Fortinet FCSS - Network Security 7.6 Support Engineer FCSS_NST_SE-7.6 Exam Practice Test
Which exchange lakes care of DoS protection in IKEv2?
Answer : C
TheIKE_SA_INITexchange in IKEv2 is responsible for DoS protection measures. During IKE_SA_INIT, before authentication and further exchange, the responder can use cookie challenges (per RFC 7296 and Fortinet VPN documentation). If a DoS attack is suspected (many requests from the same source), the responder replies with a cookie. Only after the initiator returns the correct cookie does the exchange proceed, protecting the responder from state exhaustion and certain forms of DoS traffic at the handshake stage.
FortiOS VPN Manual: IKEv2 Exchange Process and DoS Protections
IKEv2 RFC 7296: Description of IKE_SA_INIT and DoS Cookie Mechanism
Refer to the exhibit, which shows a partial output of a real-time LDAP debug.
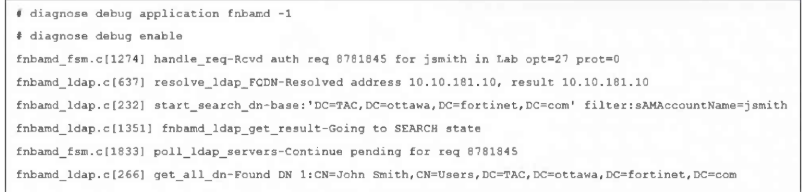
What two conclusions can you draw from the output? (Choose two.)
Answer : A, D
Refer to the exhibits.
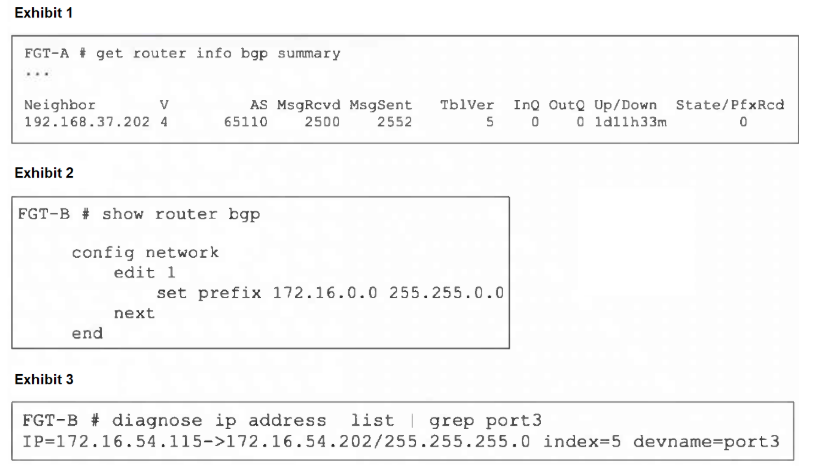
An administrator is attempting to advertise the network configured on port3. However, FGT-A is not receiving the prefix.
Which two actions can the administrator take to fix this problem? (Choose two.)
Answer : A, D
Refer to the exhibit, which shows a partial output from the get router info routing-table database command.

The administrator wants to configure a default static route for port3 and assign a distance of 50 and a priority of 0.
What will happen to the port1 and port2 default static routes after the port3 default static route is created?
Answer : A
Which statement about parallel path processing is correct (PPP)?
Answer : A
Parallel Path Processing (PPP) in FortiOS refers to the system's ability to evaluate and select among multiple processing paths---often involving dedicated network processors, content processors, or CPU-based workflows---to optimally process packets. The official documentation highlights that the PPP engine dynamically selects which hardware or software path to use for each session based on session characteristics, policy configuration, and traffic type. This dynamic selection results in optimal throughput and resource utilization.
The document specifies that PPP assesses several processing paths in parallel, using decision logic to determine whether a session should be offloaded to specialist hardware (like NP6, CP9, etc.) or stay in the CPU path, ensuring that each packet is handled by the most efficient available method under current load and policy. Hardware and software configurations both influence this outcome, but it is the PPP engine's decision-making that defines the optimal path per session.
Fortinet FortiGate Handbook: Parallel Path Processing
Fortinet FortiOS Technical Documentation: Packet Flow and Path Selection
Refer to the exhibit, which shows a truncated output of a real-time LDAP debug.
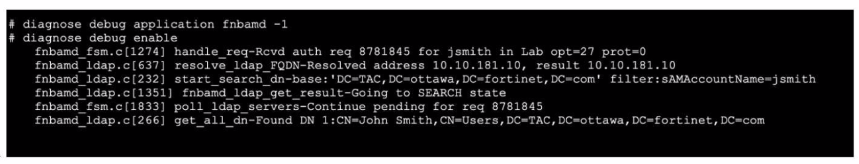
What two conclusions can you draw from the output? (Choose two.)
Answer : B, D
According toFortinet's LDAP authentication workflow as described in the FortiOS Administration Guide and the official LDAP debug log interpretation, each authentication attempt is split into several key steps: Bind Request, Search Request, and then, if successful, a Bind as the found user DN. In the provided debug output, we see 'start search_dn-base' with a filter 'sAMAccountName=jsmith' and the log line 'Going to SEARCH state,' confirming that FortiOS is in the second step---the Search Request (Option D). Official documentation highlights this exact phrase 'SEARCH state' as indicative of Step 2 within the LDAP process (''Bind Search Bind'').
Additionally, the last line ''Found DN 1: CN=John Smith, CN=Users, DC=TAC, DC=ottawa, DC=fortinet, DC=com'' verifies that the system has successfully mapped the username to the Distinguished Name (DN) and this user is ''John Smith.'' The authentication will now proceed using this mapped user (Option B). Fortinet's logs record the found DN after a successful search, which is a strong confirmation that the user's credentials can be validated against the found DN.
Options A and C are not supported directly by the debug output shown:
The server name 'Lab' is referenced as part of the request, but not explicitly as the LDAP server's configured name in this output.
Step 3 (Bind Request) would follow finding the DN, but the log here demonstrates the Search and DN found---per Fortinet, this precedes the actual Bind/validation step.
FortiOS Administration Guide: LDAP Authentication Process and Debug Logs
Fortinet Official KB: LDAP Integration Workflow and Log Interpretation
In which two slates is a given session categorized as ephemeral? (Choose two.)
Answer : A, C