Fortinet FCSS - Security Operations 7.4 Analyst FCSS_SOC_AN-7.4 Exam Practice Test
Which three end user logs does FortiAnalyzer use to identify possible IOC compromised hosts? (Choose three.)
Answer : B, D, E
Overview of Indicators of Compromise (IoCs): Indicators of Compromise (IoCs) are pieces of evidence that suggest a system may have been compromised. These can include unusual network traffic patterns, the presence of known malicious files, or other suspicious activities.
FortiAnalyzer's Role: FortiAnalyzer aggregates logs from various Fortinet devices to provide comprehensive visibility and analysis of network events. It uses these logs to identify potential IoCs and compromised hosts.
Relevant Log Types:
DNS Filter Logs:
DNS requests are a common vector for malware communication. Analyzing DNS filter logs helps in identifying suspicious domain queries, which can indicate malware attempting to communicate with command and control (C2) servers.
IPS Logs:
Intrusion Prevention System (IPS) logs detect and block exploit attempts and malicious activities. These logs are critical for identifying compromised hosts based on detected intrusion attempts or behaviors matching known attack patterns.
Web Filter Logs:
Web filtering logs monitor and control access to web content. These logs can reveal access to malicious websites, download of malware, or other web-based threats, indicating a compromised host.
Why Not Other Log Types:
Email Filter Logs:
While important for detecting phishing and email-based threats, they are not as directly indicative of compromised hosts as DNS, IPS, and Web filter logs.
Application Filter Logs:
These logs control application usage but are less likely to directly indicate compromised hosts compared to the selected logs.
Detailed Process:
Step 1: FortiAnalyzer collects logs from FortiGate and other Fortinet devices.
Step 2: DNS filter logs are analyzed to detect unusual or malicious domain queries.
Step 3: IPS logs are reviewed for any intrusion attempts or suspicious activities.
Step 4: Web filter logs are checked for access to malicious websites or downloads.
Step 5: FortiAnalyzer correlates the information from these logs to identify potential IoCs and compromised hosts.
Fortinet Documentation: FortiOS DNS Filter, IPS, and Web Filter administration guides.
FortiAnalyzer Administration Guide: Details on log analysis and IoC identification.
By using DNS filter logs, IPS logs, and Web filter logs, FortiAnalyzer effectively identifies possible compromised hosts, providing critical insights for threat detection and response.
Which FortiAnalyzer connector can you use to run automation stitches9
Answer : D
Overview of Automation Stitches:
Automation stitches in FortiAnalyzer are predefined sets of automated actions triggered by specific events. These actions help in automating responses to security incidents, improving efficiency, and reducing the response time.
FortiAnalyzer Connectors:
FortiAnalyzer integrates with various Fortinet products and other third-party solutions through connectors. These connectors facilitate communication and data exchange, enabling centralized management and automation.
Available Connectors for Automation Stitches:
FortiCASB:
FortiCASB is a Cloud Access Security Broker that helps secure SaaS applications. However, it is not typically used for running automation stitches within FortiAnalyzer.
FortiMail:
FortiMail is an email security solution. While it can send logs and events to FortiAnalyzer, it is not primarily used for running automation stitches.
Local:
The local connector refers to FortiAnalyzer's ability to handle logs and events generated by itself. This is useful for internal processes but not specifically for integrating with other Fortinet devices for automation stitches.
FortiOS:
FortiOS is the operating system that runs on FortiGate firewalls. FortiAnalyzer can use the FortiOS connector to communicate with FortiGate devices and run automation stitches. This allows FortiAnalyzer to send commands to FortiGate, triggering predefined actions in response to specific events.
Detailed Process:
Step 1: Configure the FortiOS connector in FortiAnalyzer to establish communication with FortiGate devices.
Step 2: Define automation stitches within FortiAnalyzer that specify the actions to be taken when certain events occur.
Step 3: When a triggering event is detected, FortiAnalyzer uses the FortiOS connector to send the necessary commands to the FortiGate device.
Step 4: FortiGate executes the commands, performing the predefined actions such as blocking an IP address, updating firewall rules, or sending alerts.
Conclusion:
The FortiOS connector is specifically designed for integration with FortiGate devices, enabling FortiAnalyzer to execute automation stitches effectively.
Fortinet FortiOS Administration Guide: Details on configuring and using automation stitches.
Fortinet FortiAnalyzer Administration Guide: Information on connectors and integration options.
By utilizing the FortiOS connector, FortiAnalyzer can run automation stitches to enhance the security posture and response capabilities within a network.
Which two statements about the FortiAnalyzer Fabric topology are true? (Choose two.)
Answer : B, D
Understanding FortiAnalyzer Fabric Topology:
The FortiAnalyzer Fabric topology is designed to centralize logging and analysis across multiple devices in a network.
It involves a hierarchy where the supervisor node manages and coordinates with other Fabric members.
Analyzing the Options:
Option A: Downstream collectors forwarding logs to Fabric members is not a typical configuration. Instead, logs are usually centralized to the supervisor.
Option B: For effective management and log centralization, logging devices must be registered to the supervisor. This ensures proper log collection and coordination.
Option C: The supervisor does not primarily use an API to store logs, incidents, and events locally. Logs are stored directly in the FortiAnalyzer database.
Option D: For the Fabric topology to function correctly, all Fabric members need to be in analyzer mode. This mode allows them to collect, analyze, and forward logs appropriately within the topology.
Conclusion:
The correct statements regarding the FortiAnalyzer Fabric topology are that logging devices must be registered to the supervisor and that Fabric members must be in analyzer mode.
Fortinet Documentation on FortiAnalyzer Fabric Topology.
Best Practices for Configuring FortiAnalyzer in a Fabric Environment.
Which two playbook triggers enable the use of trigger events in later tasks as trigger variables? (Choose two.)
Answer : A, B
Understanding Playbook Triggers:
Playbook triggers are the starting points for automated workflows within FortiAnalyzer or FortiSOAR.
These triggers determine how and when a playbook is executed and can pass relevant information (trigger variables) to subsequent tasks within the playbook.
Types of Playbook Triggers:
EVENT Trigger:
Initiates the playbook when a specific event occurs.
The event details can be used as variables in later tasks to customize the response.
Selected as it allows using event details as trigger variables.
INCIDENT Trigger:
Activates the playbook when an incident is created or updated.
The incident details are available as variables in subsequent tasks.
Selected as it enables the use of incident details as trigger variables.
ON SCHEDULE Trigger:
Executes the playbook at specified times or intervals.
Does not inherently use trigger events to pass variables to later tasks.
Not selected as it does not involve passing trigger event details.
ON DEMAND Trigger:
Runs the playbook manually or as required.
Does not automatically include trigger event details for use in later tasks.
Not selected as it does not use trigger events for variables.
Implementation Steps:
Step 1: Define the conditions for the EVENT or INCIDENT trigger in the playbook configuration.
Step 2: Use the details from the trigger event or incident in subsequent tasks to customize actions and responses.
Step 3: Test the playbook to ensure that the trigger variables are correctly passed and utilized.
Conclusion:
EVENT and INCIDENT triggers are specifically designed to initiate playbooks based on specific occurrences, allowing the use of trigger details in subsequent tasks.
Fortinet Documentation on Playbook Configuration FortiSOAR Playbook Guide
By using the EVENT and INCIDENT triggers, you can leverage trigger events in later tasks as variables, enabling more dynamic and responsive playbook actions.
Refer to the Exhibit:
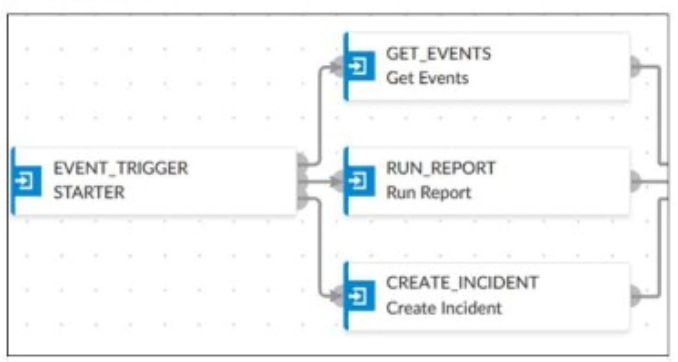
An analyst wants to create an incident and generate a report whenever FortiAnalyzer generates a malicious attachment event based on FortiSandbox analysis. The endpoint hosts are protected by FortiClient EMS integrated with FortiSandbox. All devices are logging to FortiAnalyzer.
Which connector must the analyst use in this playbook?
Answer : A
Understanding the Requirements:
The objective is to create an incident and generate a report based on malicious attachment events detected by FortiAnalyzer from FortiSandbox analysis.
The endpoint hosts are protected by FortiClient EMS, which is integrated with FortiSandbox. All logs are sent to FortiAnalyzer.
Key Components:
FortiAnalyzer: Centralized logging and analysis for Fortinet devices.
FortiSandbox: Advanced threat protection system that analyzes suspicious files and URLs.
FortiClient EMS: Endpoint management system that integrates with FortiSandbox for endpoint protection.
Playbook Analysis:
The playbook in the exhibit consists of three main actions: GET_EVENTS, RUN_REPORT, and CREATE_INCIDENT.
EVENT_TRIGGER: Starts the playbook when an event occurs.
GET_EVENTS: Fetches relevant events.
RUN_REPORT: Generates a report based on the events.
CREATE_INCIDENT: Creates an incident in the incident management system.
Selecting the Correct Connector:
The correct connector should allow fetching events related to malicious attachments analyzed by FortiSandbox and facilitate integration with FortiAnalyzer.
Connector Options:
FortiSandbox Connector:
Directly integrates with FortiSandbox to fetch analysis results and events related to malicious attachments.
Best suited for getting detailed sandbox analysis results.
Selected as it is directly related to the requirement of handling FortiSandbox analysis events.
FortiClient EMS Connector:
Used for managing endpoint security and integrating with endpoint logs.
Not directly related to fetching sandbox analysis events.
Not selected as it is not directly related to the sandbox analysis events.
FortiMail Connector:
Used for email security and handling email-related logs and events.
Not applicable for sandbox analysis events.
Not selected as it does not relate to the sandbox analysis.
Local Connector:
Handles local events within FortiAnalyzer itself.
Might not be specific enough for fetching detailed sandbox analysis results.
Not selected as it may not provide the required integration with FortiSandbox.
Implementation Steps:
Step 1: Ensure FortiSandbox is configured to send analysis results to FortiAnalyzer.
Step 2: Use the FortiSandbox connector in the playbook to fetch events related to malicious attachments.
Step 3: Configure the GET_EVENTS action to use the FortiSandbox connector.
Step 4: Set up the RUN_REPORT and CREATE_INCIDENT actions based on the fetched events.
Fortinet Documentation on FortiSandbox Integration FortiSandbox Integration Guide
Fortinet Documentation on FortiAnalyzer Event Handling FortiAnalyzer Administration Guide
By using the FortiSandbox connector, the analyst can ensure that the playbook accurately fetches events based on FortiSandbox analysis and generates the required incident and report.
While monitoring your network, you discover that one FortiGate device is sending significantly more logs to FortiAnalyzer than all of the other FortiGate devices in the topology.
Additionally, the ADOM that the FortiGate devices are registered to consistently exceeds its quota.
What are two possible solutions? (Choose two.)
Answer : B, C
Understanding the Problem:
One FortiGate device is generating a significantly higher volume of logs compared to other devices, causing the ADOM to exceed its storage quota.
This can lead to performance issues and difficulties in managing logs effectively within FortiAnalyzer.
Possible Solutions:
The goal is to manage the volume of logs and ensure that the ADOM does not exceed its quota, while still maintaining effective log analysis and monitoring.
Solution A: Increase the Storage Space Quota for the First FortiGate Device:
While increasing the storage space quota might provide a temporary relief, it does not address the root cause of the issue, which is the excessive log volume.
This solution might not be sustainable in the long term as log volume could continue to grow.
Not selected as it does not provide a long-term, efficient solution.
Solution B: Create a Separate ADOM for the First FortiGate Device and Configure a Different Set of Storage Policies:
Creating a separate ADOM allows for tailored storage policies and management specifically for the high-log-volume device.
This can help in distributing the storage load and applying more stringent or customized retention and storage policies.
Selected as it effectively manages the storage and organization of logs.
Solution C: Reconfigure the First FortiGate Device to Reduce the Number of Logs it Forwards to FortiAnalyzer:
By adjusting the logging settings on the FortiGate device, you can reduce the volume of logs forwarded to FortiAnalyzer.
This can include disabling unnecessary logging, reducing the logging level, or filtering out less critical logs.
Selected as it directly addresses the issue of excessive log volume.
Solution D: Configure Data Selectors to Filter the Data Sent by the First FortiGate Device:
Data selectors can be used to filter the logs sent to FortiAnalyzer, ensuring only relevant logs are forwarded.
This can help in reducing the volume of logs but might require detailed configuration and regular updates to ensure critical logs are not missed.
Not selected as it might not be as effective as reconfiguring logging settings directly on the FortiGate device.
Implementation Steps:
For Solution B:
Step 1: Access FortiAnalyzer and navigate to the ADOM management section.
Step 2: Create a new ADOM for the high-log-volume FortiGate device.
Step 3: Register the FortiGate device to this new ADOM.
Step 4: Configure specific storage policies for the new ADOM to manage log retention and storage.
For Solution C:
Step 1: Access the FortiGate device's configuration interface.
Step 2: Navigate to the logging settings.
Step 3: Adjust the logging level and disable unnecessary logs.
Step 4: Save the configuration and monitor the log volume sent to FortiAnalyzer.
Fortinet Documentation on FortiAnalyzer ADOMs and log management FortiAnalyzer Administration Guide
Fortinet Knowledge Base on configuring log settings on FortiGate FortiGate Logging Guide
By creating a separate ADOM for the high-log-volume FortiGate device and reconfiguring its logging settings, you can effectively manage the log volume and ensure the ADOM does not exceed its quota.
Refer to Exhibit:
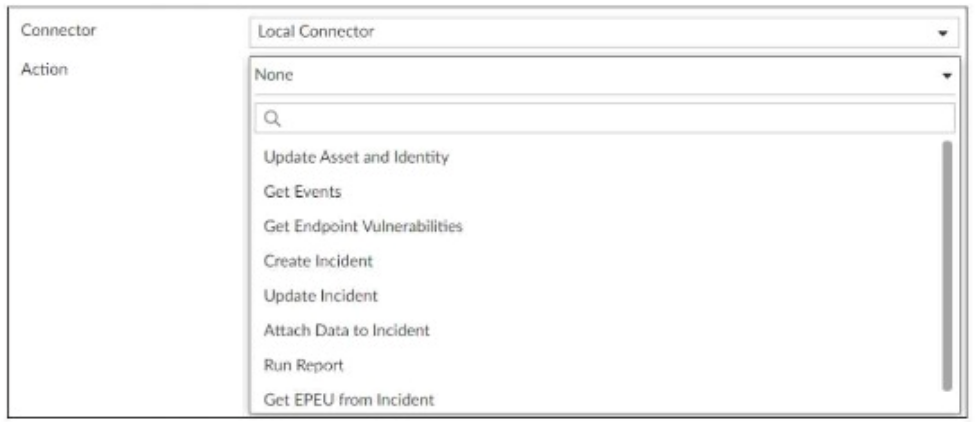
A SOC analyst is designing a playbook to filter for a high severity event and attach the event information to an incident.
Which local connector action must the analyst use in this scenario?
Answer : D
Understanding the Playbook Requirements:
The SOC analyst needs to design a playbook that filters for high severity events.
The playbook must also attach the event information to an existing incident.
Analyzing the Provided Exhibit:
The exhibit shows the available actions for a local connector within the playbook.
Actions listed include:
Update Asset and Identity
Get Events
Get Endpoint Vulnerabilities
Create Incident
Update Incident
Attach Data to Incident
Run Report
Get EPEU from Incident
Evaluating the Options:
Get Events: This action retrieves events but does not attach them to an incident.
Update Incident: This action updates an existing incident but is not specifically for attaching event data.
Update Asset and Identity: This action updates asset and identity information, not relevant for attaching event data to an incident.
Attach Data to Incident: This action is explicitly designed to attach additional data, such as event information, to an existing incident.
Conclusion:
The correct action to use in the playbook for filtering high severity events and attaching the event information to an incident is Attach Data to Incident.
Fortinet Documentation on Playbook Actions and Connectors.
Best Practices for Incident Management and Playbook Design in SOC Operations.