Fortinet NSE 4 - FortiOS 7.2 NSE4_FGT-7.2 Exam Questions
Refer to the exhibit.
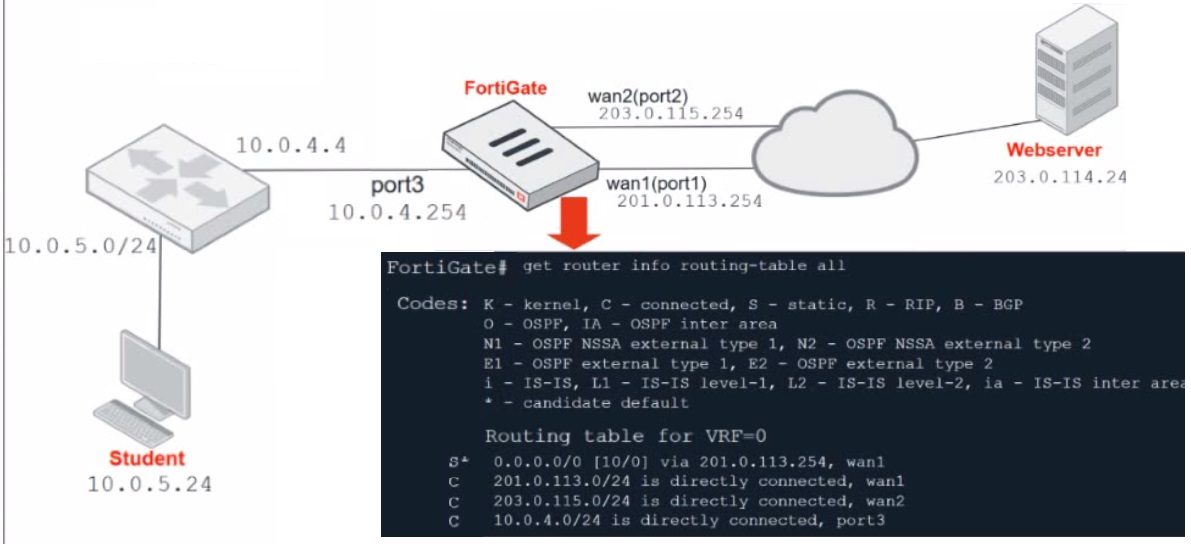
Which contains a network diagram and routing table output.
The Student is unable to access Webserver.
What is the cause of the problem and what is the solution for the problem?
Answer : D
A network administrator has enabled full SSL inspection and web filtering on FortiGate. When visiting any HTTPS websites, the browser reports certificate warning errors. When visiting HTTP websites, the browser does not report errors.
What is the reason for the certificate warning errors?
Answer : D
FortiGate Security 7.2 Study Guide (p.235): 'If FortiGate receives a trusted SSL certificate, then it generates a temporary certificate signed by the built-in Fortinet_CA_SSL certificate and sends it to the browser. If the browser trusts the Fortinet_CA_SSL certificate, the browser completes the SSL handshake. Otherwise, the browser also presents a warning message informing the user that the site is untrusted. In other words, for this function to work as intended, you must import the Fortinet_CA_SSL certificate into the trusted root CA certificate store of your browser.'
Which of the following SD-WAN load balancing method use interface weight value to distribute traffic? (Choose two.)
What are two characteristics of FortiGate HA cluster virtual IP addresses? (Choose two.)
Answer : A, D
Fortigate Infrastructure 7.2 Study Guide page 301
FortiGate Infrastructure 7.2 Study Guide (p.301):
'FGCP automatically assigns the heartbeat IP addresses based on the serial number of each device. The IP address 169.254.0.1 is assigned to the device with the highest serial number.'
'A change in the heartbeat IP addresses may happen when a FortiGate device joins or leaves the cluster.'
'The HA cluster uses the heartbeat IP addresses to distinguish the cluster members and synchronize data.'
https://networkinterview.com/fortigate-ha-high-availability/
An administrator is configuring an IPsec VPN between site A and site B. The Remote Gateway setting in both sites has been configured as Static IP Address. For site A, the local quick mode selector is 192. 168. 1.0/24 and the remote quick mode selector is 192. 168.2.0/24.
Which subnet must the administrator configure for the local quick mode selector for site B?
Answer : C
For an IPsec VPN between site A and site B, the administrator has configured the local quick mode selector for site A as 192.168.1.0/24 and the remote quick mode selector as 192.168.2.0/24. This means that the VPN will allow traffic to and from the 192.168.1.0/24 subnet at site A to reach the 192.168.2.0/24 subnet at site B.
To complete the configuration, the administrator must configure the local quick mode selector for site B. To do this, the administrator must use the same subnet as the remote quick mode selector for site A, which is 192.168.2.0/24. This will allow traffic to and from the 192.168.2.0/24 subnet at site B to reach the 192.168.1.0/24 subnet at site A.
Therefore, the administrator must configure the local quick mode selector for site B as 192.168.2.0/24.
An administrator needs to increase network bandwidth and provide redundancy.
What interface type must the administrator select to bind multiple FortiGate interfaces?
Which two configuration settings are synchronized when FortiGate devices are in an active-active HA cluster? (Choose two.)
Answer : C, D
In the 7.2 Infrastructure Guide (page 306) the list of configuration settings that are NOT synchronized includes both 'FortiGate host name' and 'Cache'