Fortinet FCP - FortiSIEM 7.2 Analyst FCP_FSM_AN-7.2 Exam Practice Test
Refer to the exhibit.
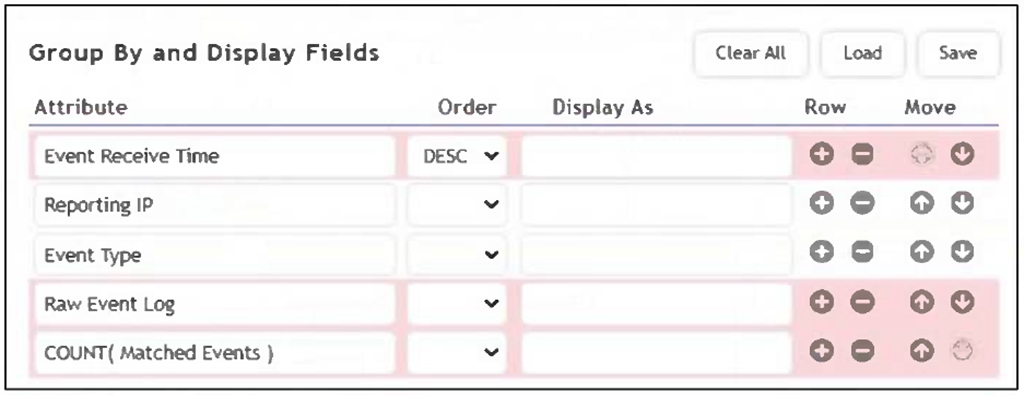
As shown in the exhibit, why are some of the fields highlighted in red?
Answer : A
The fields are highlighted in red because unique values such as Event Receive Time and Raw Event Log cannot be used in group-by operations. Grouping requires aggregatable or consistent values across events, while these fields are unique to each event, making them incompatible for grouping.
Refer to the exhibit.
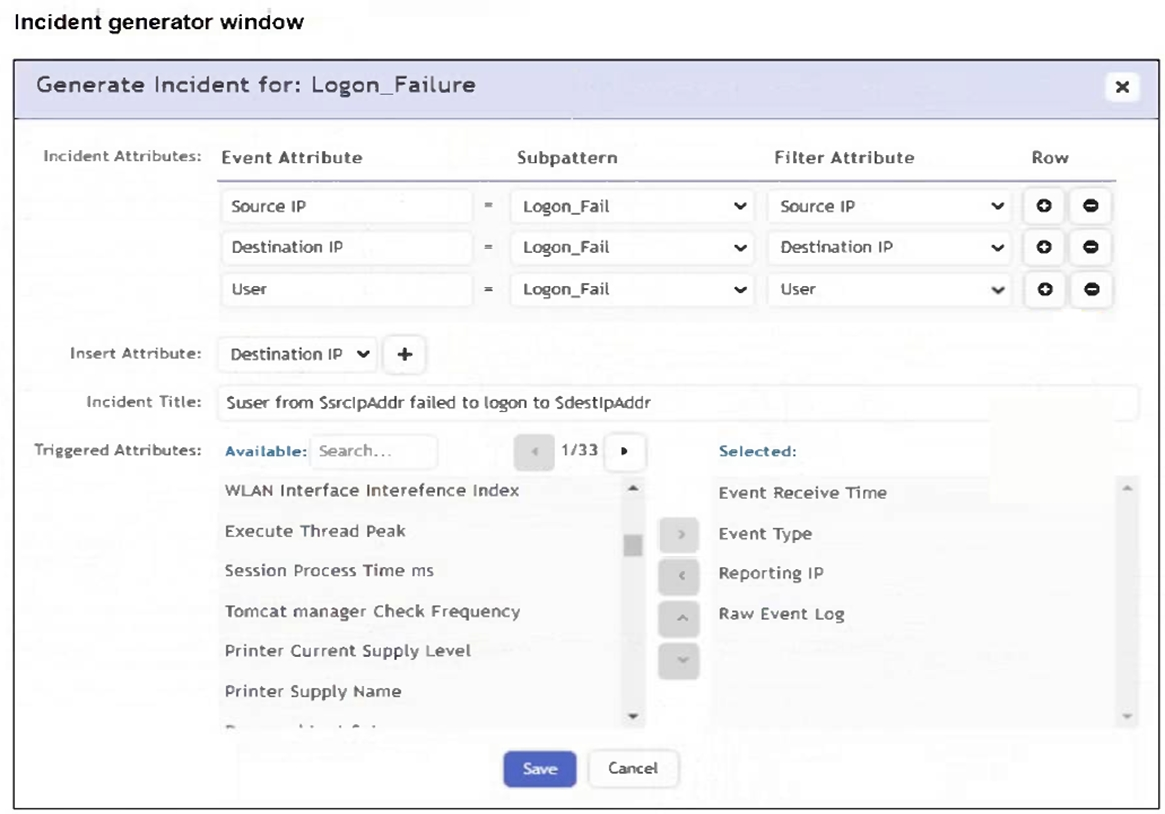
An analyst is trying to generate an incident with a title that includes the Source IP, Destination IP, User, and Destination Host Name. They are unable to add a Destination Host Name as an incident attribute.
What must be changed to allow the analyst to select Destination Host Name as an attribute?
Answer : A
For an attribute like Destination Host Name to be used in the incident title, it must first be included in the Triggered Attributes list. Only attributes listed there are available for substitution in the title template (e.g., $destIpAddr, $srcIpAddr).
Refer to the exhibit.
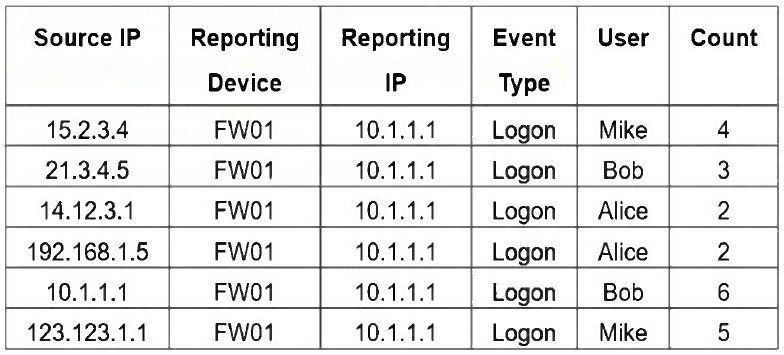
If you group the events by User, Source IP, and Count attributes, how many results will FortiSIEM display?
Answer : B
Grouping by User, Source IP, and Count means that each unique combination of those three attributes will be treated as a separate result. In the table, all six rows have distinct combinations of User, Source IP, and Count - so FortiSIEM will display 6 results.
Refer to the exhibit.
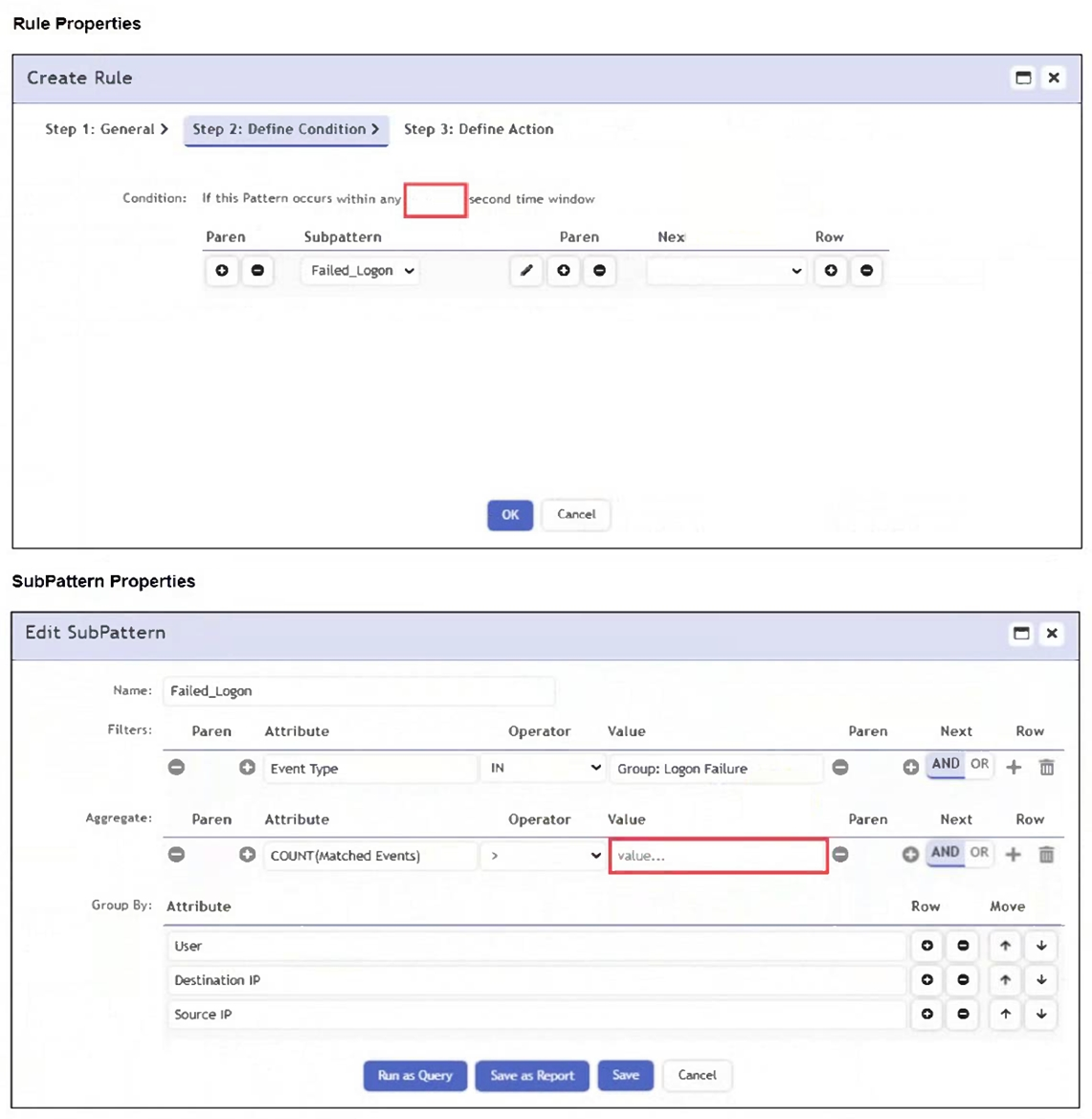
An analyst wants the rule shown in the exhibit to trigger when three failed login attempts occur within three minutes.
What should the values be for the condition time window and aggregate count?
Answer : A
To detect three failed login attempts within three minutes, you must set the aggregate count to 3 in the subpattern and the time window to 180 seconds in the rule condition. This ensures the rule triggers only if three or more failed logins occur in that timeframe.
Refer to the exhibit.
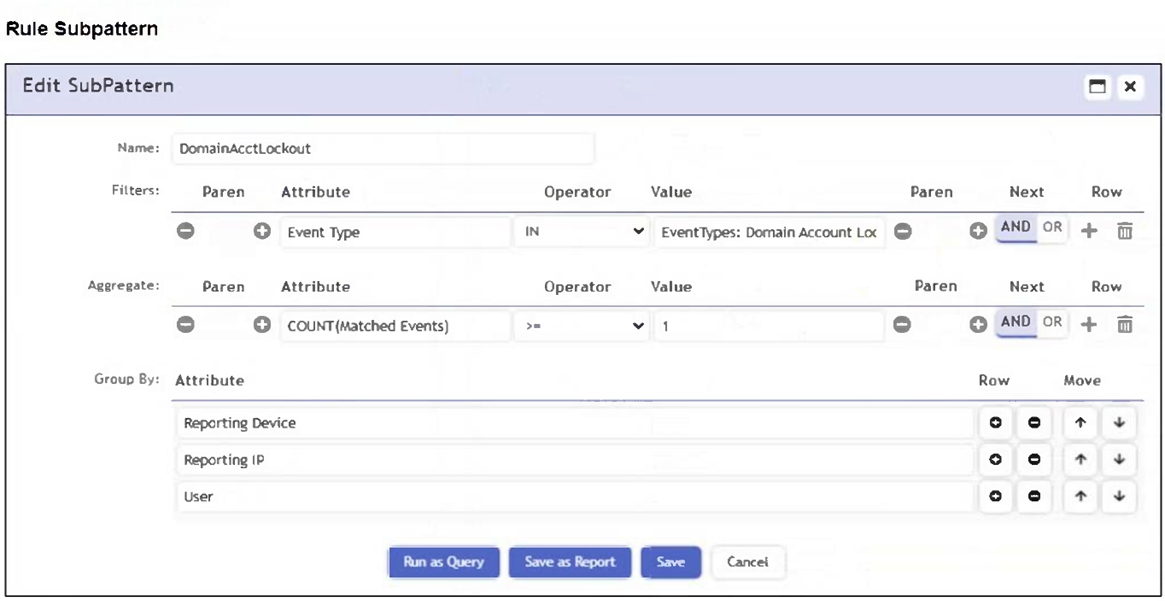
Which section contains the subpattern configuration that determines how many matching events are needed to trigger the rule?
Answer : A
The Aggregate section contains the condition COUNT(Matched Events) >= 1, which defines how many events must match the filter criteria for the rule to trigger. This is the subpattern configuration that determines the event threshold.
Refer to the exhibit.

Which value would you expect the FortiSIEM parser to use to populate the Application Name field?
Answer : C
The Application Name field in FortiSIEM is typically populated using the value of the app field in the raw log. In this event, app='SSL', so 'SSL' is the expected application name parsed by FortiSIEM.
Which statement about thresholds is true?
Answer : C
FortiSIEM evaluates performance metrics against both global thresholds, which apply system-wide, and per-device thresholds, which can be customized for individual devices. This dual approach allows flexibility in monitoring while ensuring consistent baseline alerting.