Fortinet NSE 6 - FortiNAC 7.2 NSE6_FNC-7.2 Exam Practice Test
Which two are required for endpoint compliance monitors? (Choose two.}
Answer : A, C
View the output.
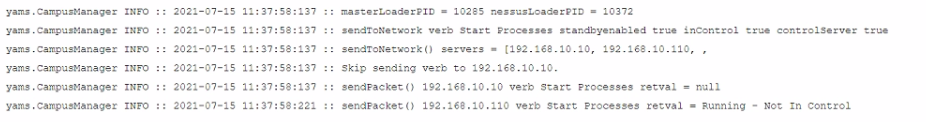
Examine the communication between a primary FortiNAC (192.168.10.10) and a secondary FortiNAC (192.166.10.110) configured as an HA pair What is the current state of the FortiNAC HA pair?
Answer : A
Which three are components of a security rule? (Choose three.)
Answer : C, D, E
Components of a security rule in FortiNAC include:
Trigger: The condition or event that initiates the evaluation of the rule.
User or Host Profile: A requirement that can be added to a rule to specify the user or host profile that must be matched.
Action: The activities or responses that FortiNAC performs when the rule is matched.
Reference
FortiNAC 7.2 Study Guide, page 419
In which view would you find who made modifications to a Group?
Answer : D
It's important to audit Group Policy changes in order to determine the details of changes made to Group Policies by delegated users.
During the on-boarding process through the captive portal, what are two reasons why a host that successfully registered would remain stuck in the Registration VLAN? (Choose two.)
Answer : B, D
While troubleshooting a network connectivity issue, an administrator determines that a device was being automatically provisioned to an incorrect VLAN.
Where would the administrator look to determine when and why FortiNAC made the network access change?
Answer : C
View the command and output.
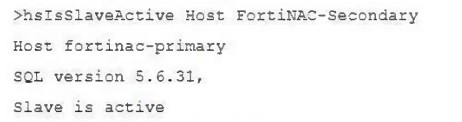
What is the state of database replication?
Answer : D
The command and output shown in the exhibit indicate that the host FortiNAC-Secondary is referencing FortiNAC-Primary, and it states 'Slave is active.' In database replication terminology within a high availability setup, the term 'Slave is active' typically means that the secondary server (slave) is actively receiving data from the primary server (master). This implies that the synchronization process from the primary to the secondary database has been successful and is currently active.
Reference
FortiNAC 7.2 Study Guide, Security Policies section