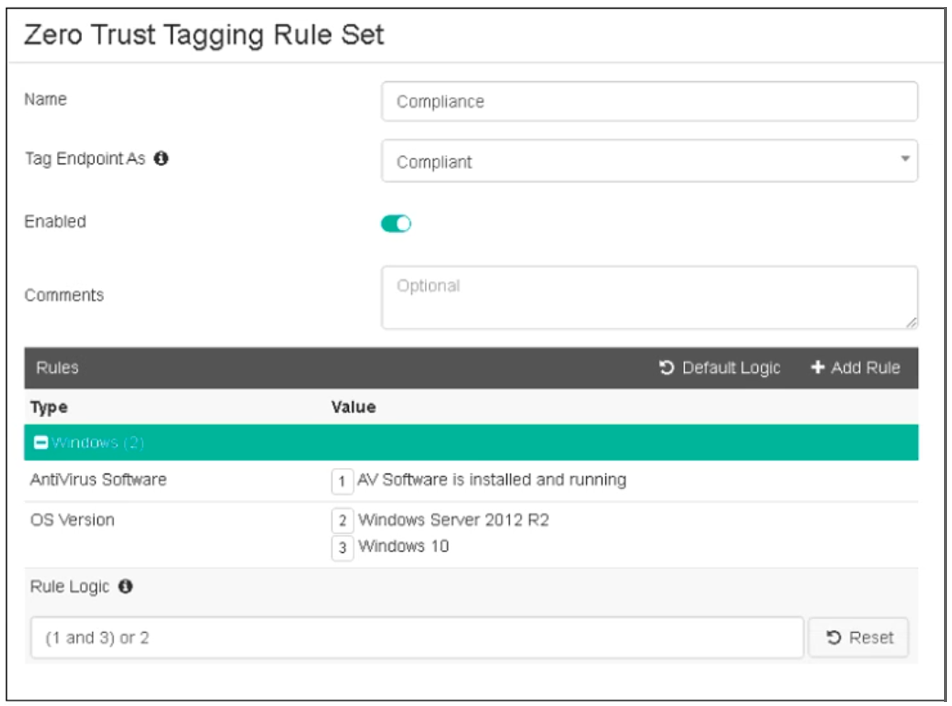
Which two statements about the rule set are true? (Choose two.)
Answer : C, D
Based on the Zero Trust Tagging Rule Set configuration shown in the exhibit:
The rule set includes two conditions:
AV Software is installed and running
OS Version is Windows Server 2012 R2 or Windows 10
The Rule Logic is specified as '(1 and 3) or 2,' meaning:
The endpoint must have antivirus software installed and running and must be running Windows 10.
Alternatively, the endpoint must be running Windows Server 2012 R2.
Therefore, the endpoint must satisfy either:
Antivirus is installed and running and Windows 10 is running.
Windows Server 2012 R2 is running.
Reference
FortiClient EMS 7.2 Study Guide, Zero Trust Tagging Rule Set Configuration Section
Fortinet Documentation on Configuring Zero Trust Tagging Rules and Logic
Which security fabric component sends a notification io quarantine an endpoint after IOC detection "n the automation process?
Answer : C
Understanding the Automation Process:
In the Security Fabric, automation processes can include actions such as quarantining an endpoint after an IOC (Indicator of Compromise) detection.
Evaluating Responsibilities:
FortiClient EMS plays a crucial role in endpoint management and can send notifications to quarantine endpoints.
Conclusion:
The correct security fabric component that sends a notification to quarantine an endpoint after IOC detection is FortiClient EMS.
FortiClient EMS and automation process documentation from the study guides.
Exhibit.
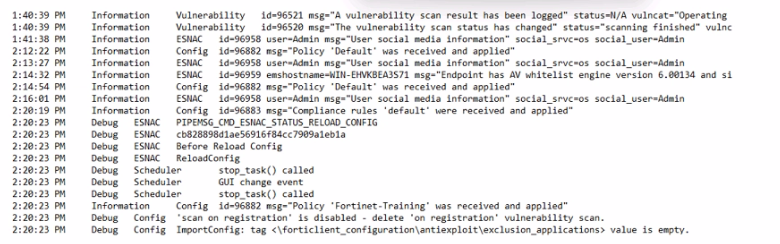
Based on the FortiClient logs shown in the exhibit, which endpoint profile policy is currently applied lo the ForliClient endpoint from the EMS server?
Answer : A
Observation of Logs:
The logs show a policy named 'Fortinet-Training' being applied to the endpoint.
Evaluating Policies:
The log entries indicate that the 'Fortinet-Training' policy was received and applied.
Conclusion:
Based on the logs, the currently applied policy on the FortiClient endpoint is 'Fortinet-Training'.
FortiClient EMS policy configuration and log analysis documentation from the study guides.
Which two VPN types can a FortiClient endpoint user inmate from the Windows command prompt? (Choose two)
Answer : C, D
FortiClient supports initiating the following VPN types from the Windows command prompt:
IPSec VPN: FortiClient can establish IPSec VPN connections using command line instructions.
SSL VPN: FortiClient also supports initiating SSL VPN connections from the Windows command prompt.
These two VPN types can be configured and initiated using specific command line parameters provided by FortiClient.
Reference
FortiClient EMS 7.2 Study Guide, VPN Configuration Section
Fortinet Documentation on Command Line Options for FortiClient VPN
Which three types of antivirus scans are available on FortiClient? (Choose three )
Answer : B, C, E
FortiClient offers several types of antivirus scans to ensure comprehensive protection:
Full scan: Scans the entire system for malware, including all files and directories.
Custom scan: Allows the user to specify particular files, directories, or drives to be scanned.
Quick scan: Scans the most commonly infected areas of the system, providing a faster scanning option.
These three types of scans provide flexibility and thoroughness in detecting and managing malware threats.
Reference
FortiClient EMS 7.2 Study Guide, Antivirus Scanning Options Section
Fortinet Documentation on Types of Antivirus Scans in FortiClient