Fortinet NSE 7 - LAN Edge 7.0 NSE7_LED-7.0 Exam Practice Test
Which CLI command should an administrator use on FortiGate to view the RSSO authentication process in real time?
Answer : A
Refer to the exhibit.
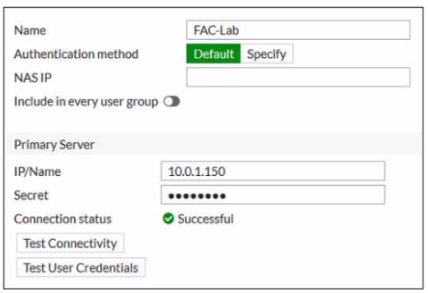
Examine the RADIUS server configuration shown in the exhibit
An administrator has configured a RADIUS server on FortiGate that points to FortiAuthenticator FortiAuthenticator is acting as an authentication proxy and is configured to relay all authentication requests to a remote Windows AD server using LDAP
While testing the configuration the administrator noticed that the diagnose test authserver command worked with PAP, however authentication requests failed when using MSCHAP2
Which two solutions can the administrator implement to get MSCHAP2 authentication to work'' (Choose two.)
Answer : A, C
According to the exhibit, the RADIUS server configuration on FortiGate points to FortiAuthenticator, which is acting as an authentication proxy and is configured to relay all authentication requests to a remote Windows AD server using LDAP. However, LDAP does not support MSCHAP2 authentication, which is required for RADIUS. Therefore, option A is true because on FortiAuthenticator, enabling Windows Active Directory Domain Authentication will add FortiAuthenticator to the Windows domain and allow it to use MSCHAP2 authentication with the AD server. Option C is also true because on FortiAuthenticator, changing the back-end authentication server from LDAP to RADIUS will allow it to use MSCHAP2 authentication with the AD server. Option B is false because on FortiGate, configuring the NAS IP setting on the RADIUS server will not affect the MSCHAP2 authentication, but rather the source IP address of the RADIUS packets. Option D is false because on FortiGate, updating the Secret setting on the RADIUS server will not affect the MSCHAP2 authentication, but rather the shared secret between FortiGate and FortiAuthenticator.
Refer to the exhibit.
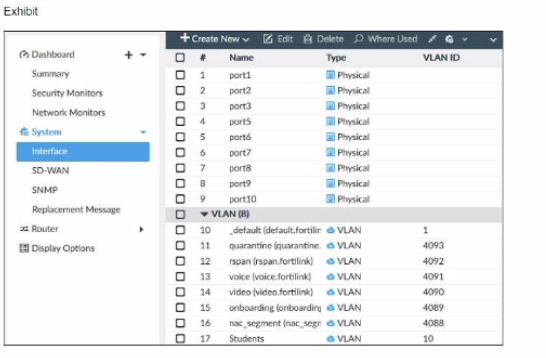
Examine the FortiSwitch port configuration and the FortiGate interface configuration shown in the exhibit.
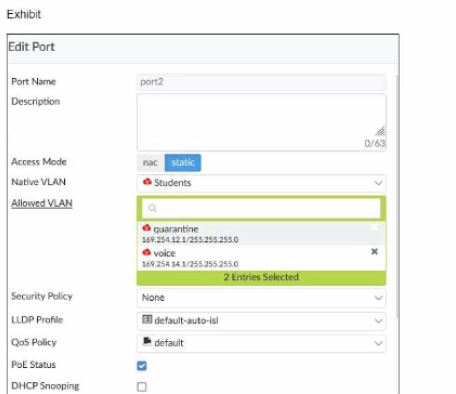
Based on the configuration shown in the exhibit, which two statements about how port2 handles tagged and untagged traffic are true? (Choose two.)
Answer : A, B
Refer to the exhibit.
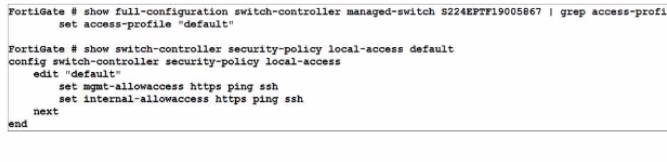
An administrator wants to telnet into the S224EPTF19005867 switch over the FortiGate FortiLink interface.
Which configuration change should the administrator make?
Answer : C
Refer to the exhibit.
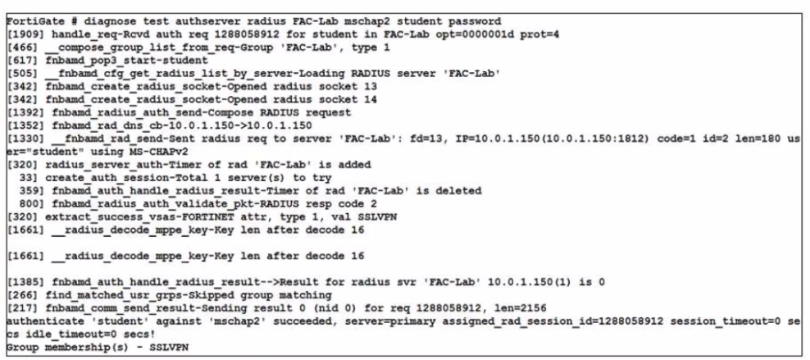
Examine the debug output shown in the exhibit
Which two statements about the RADIUS debug output are true'' (Choose two)
Answer : A, C
Refer to the exhibit.
Examine the FortiGate RSSO configuration shown in the exhibit.
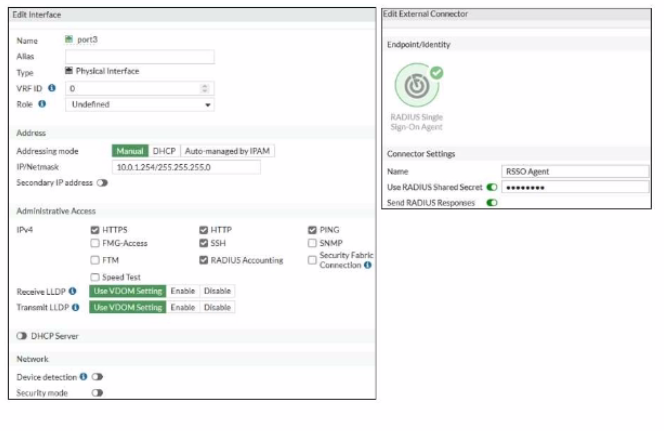
FortiGate is configured to receive RADIUS accounting messages on port3 to authenticate RSSO users. The incoming RADIUS accounting messages contain the username and group membership information in the User-Name and Class RADIUS attributes, respectively.
Which three settings must you configure on FortiGate to successfully authenticate RSSO users and match them to the existing RSSO user groups? (Choose three)
Answer : A, C, E
Refer to the exhibit.
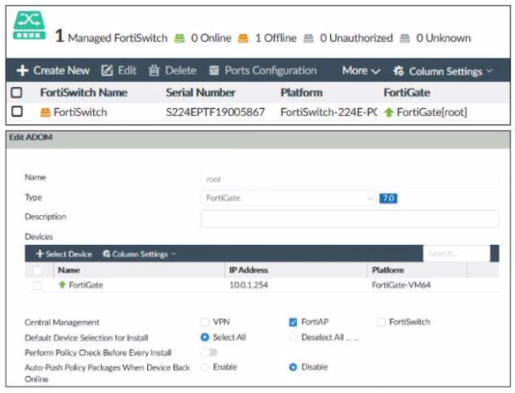
Examine the FortiManager information shown in the exhibit
Which two statements about the FortiManager status are true'' (Choose two)
Answer : A, D