GIAC Security Essentials Exam Practice Test
Open the MATE terminal and use the tcpdump program to read - /pcaps /cass tech.pcap.
What is the source port number?
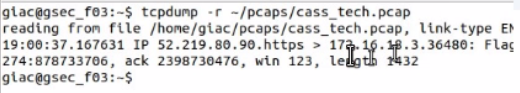
Answer : E
Which asymmetric algorithm is used only for key exchange?
Answer : B
Which of the following is a potential WPA3 security issue?
Answer : A
What cryptographic technique does file Integrity monitoring employ?
Answer : B
Which of the following consists of the security identifier number (SID) of your user account, the SID of all of your groups and a list of all your user rights?
Answer : C
An email system administrator deploys a configuration blocking all inbound and outbound executable files due to security concerns.
What Defense in Depth approach is being used?
Answer : C
What dots Office 365 use natively for authentication?
Answer : B, C