Fortinet NSE 5 - FortiSIEM 6.3 NSE5_FSM-6.3 Exam Practice Test
If FortiSIEM supervisor is deployed with the worker using the proprietary flat file database, which action is required?
Answer : A
Refer to the exhibit.
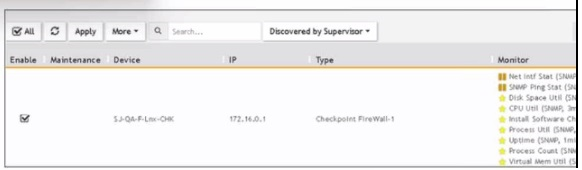
What does the pauso icon indicate?
Answer : D
Data Collection Status: FortiSIEM displays various icons to indicate the status of data collection for different devices.
Pause Icon: The pause icon specifically indicates that data collection is paused, but this can happen due to several reasons.
Common Cause for Pausing: One common cause for pausing data collection is an issue such as a change of password, which prevents the system from authenticating and collecting data.
Exhibit Analysis: In the provided exhibit, the presence of the pause icon next to the device suggests that data collection has encountered an issue that has caused it to pause.
Reference: FortiSIEM 6.3 User Guide, Device Management and Data Collection Status Icons section, which explains the different icons and their meanings.
Which protocol do collectors use to communicate with a FortiSIEM cluster?
Answer : C
Refer to the exhibit.
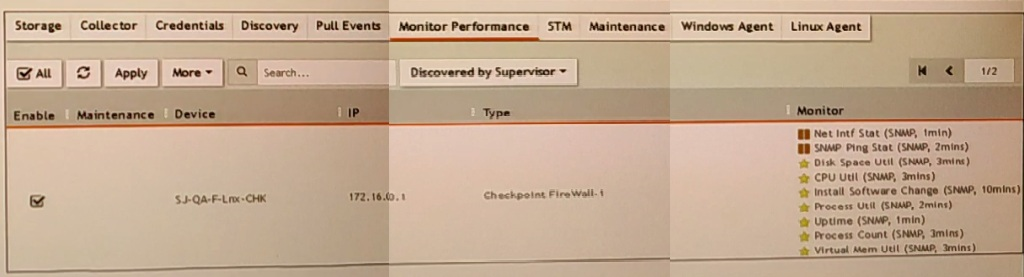
What do the yellow stars listed in the Monitor column indicate?
Answer : B
Monitor Column Indicators: In FortiSIEM, the Monitor column displays the status of various metrics applied during the discovery process.
Yellow Star Meaning: A yellow star next to a metric indicates that the metric was successfully applied during discovery and data has been collected for that metric.
Successful Data Collection: This visual indicator helps administrators quickly identify which metrics are active and have data available for analysis.
Reference: FortiSIEM 6.3 User Guide, Device Monitoring section, which explains the significance of different icons and indicators in the Monitor column.
What are two tasks that you must do to make a secondary FortiSIEM device ready for disaster recovery? (Choose two.)
Answer : A, D
In me FortiSIEM CLI. which command must you use to determine whether or not syslog is being received from a network device?
Answer : A
Syslog Reception Verification: To verify whether syslog messages are being received from a network device, a network packet capture tool can be used.
tcpdump Command: tcpdump is a powerful command-line packet analyzer tool available in Unix-like operating systems. It allows administrators to capture and analyze network traffic.
Usage: By using tcpdump with the appropriate filters (e.g., port 514 for syslog), administrators can monitor the incoming syslog messages in real-time to verify if they are being received.
Example Command: tcpdump -i <interface> port 514 captures the syslog messages on the specified network interface.
Reference: FortiSIEM 6.3 User Guide, CLI Commands section, which details the usage of tcpdump for network traffic analysis and verification of syslog reception.
Refer to the exhibit.
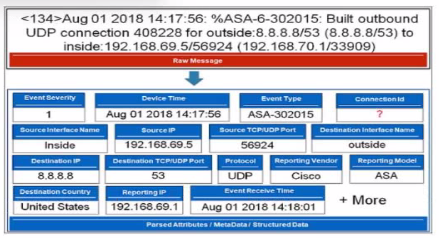
Which value will FortiSIEM use to populate the Connection Id field?
Answer : D