Fortinet NSE 6 - FortiMail 7.2 NSE6_FML-7.2 Exam Practice Test
Refer to the exhibit which shows the output of an email transmission using a telnet session.
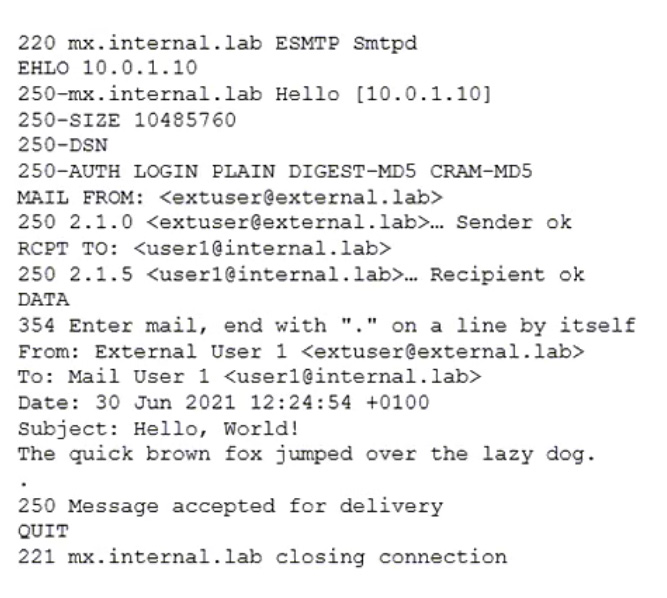
What are two correct observations about this SMTP session? (Choose two.)
Answer : C, D
Refer to the exhibits which show a topology diagram (Topology), and a configuration element (Access Control Rule).
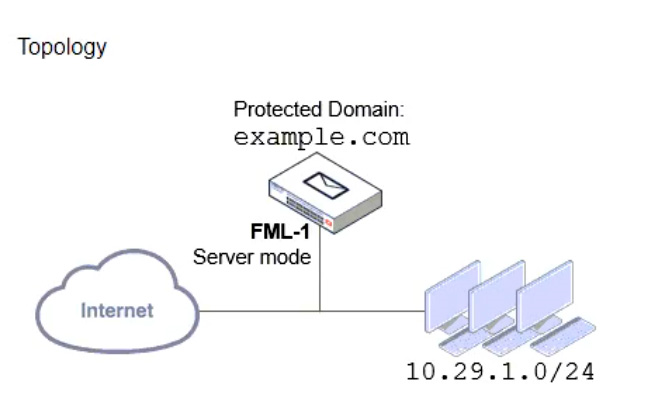
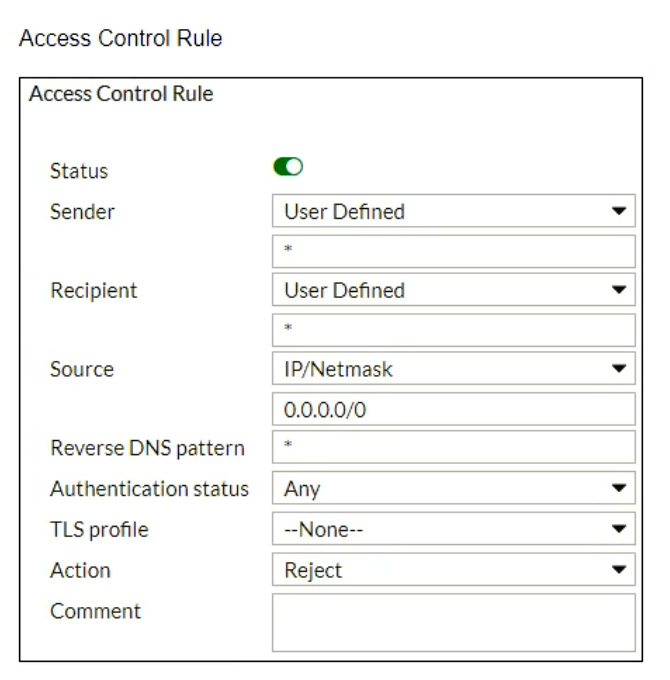
An administrator must enforce authentication on FML-1 for all outbound email from the example.com domain.
Which two settings should be used to configure the access receive rule? (Choose two.)
Answer : A, D
While reviewing logs, an administrator discovers that an incoming email was processed using policy IDs 0:4:9:INTERNAL.
Which two statements describe what this policy ID means? (Choose two.)
Answer : A, C
A FortiMail administrator is investigating a sudden increase in DSNs being delivered to their protected domain. After searching the logs, the administrator identifies that the DSNs were not generated because of any outbound email sent from their organization.
Which FortiMail antispam technique can the administrator use to prevent this scenario?
Answer : D
Refer to the exhibit which shows a detailed history log view.
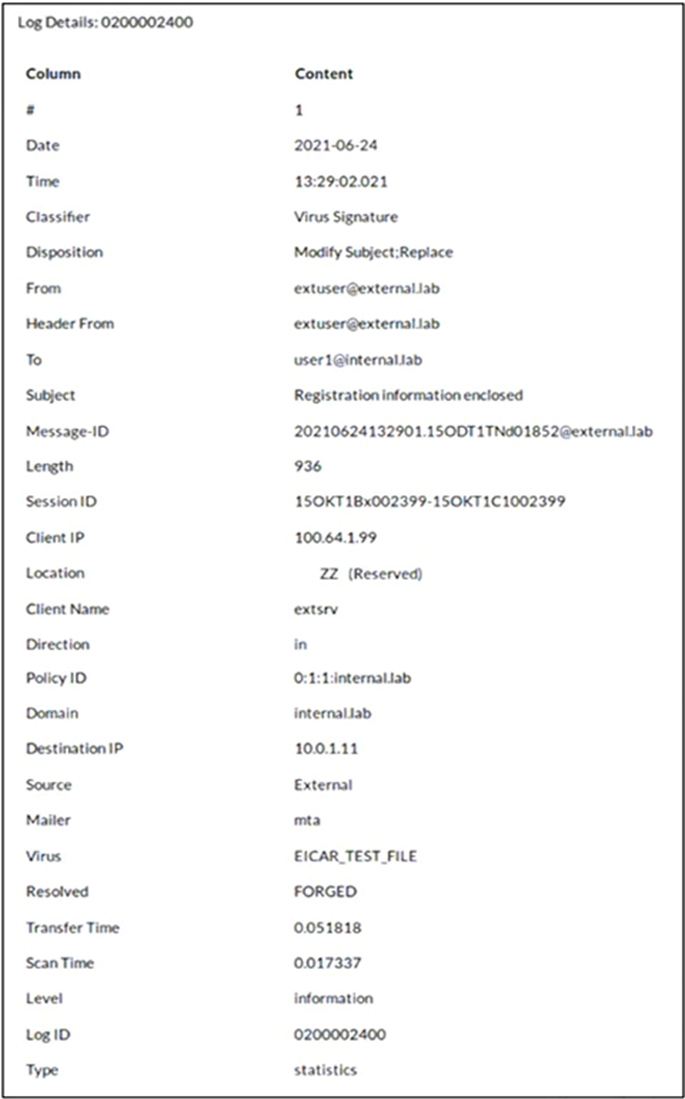
Which two actions did FortiMail take on this email message? (Choose two.)
Answer : A, B
Refer to the exhibit which shows the Authentication Reputation list on a gateway mode FortiMail device.

Why was the IP address blocked?
Answer : C
Refer to the exhibit which shows a command prompt output of a telnet command.
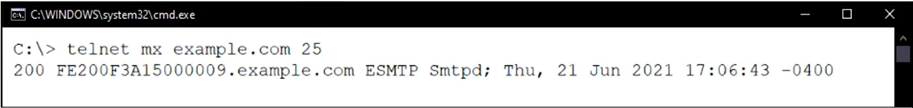
Which configuration change must you make to prevent the banner from displaying the FortiMail serial number?
Answer : A