Fortinet FCSS - Advanced Analytics 6.7 Architect FCSS_ADA_AR-6.7 Exam Practice Test
Refer to the exhibit.
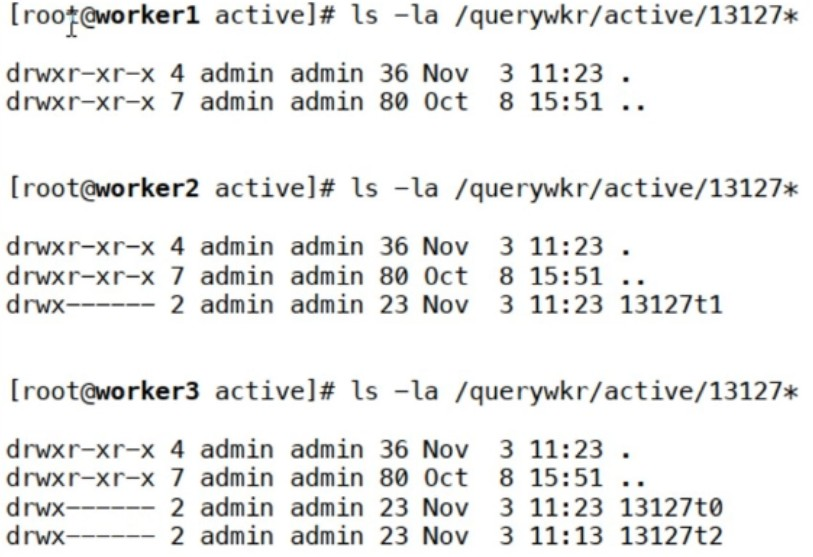
Which workers are assigned tasks for the query ID 13127? (Choose two.)
Answer : A, E
The exhibit shows the directory listings for three different workers (worker1, worker2, and worker3) under the /querywkr/active/13127* path, which indicates active query tasks assigned to each worker.
1. Worker1 (worker1)
2. Worker2 (worker2)
3. Worker3 (worker3)
Refer to the exhibit.
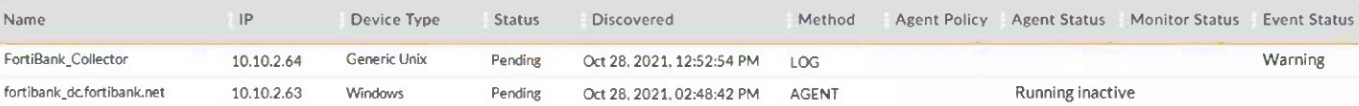
What are three possible reasons why the Agent Status displays Running Inactive? (Choose three.)
Answer : A, C, D
In FortiSIEM, an agent's status of 'Running Inactive' indicates that the agent is installed and running but not actively sending data or has encountered a misconfiguration. The following reasons can cause this status:
1. The agent was registered incorrectly
If an agent was not registered properly, it might not establish a proper connection with the FortiSIEM system, resulting in an inactive status.
2. The agent is temporarily down
If the agent goes offline (e.g., due to system shutdown, network issues, or agent crash), it will show as inactive.
3. The template was not assigned
Agents require a template to function correctly. If no template is assigned, the agent cannot collect or process events, leading to an inactive state.
Refer to the exhibit.
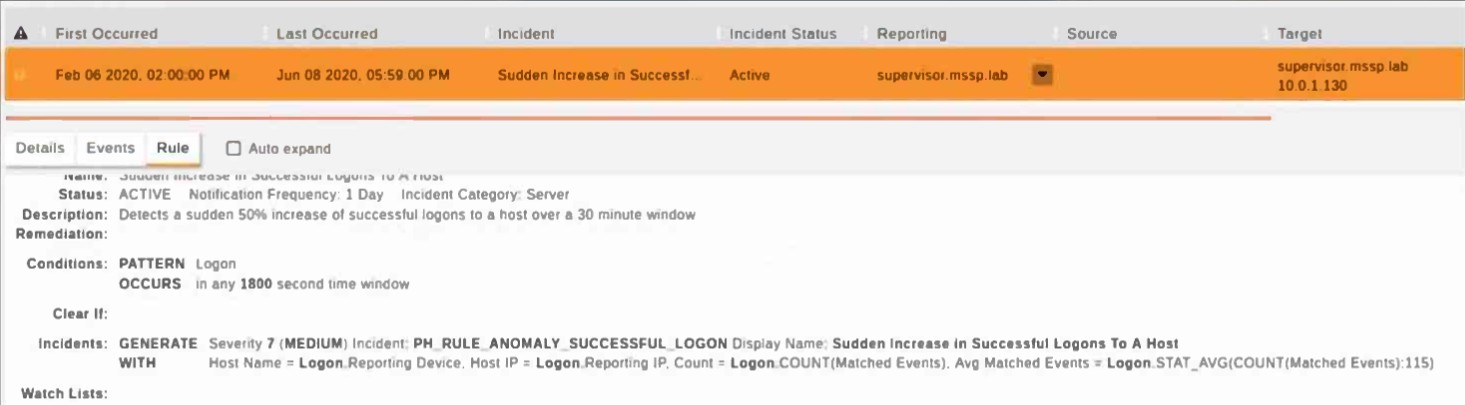
Within what time window is the incident auto cleared?
Answer : B
In the exhibit, the 'Clear If' condition does not specify a condition for auto-clearing the incident. If an incident does not have a specific clear condition, it remains active until manually resolved or cleared by another process.
Refer to the exhibit.
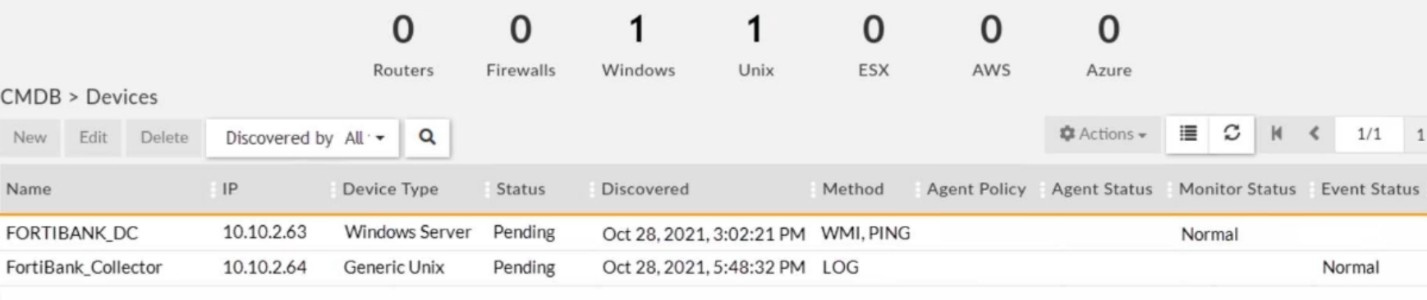
Why is the windows device still in the CMDB, even though the administrator uninstalled the windows agent?
Answer : A
Which statement accurately contrasts lookup tables with watchlists?
Answer : C
Lookup tables and watchlists serve different purposes in Fortinet's Advanced Analytics:
Lookup tables allow for structured data storage with multiple columns, making them useful for correlating different attributes or key-value pairs.
Watchlists are simpler and contain only a single column, often used for quick reference to flagged values, such as IP addresses or user accounts.
Refer to the exhibit.
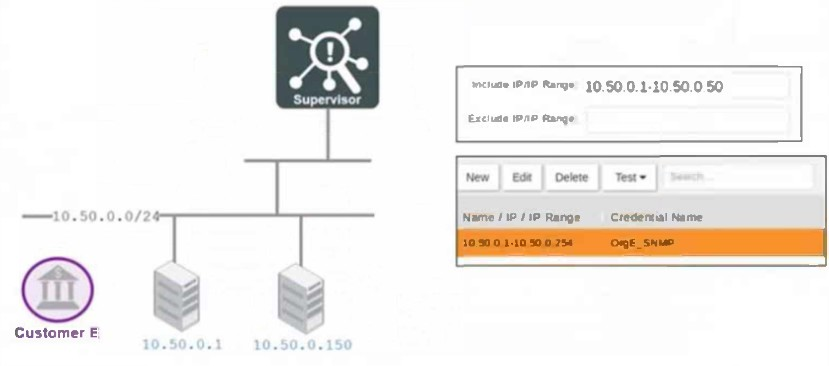
Which devices will be added to the CMDB and mapped to Customer E?
Answer : B, D
From the exhibit, we can determine the IP range that will be added to the CMDB and mapped to Customer E.
The included IP range is 10.50.0.1 -- 10.50.0.50.
This means any device within this range (10.50.0.1 to 10.50.0.50) will be added to the CMDB.
10.50.0.1 Falls within the included range (10.50.0.1 -- 10.50.0.50) Added to CMDB.
10.50.0.149 Falls within the 10.50.0.1 -- 10.50.0.50 range Added to CMDB.
How do customers connect to a shared multi-tenant instance on FortiSOAR?
Answer : B
In a multi-tenant FortiSOAR deployment, a Managed Security Service Provider (MSSP) hosts a shared FortiSOAR instance that serves multiple customers. Each customer operates as a separate tenant within the instance, ensuring data isolation and security.
FortiSOAR uses secure network connectivity (VPNs, direct connections, or secure tunnels) between the MSSP's FortiSOAR manager node and the customer's devices.
The customer does not need to install additional software or tenant nodes; instead, the MSSP manages multi-tenancy at the platform level.