Fortinet NSE 7 - Enterprise Firewall 7.2 NSE7_EFW-7.2 Exam Questions
Refer to the exhibit, which shows an error in system fortiguard configuration.
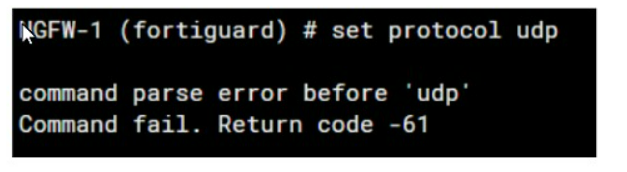
What is the reason you cannot set the protocol to udp in config system fortiguard?
Answer : B
The reason for the command failure when trying to set the protocol to UDP in the config system fortiguard is likely that UDP is not a protocol option in this context. The command syntax might be incorrect or the option to set a protocol for FortiGuard updates might not exist in this manner. So the correct answer is D. udp is not a protocol option.
Exhibit.
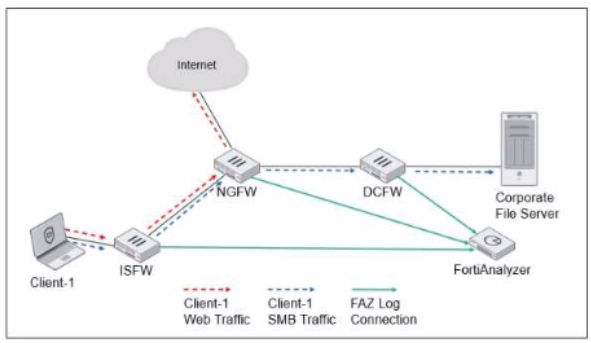
ISFW is installed in the access layer NGFW is performing SNAT and web tittering DCFW is running IPS Which two statements are true regarding the Security Fabric logging? (Choose two.)
Answer : A, B
An administrator configured the following command on FortiGate
config router ospf
sec reszart-mode graceful-restart
Which two statements correctly describe the result of the above command? (Choose two.)
Answer : B, C
Which three conditions are required (or two FortiGate devices to form an OSPF adjacency? (Choose three.)
Answer : B, D, E
Refer to the exhibit.
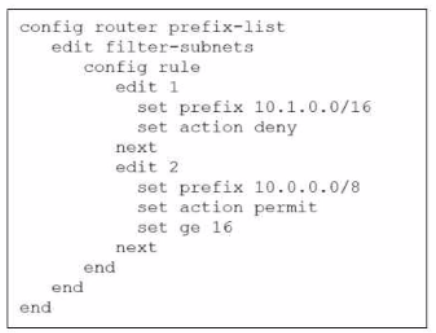
The exhibit shows a prefix list configuration
What can you conclude from the above prefix-list configuration?
Answer : C
Exhibit.
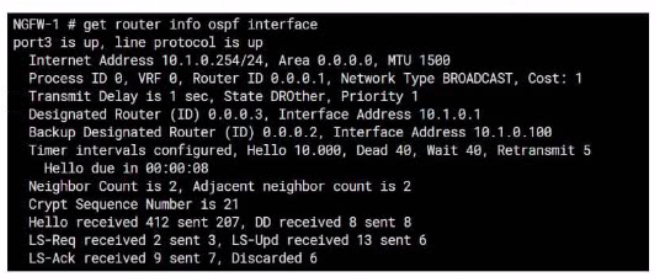
Refer to the exhibit, which shows information about an OSPF interlace
What two conclusions can you draw from this command output? (Choose two.)
Answer : A, C
From the OSPF interface command output, we can conclude that the port3 network has more than one OSPF router because the Neighbor Count is 2, indicating the presence of another OSPF router besides NGFW-1. Additionally, we can deduce that the interfaces of the OSPF routers match the MTU value configured as 1500, which is necessary for OSPF neighbors to form adjacencies. The MTU mismatch would prevent OSPF from forming a neighbor relationship.
Fortinet FortiOS Handbook: OSPF Configuration
Refer to the exhibit, which shows device registration on FortiManager.
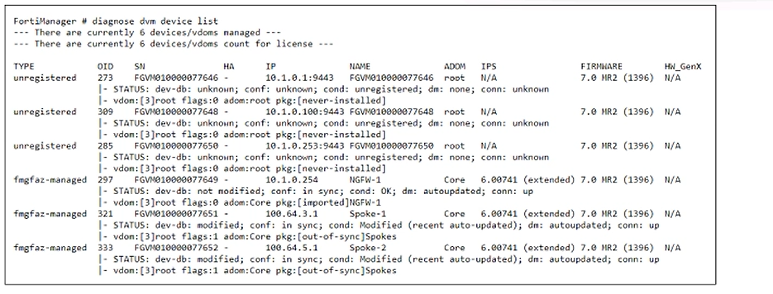
What can you conclude about the Spoke-1 and Spoke-2 configurations with respect to the information cond: Modified (recent auto-updated)?
Answer : B