Fortinet NSE 6 - FortiMail 7.2 NSE6_FML-7.2 Exam Questions
Refer to the exhibit, which shows a few lines of FortiMail logs.
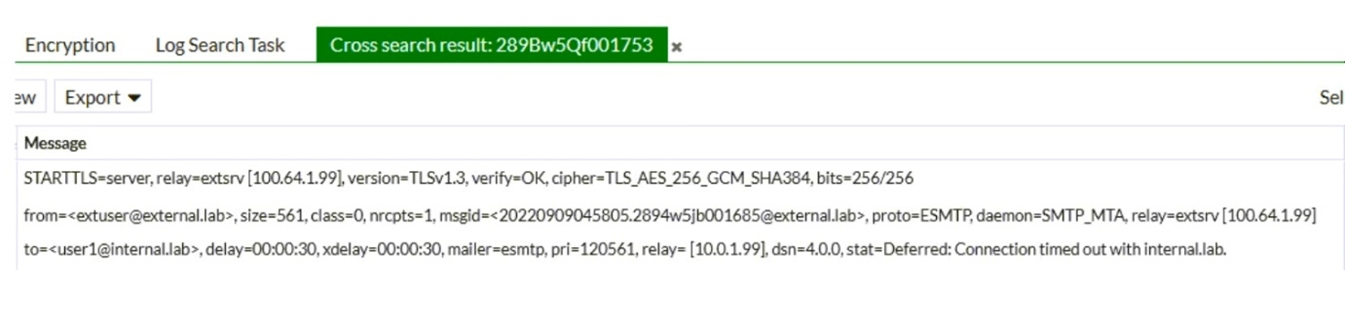
Based on these log entries, which two statements correctly describe the operational status of this FortiMail device? (Choose two.)
Answer : A, C
Which item is a supported one-time secure token for IBE authentication?
Answer : D
While reviewing logs, an administrator discovers that an incoming email was processed using policy IDs 0:4:9:INTERNAL.
Which two statements describe what this policy ID means? (Choose two.)
Answer : A, C
Refer to the exhibit, which shows an inbound recipient policy.
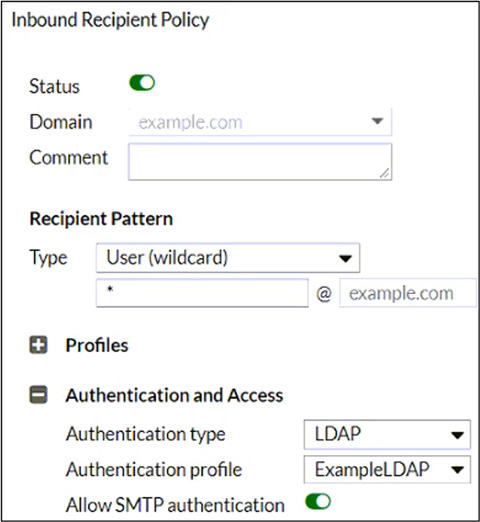
After creating the policy shown in the exhibit, an administrator discovers that clients can send unauthenticated emails using SMTP.
What must the administrator do to enforce authentication?
Answer : D
In which two places can the maximum email size be overridden on FortiMail? (Choose two.)
Answer : B, C
In which FortiMail configuration object can you assign an outbound session profile?
Answer : A
Refer to the exhibit which shows the output of an email transmission using a telnet session.
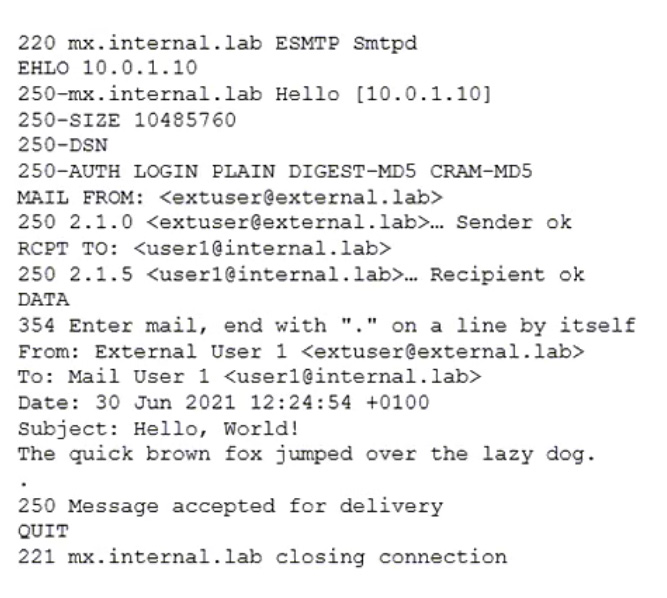
What are two correct observations about this SMTP session? (Choose two.)
Answer : C, D