Fortinet FCP - AWS Cloud Security 7.4 Administrator FCP_WCS_AD-7.4 Exam Questions
You are troubleshooting network connectivity issues between two VMs deployed in AWS.
One VM is a FortiGate located on subnet "LAN" that is part of the VPC "Encryption". The other VM is a Windows server located on the subnet "servers" which is also in the "Encryption" VPC. You are unable to ping the Windows server from FortiGate.
What are two reasons for this? (Choose two.)
Answer : A, D
Windows Firewall Blocking Traffic:
The firewall on the Windows VM might be configured to block incoming ICMP traffic (ping requests). By default, Windows Firewall is set to block ICMP traffic, which could be a reason for the connectivity issue (Option A).
Security Group Configuration:
AWS Security Groups act as virtual firewalls for instances. If there is no rule allowing ICMP traffic in the security group attached to the Windows server, the ping requests from FortiGate will be blocked. An inbound allow ICMP rule must be added to the security group to permit this traffic (Option D).
Other Options Analysis:
Option B is incorrect because the default AWS Network Access Control List (NACL) allows all inbound and outbound traffic.
Option C is incorrect as AWS does allow ICMP traffic between subnets if properly configured with Security Groups and NACLs.
Refer to the exhibit.
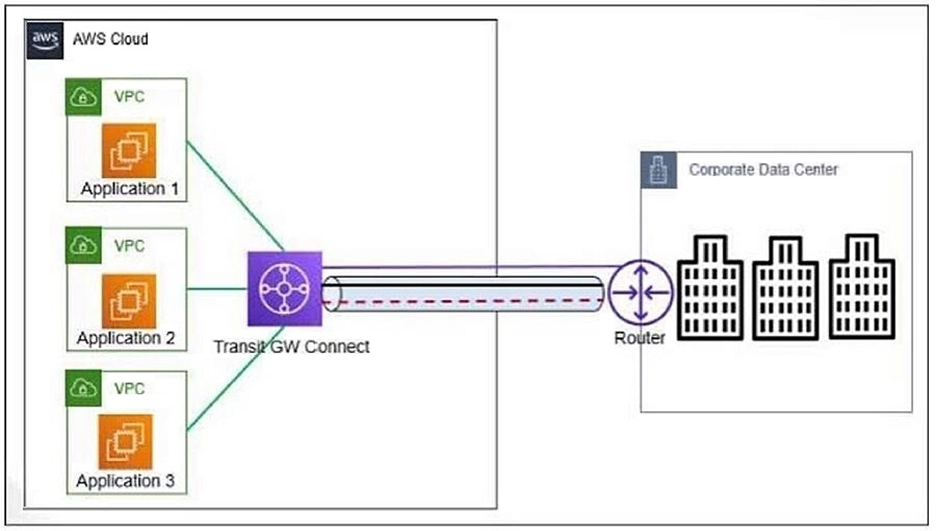
An organization deployed the application servers in the AWS VPC that connects to the corporate data center using Transit Gateway Connect. Demand for the applications has grown and the connection requires more bandwidth.
What is required to achieve higher bandwidth?
Answer : C
Understanding Transit Gateway Connect:
Transit Gateway Connect is a feature of AWS Transit Gateway that simplifies the integration of SD-WAN networks with AWS. It uses Generic Routing Encapsulation (GRE) tunnels to facilitate this connection.
GRE Tunnels and Bandwidth:
GRE tunnels can dynamically scale to meet increasing bandwidth demands. They allow multiple tunnels between the same endpoints, which can aggregate bandwidth without requiring additional configuration.
Scaling Bandwidth with GRE:
The GRE protocol used by Transit Gateway Connect can support high bandwidth requirements by spreading traffic across multiple tunnels. As demand grows, additional tunnels can be automatically used to handle the increased traffic load.
Comparison with Other Options:
Option A suggests using public IP addresses, which is not relevant to bandwidth scaling.
Option B is incorrect because bandwidth can be increased through GRE scaling.
Option D suggests adding a Transit VPC, which is unnecessary for increasing bandwidth when using Transit Gateway Connect.
A customer has implemented GWLB between the partner and application VPCs. FortiGate appliances are deployed in the partner VPC with multiple AZs to inspect traffic transparently.
Which two things will happen to application traffic based on the GWLB deployment? (Choose two.)
Answer : A, B
Understanding Gateway Load Balancer (GWLB):
GWLB is designed to distribute traffic across multiple appliances for both inbound and outbound traffic, providing scalability and high availability.
Traffic Load Balancing:
GWLB can send traffic to multiple FortiGate appliances for load balancing purposes, ensuring efficient use of resources (Option A).
Stateful Processing:
For stateful processing, GWLB ensures that traffic flows (both inbound and outbound) for a given connection are directed to the same FortiGate appliance. This maintains session integrity (Option B).
Preservation and Hashing of Traffic:
Options C and D are incorrect as they suggest incorrect behavior regarding traffic content preservation and hashing for data integrity, which are not primary functions of GWLB.
AWS Gateway Load Balancer Documentation: AWS Gateway Load Balancer
FortiGate Integration with GWLB: Fortinet Documentation
An administrator must deploy a web application firewall (WAF) solution to protect the web applications of their organization.
Why would the administrator choose FortiWeb Cloud over AWS WAF with Fortinet managed rules?
Answer : C
SSL Inspection Requirement:
FortiWeb Cloud provides comprehensive SSL inspection capabilities, allowing it to decrypt and inspect HTTPS traffic for threats. This is a crucial feature for many organizations that need to ensure all traffic, including encrypted traffic, is thoroughly inspected (Option C).
Comparison with AWS WAF:
While AWS WAF with Fortinet managed rules provides robust protection, it might not offer the same level of SSL inspection capabilities as FortiWeb Cloud.
Other Considerations:
Option A (Manual WAF signature updates) is incorrect because FortiWeb Cloud updates signatures automatically.
Option B (PCI 6.6 compliance) is a general requirement for any WAF solution, not specific to choosing FortiWeb Cloud over AWS WAF.
Option D (Traffic inspection for malware) is a feature provided by both FortiWeb Cloud and AWS WAF with Fortinet managed rules.
FortiWeb Cloud Overview: FortiWeb Cloud
You want to deploy the Fortinet HA CloudFormation template to stage and bootstrap the FortiGate configuration in the same region in which you created your VPC, which is Ohio US-East-2.
Based on this information, which statement is correct?
Answer : C
Understanding Fortinet HA CloudFormation Template:
The Fortinet High Availability (HA) CloudFormation template is used to automate the deployment and configuration of FortiGate instances in AWS.
Staging and Bootstrapping FortiGate:
Staging involves preparing the necessary configuration files and resources needed for deployment.
Bootstrapping is the process of automatically configuring FortiGate instances upon deployment.
S3 Bucket Requirement:
The configuration files required for staging and bootstrapping are typically stored in an S3 bucket.
Since the deployment is in the Ohio (US-East-2) region, it is recommended to host the S3 bucket in the same region to minimize latency and ensure regional compliance.
Comparison with Other Options:
Option A is incorrect because while an S3 bucket is required, it should be in the same region (US-East-2).
Option B is incorrect as the template does not automatically create the S3 bucket.
Option D is incorrect as DynamoDB is not used for staging and bootstrapping in this scenario.
Fortinet Documentation: FortiGate on AWS
A cloud administrator is tasked with protecting web applications hosted in AWS cloud.
Which three Fortinet cloud offerings can the administrator choose from to accomplish the task? (Choose three.)
Answer : C, D, E
FortiGate Cloud-Native Firewall (CNF):
FortiGate CNF offers cloud-native firewall capabilities designed to provide network security within AWS. It integrates seamlessly with AWS services and offers advanced threat protection and traffic management (Option C).
Fortinet Managed Rules for AWS WAF:
Fortinet Managed Rules for AWS WAF provide pre-configured, updated security rules that protect web applications from common threats such as SQL injection and cross-site scripting. This offering simplifies the protection of web applications hosted on AWS (Option D).
FortiWeb Cloud:
FortiWeb Cloud is a Web Application Firewall (WAF) as a service that provides comprehensive protection for web applications hosted on AWS. It offers features such as bot mitigation, DDoS protection, and deep inspection of HTTP/HTTPS traffic (Option E).
Comparison with Other Options:
Option A (AWS WAF) is a native AWS service, not a Fortinet offering.
Option B (FortiEDR) is focused on endpoint detection and response, which is not specifically aimed at protecting web applications.
FortiGate CNF Documentation: FortiGate CNF
Fortinet Managed Rules for AWS WAF: Fortinet AWS WAF Rules
FortiWeb Cloud Overview: FortiWeb Cloud
Refer to the exhibit.
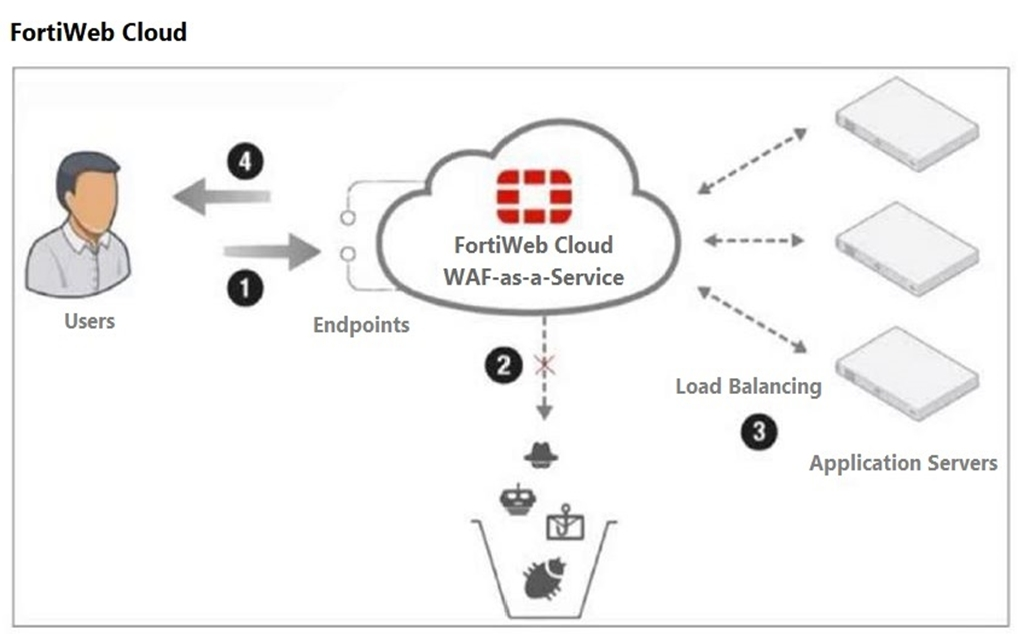
Which two statements are correct about traffic flow in FortiWeb Cloud? (Choose two.)
Answer : A, B
DNS Configuration:
For FortiWeb Cloud to effectively protect web applications, the DNS records for the application servers must be configured to point to FortiWeb Cloud. This ensures that all incoming traffic is routed through FortiWeb Cloud for inspection and protection (Option A).
Traffic Filtering:
FortiWeb Cloud provides robust protection by filtering incoming traffic to block the OWASP Top 10 attacks, zero-day threats, and other application layer attacks. This ensures the security and integrity of the web applications it protects (Option B).
Other Options Analysis:
Option C is incorrect because FortiWeb Cloud can protect application servers across different VPCs or regions, not just within the same VPC.
Option D is incorrect because step 2 does not require an AWS S3 bucket; it refers to the inspection and filtering of incoming traffic.
FortiWeb Cloud Overview: FortiWeb Cloud