HP Designing Aruba Solutions HPE6-A47 Exam Questions
A Remote AP provisioned in "Split-Tunnel" Forwarding mode has which of the following characteristics?.
Answer : E
The corporation has deployed hundreds of RAP3 and all are working. A user has received a RAP3 from the IT department. At his home he connects the Ethernet port to his DSL modem. The corporate SSID is not advertises but an Instant SSID is. What could be the problem?
Answer : B
A customer needs a wired network solution that can recognize and prioritize a wide array of different types of
traffic, including casual Web browsing, voice, video, SAP Online, and file sharing.
The architect needs to choose between the Aruba 2930F or the 2540 Switch Series for the access layer
switch. Why would the architect choose the 2930F rather than the 2540 Switch Series for this customer?
Answer : D
A company purchased an indoor mesh deployment using the 7005 controller and the AP 115 models, where 5 APs will be deployed on a floor to provide wireless internet access for users. Users may open VPN tunnels using software clients over the wireless network to a 3rd party VPN concentrator overseas. The company wants to limit wireless user access to TCP traffic locally and VPN traffic overseas.
In addition to the base AOS, which licenses will be necessary for this deployment?
Answer : B
Refer to the exhibit.
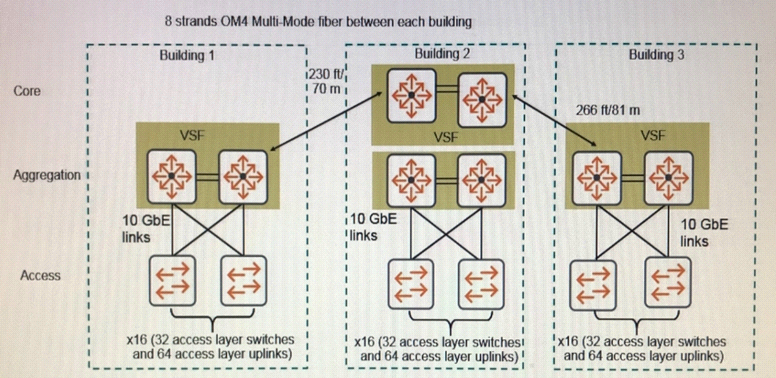
An architect selects 5406R switches for the aggregation layer. What is an appropriate amount of bandwidth for
the link aggregation between each aggregation layer VSF fabric and the campus core?
Answer : C
A Remote AP provisioned in "Split-Tunnel" Forwarding mode has which characteristic?
Answer : B
A plan includes these security settings for the employee WLAN:
1. WPA2-Enterprise with AES encryption
2. 802.1X with PEAP-MSCHAPv2
However, the customer wants to use certificates to authenticate user devices. Which change brings the plan in
alignment with the customer requirements?
Answer : D