Fortinet NSE 7 - Secure Access 6.2 NSE7_SAC-6.2 Exam Questions
Refer to the exhibit.
Examine the configuration of the FortiSwitch security policy profile.
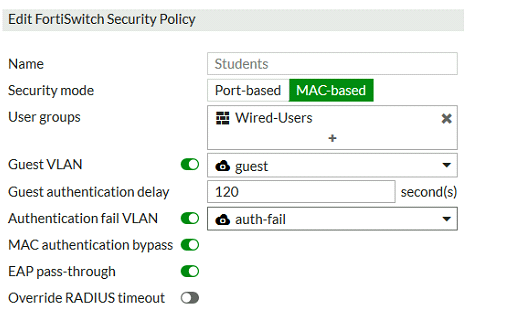
If the security profile shown in the exhibit is assigned on the FortiSwitch port for 802 1X. port authentication, which statement is correct?
Answer : C
Refer to the exhibit.
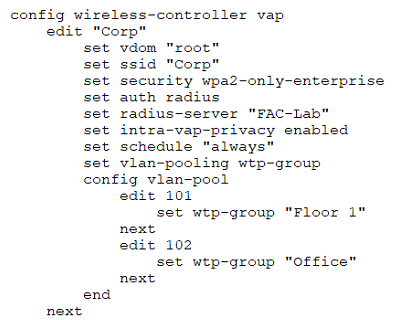
Examine the VAP configuration and the WiFi zones table shown in the exhibits.
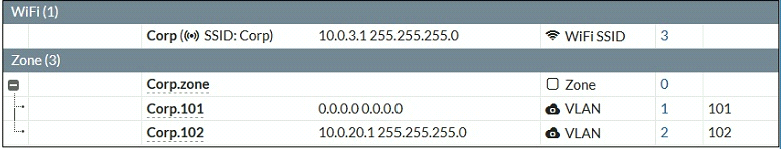
Which two statements describe FortiGate behavior regarding assignment of
Answer : B, D
Refer to the exhibit.
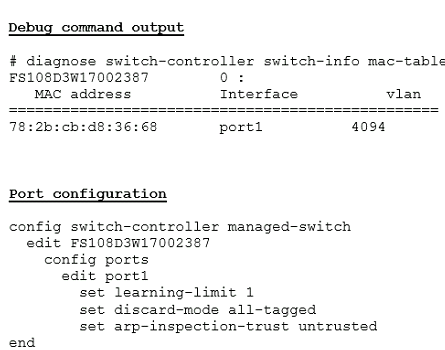
Examine the output of the debug command and port configuration shown in the exhibit.
FortiGate learned the MAC address 78:2b:cb:d8:36:68 dynamically.
What action does FortiSwitch take if there is an untagged frame coming to port1 will different MAC address?
Answer : A
Refer to the exhibit.
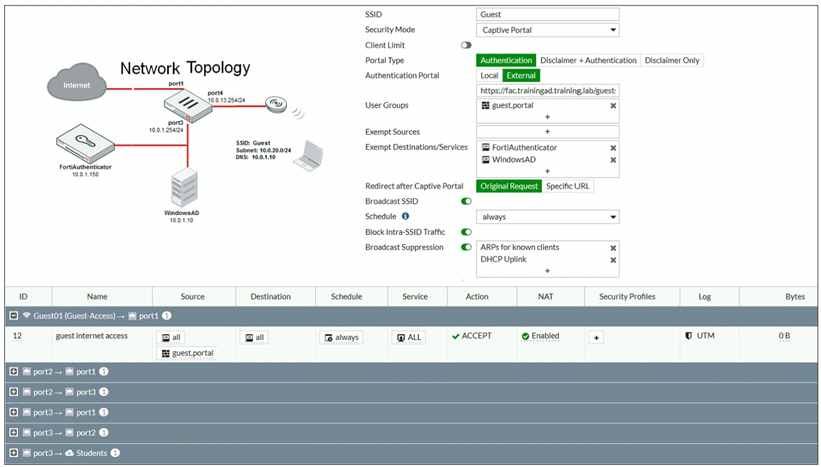
The exhibit shows a network topology and SSID settings.
FortiGate is configured to use an external captive portal. However, wireless users are not able to see the captive portal login page.
Which configuration change should the administrator make to fix the problem?
What does DHCP snooping MAC verification do?
What action does FortiSwitch take when it receives a loop guard data packet (LGDP) that was sent by itself?
A FotliGate has the following LDAP configuration
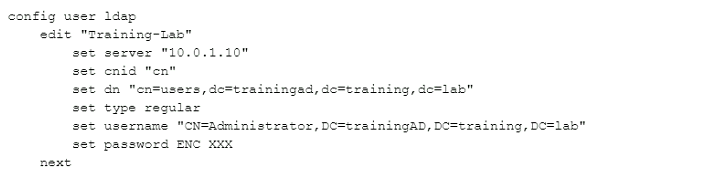
On the Windows LDAP server 10.0.1.10, the administrator used dsqueryT which returned the following output:
>dsquery user -samid admin* "CN=AdministratorrCN=UsersiDC=trainingAD;DC=trainingiDC=lab"
According to the output, which FortiGate LDAP setting is configured incorrectly?
Answer : B