Fortinet FCP - FortiGate 7.4 Administrator FCP_FGT_AD-7.4 Exam Practice Test
When FortiGate performs SSL/SSH full inspection, you can decide how it should react when it detects an invalid certificate.
Which three actions are valid actions that FortiGate can perform when it detects an invalid certificate? (Choose three.)
Answer : B, C, E
When a certificate fails for any of the reasons above, you can configure any of the following actions: * Keep untrusted & Allow: FortiGate allows the website and lets the browser decide the action to take. FortiGate takes the certificate as untrusted. * Block: FortiGate blocks the content of the site. * Trust & Allow: FortiGate allows the website and takes the certificate as trusted.
Which statement about the deployment of the Security Fabric in a multi-VDOM environment is true?
Answer : C
'When you configure FortiGate devices in multi-vdom mode and add them to the Security Fabric, each VDOM with its assigned ports is displayed when one or more devices are detected. Only the ports with discovered and connected devices appear in the Security Fabric view and, because of this, you must enable Device Detection on ports you want to have displayed in the Security Fabric. VDOMs without ports with connected devices are not displayed. All VDOMs configured must be part of a single Security Fabric.'
Which statement is a characteristic of automation stitches?
A FortiGate firewall policy is configured with active authentication however, the user cannot authenticate when accessing a website.
Which protocol must FortiGate allow even though the user cannot authenticate?
Answer : B
Refer to the exhibit which contains a RADIUS server configuration.
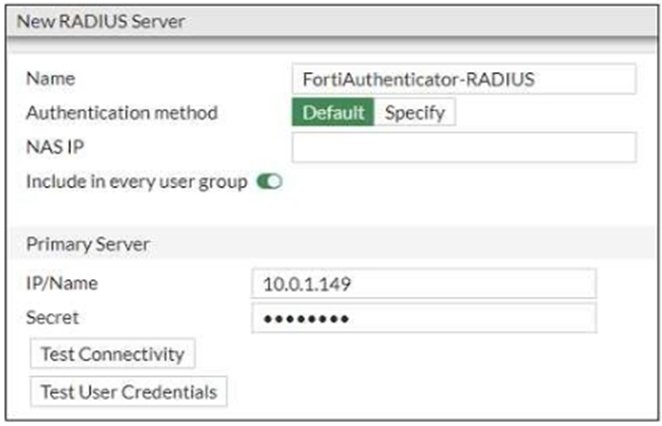
An administrator added a configuration for a new RADIUS server. While configuring, the administrator selected the Include in every user group option.
What is the impact of using the Include in every user group option in a RADIUS configuration?
Answer : A
By selecting the 'Include in every user group' option in the RADIUS configuration, FortiGate automatically includes this RADIUS server as an authentication source for all user groups. This means any user group configured on the FortiGate will authenticate using this RADIUS server, allowing users to authenticate against the server for any group they belong to.
Refer to the exhibit.
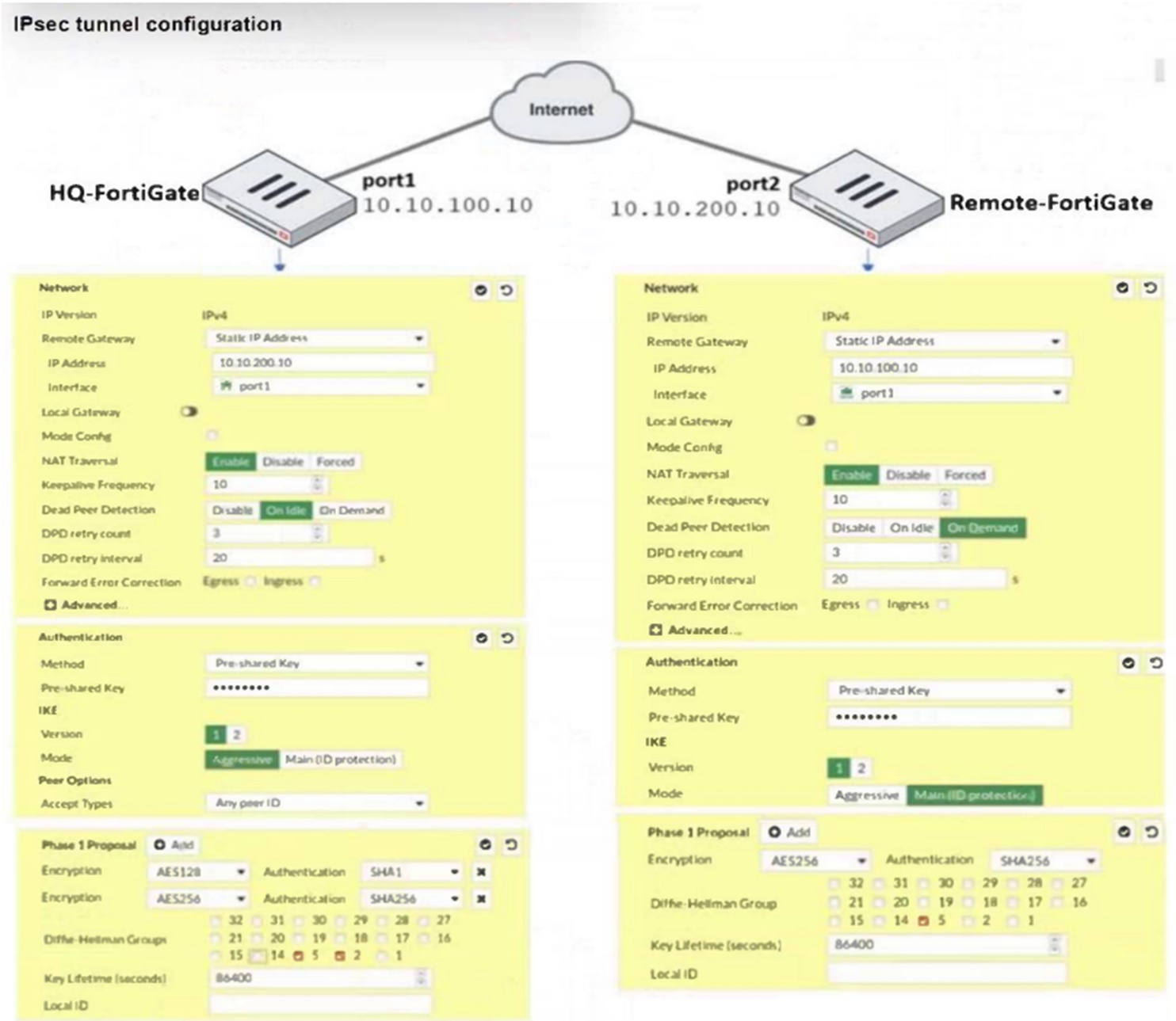
A network administrator is troubleshooting an IPsec tunnel between two FortiGate devices. The administrator has determined that phase 1 failed to come up. The administrator has also re-entered the pre-shared key on both FortiGate devices to make sure they match.
Based on the phase 1 configuration and the diagram shown in the exhibit, which two configuration changes can the administrator make to bring phase 1 up? (Choose two.)
Answer : B, D
Based on the phase 1 configuration and the diagram shown in the exhibit, the administrator can make the following two configuration changes to bring phase 1 up:
B . On Remote-FortiGate, set port2 as Interface: The diagram indicates that port2 is currently not selected under 'Interface' for Remote-FortiGate. Aligning this setting with HQ-FortiGate, which has port1 set as Interface, might resolve inconsistencies.
D . On HQ-FortiGate, set IKE mode to Main (ID protection): The current setting on HQ-FortiGate is Aggressive for IKE mode, while Remote-FortiGate is set to Main mode. Matching these settings may help in establishing phase 1 of the IPsec tunnel.
An administrator manages a FortiGate model that supports NTurbo.
How does NTurbo enhance performance for flow-based inspection?