Fortinet NSE 7 - SD-WAN 7.2 NSE7_SDW-7.2 Exam Practice Test
Refer to the exhibits.
Exhibit A
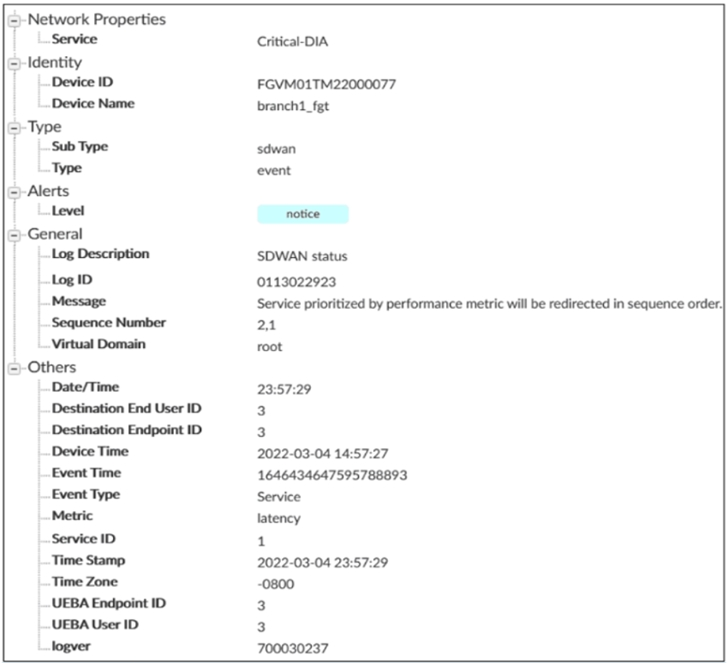
Exhibit B
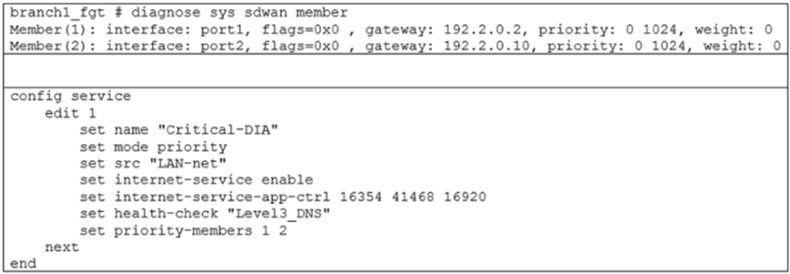
Exhibit A shows an SD-WAN event log and exhibit B shows the member status and the SD-WAN rule configuration.
Based on the exhibits, which two statements are correct? (Choose two.)
Answer : A, C
Which statement about SD-WAN zones is true?
Answer : B
Full Explanation:
Option A is incorrect because SD-WAN zones can include multiple interface types (e.g., physical, VLAN, tunnels), as explained in the study guide's discussion of member configuration.
Option B is correct because an SD-WAN zone can logically have zero members (an empty zone) and up to a large number of members, with 512 being a reasonable upper bound supported by Fortinet's scalability, even if not explicitly stated in the study guide.
Option C is incorrect because the study guide clearly states that SD-WAN zones can be used in static route definitions, enhancing routing flexibility.
Option D, while possibly true based on Fortinet's typical limits, lacks a definitive reference in the Fortinet SD-WAN Study Guide for FortiOS 7.2 to confirm '32' as the exact number, making it less certain than Option B.
Fortinet SD-WAN Study Guide for FortiOS 7.2, Section 3: Members, Zones, and Performance SLAs (description of interface types and zones).
Fortinet SD-WAN Study Guide for FortiOS 7.2, Section 4: Routing and Sessions (use of SD-WAN zones in static routes).
Fortinet Documentation: SD-WAN members and zones | FortiGate / FortiOS 7.2.4 (general behavior and flexibility of zones).
Which statement about using BGP routes in SD-WAN is true?
Answer : A
Which diagnostic command can you use to show the member utilization statistics measured by performance SLAs for the last 10 minutes?
Answer : A
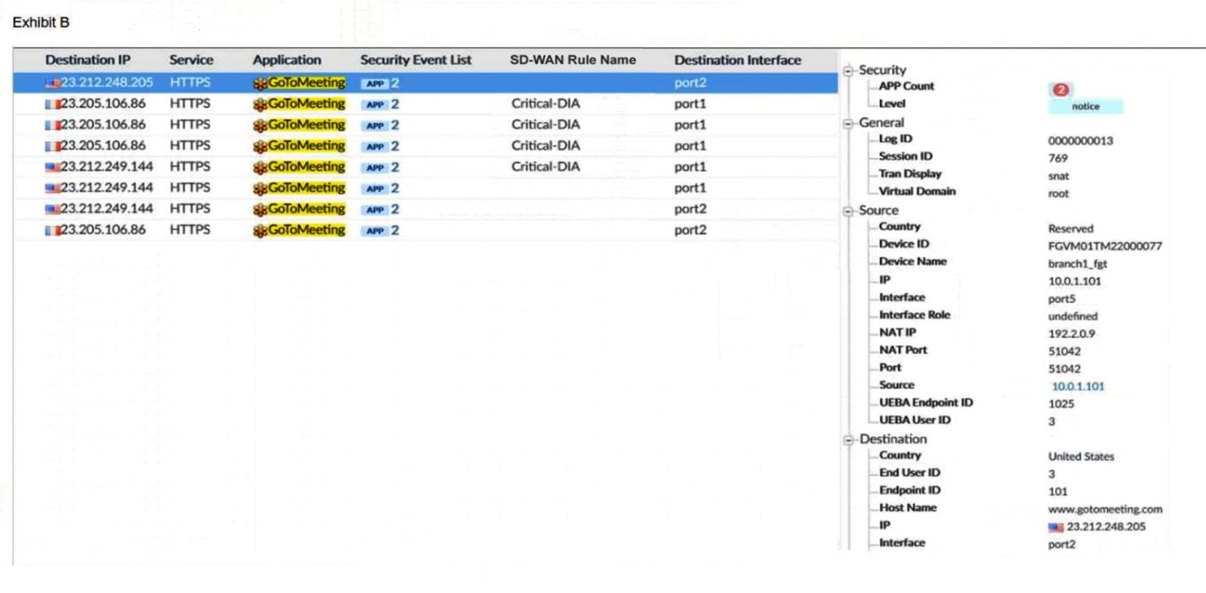
Refer to the exhibits.
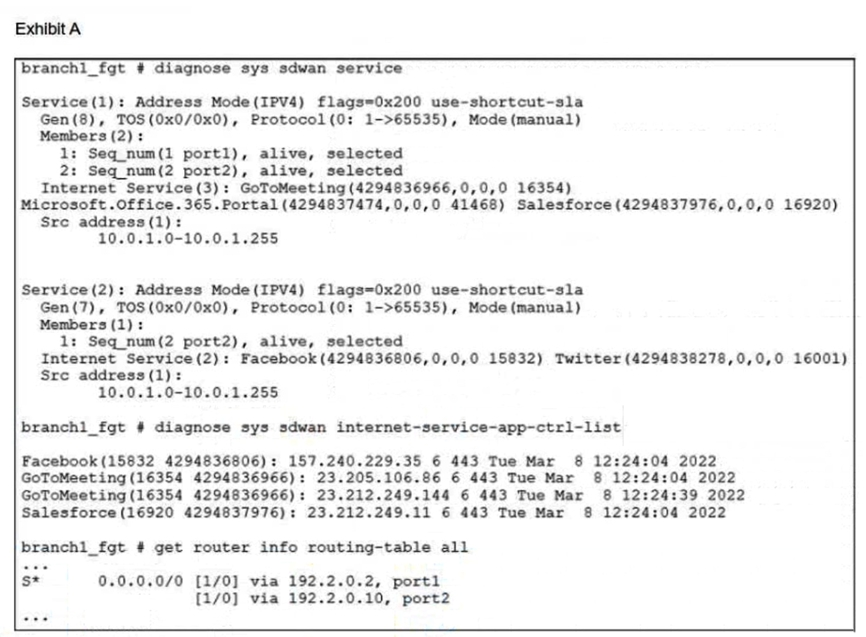
An administrator is testing application steering in SD-WAN. Before generating test traffic, the administrator collected the information shown in exhibit A.
After generating GoToMeeting test traffic, the administrator examined the respective traffic log on FortiAnalyzer, which is shown in exhibit B. The administrator noticed that the traffic matched the implicit SD-WAN rule, but they expected the traffic to match rule ID 1.
Which two reasons explain why the traffic matched the implicit SD-WAN rule? (Choose two.)
Answer : B, C
Study guide 7.2 Page 191
Refer to the exhibit.
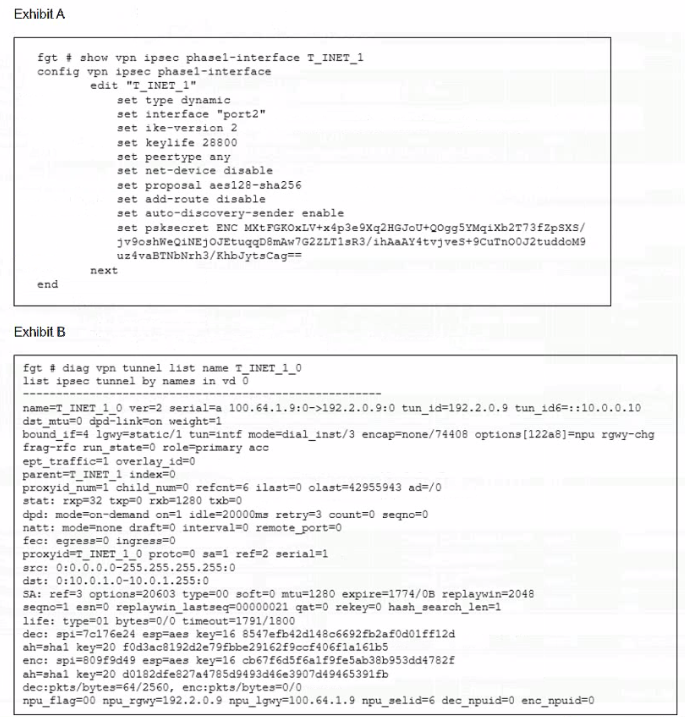
Which two statements about the IPsec VPN configuration and the status of the IPsec VPN tunnel are true? (Choose two.)
Answer : A, B
Refer to the exhibit.
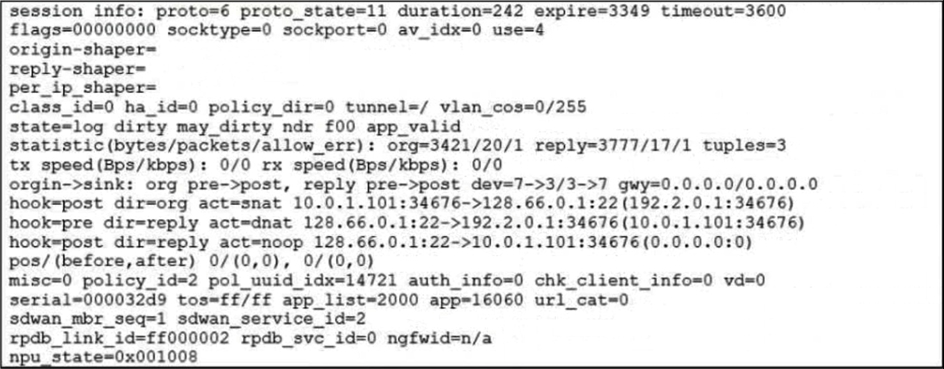
Which statement explains the output shown in the exhibit?
Answer : D
The snat-route-change option is enabled by default. This option enables FortiGate to re-evaluate the routing table and select a new egress interface if the next hop IP address changes. This option only applies to sessions in the dirty state. Sessions in the log state are not affected by routing changes.