HP Aruba Certified Network Security Expert Written HPE6-A84 Exam Practice Test
Refer to the scenario.
A customer has asked you to review their AOS-CX switches for potential vulnerabilities. The configuration for these switches is shown below:
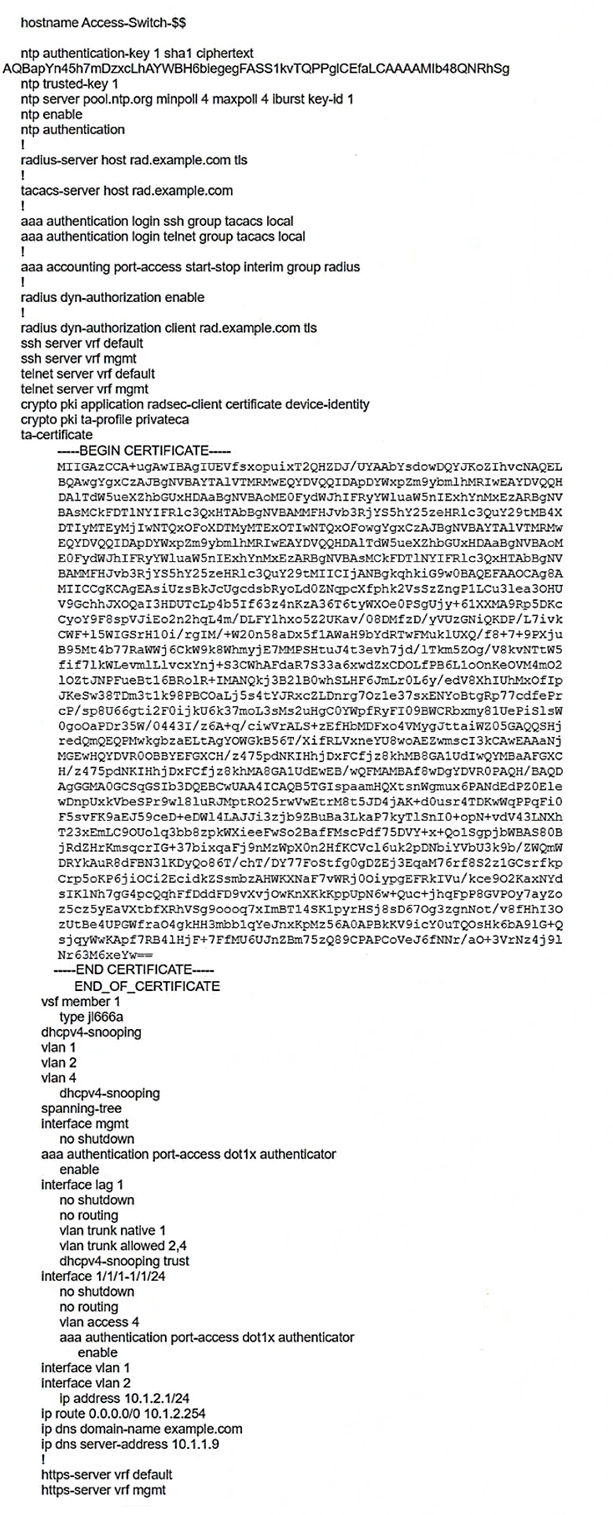
What is one immediate remediation that you should recommend?
Refer to the scenario.
A customer is using an AOS 10 architecture with Aruba APs and Aruba gateways (two per site). Admins have implemented auto-site clustering for gateways with the default gateway mode disabled. WLANs use tunneled mode to the gateways.
The WLAN security is WPA3-Enterprise with authentication to an Aruba ClearPass Policy Manager (CPPM) cluster VIP. RADIUS communications use RADIUS, not RadSec.
CPPM is using the service shown in the exhibits.
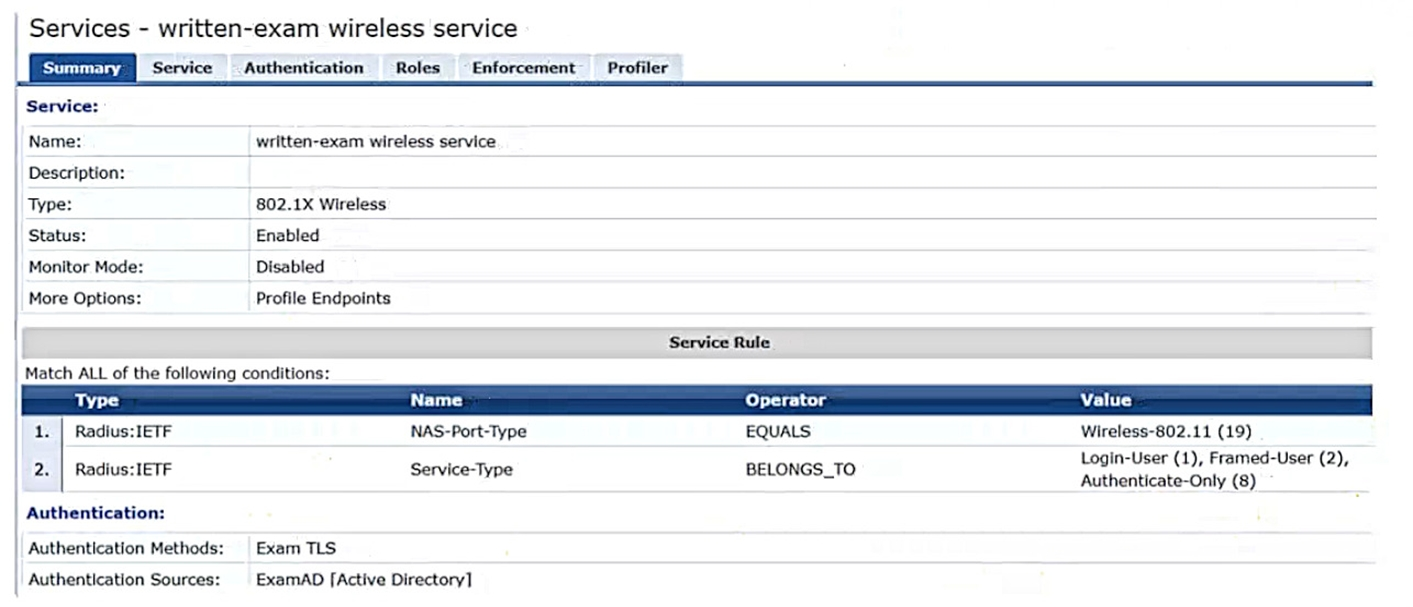
Which step can you take to improve operations during a possible gateway failover event?
Answer : B
Auto-site clustering is a feature that allows gateways in the same site and group to form a cluster automatically. However, this mode does not support VRRP IP addresses, which are required for dynamic authorization (CoA) from ClearPass Policy Manager (CPPM) to the gateways. Dynamic authorization is a mechanism that allows CPPM to change the attributes or status of a client session on the gateways without requiring re-authentication. This is useful for applying policies, roles, or bandwidth limits based on various conditions. Without VRRP IP addresses, CPPM would not be able to send CoA messages to the correct gateway in case of a failover event, resulting in inconsistent or incorrect client behavior.
To enable VRRP IP addresses for dynamic authorization, you need to set up gateway clusters manually and assign a VRRP VLAN and a VRRP IP address to each cluster. This way, CPPM can use the VRRP IP address as the NAS IP address for RADIUS communications and CoA messages. The VRRP IP address will remain the same even if the active gateway in the cluster changes due to a failover event, ensuring seamless operations. You can find more information about how to set up gateway clusters manually and configure VRRP IP addresses in the Gateway Cluster Deployment - Aruba page and the ClearPass Policy Manager User Guide1.
Refer to the scenario.
A customer requires these rights for clients in the ''medical-mobile'' AOS firewall role on Aruba Mobility Controllers (MCs):
External devices should not be permitted to initiate sessions with ''medical-mobile'' clients, only send return traffic.
The exhibits below show the configuration for the role.
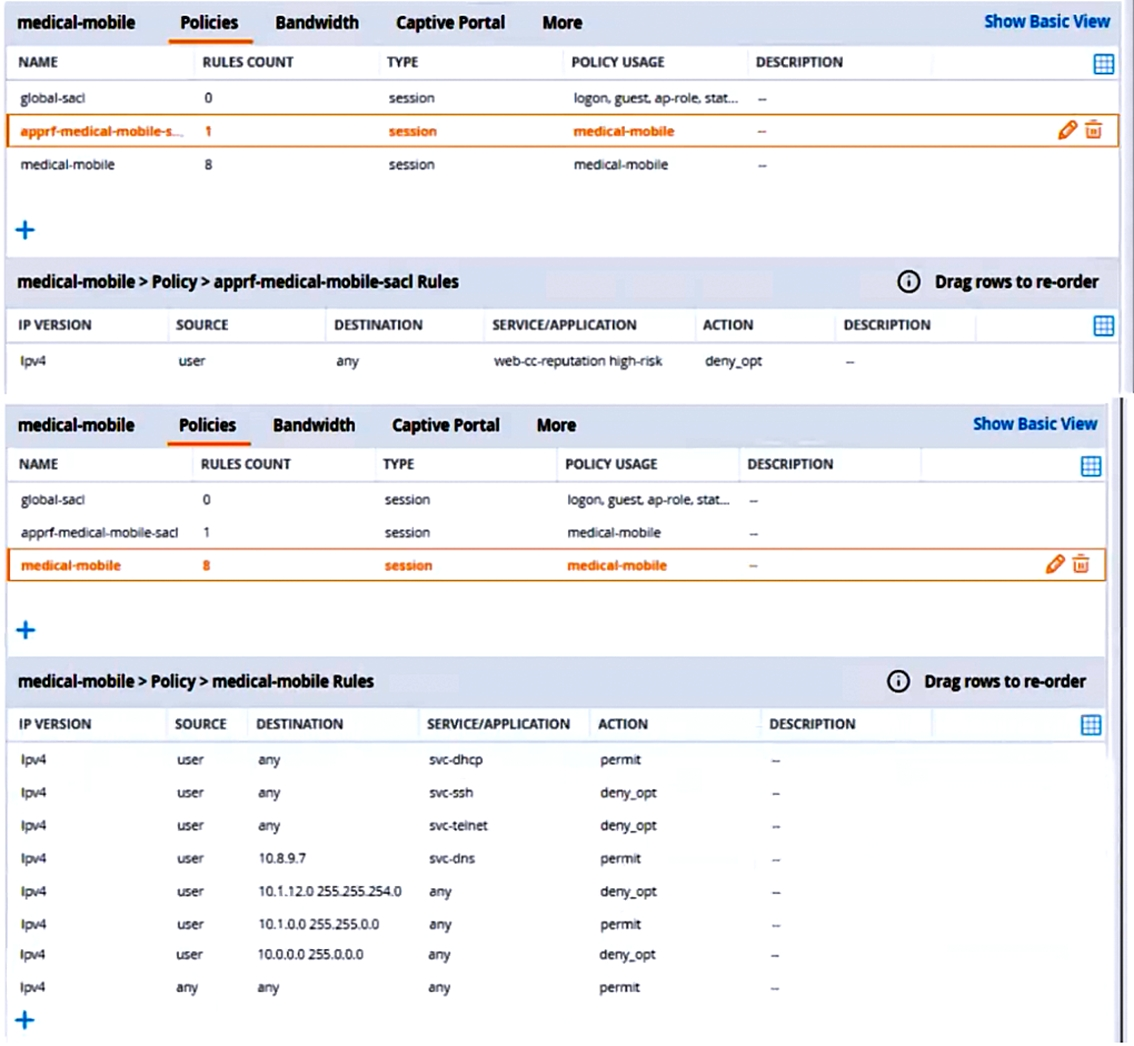
What setting not shown in the exhibit must you check to ensure that the requirements of the scenario are met?
Answer : C
To enable AppRF and WebCC, you need to check the following settings:
Refer to the exhibit.
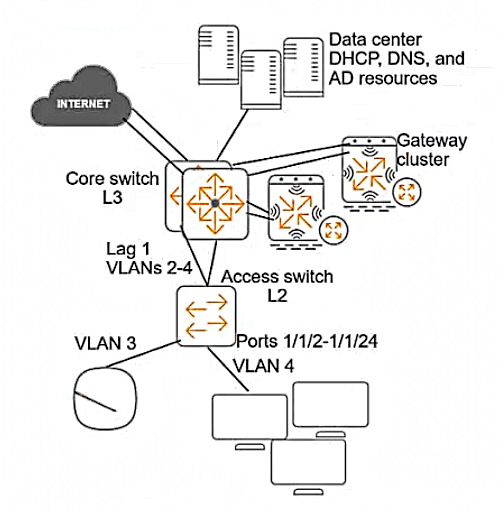
A customer requires protection against ARP poisoning in VLAN 4. Below are listed all settings for VLAN 4 and the VLAN 4 associated physical interfaces on the AOS-CX access layer switch:
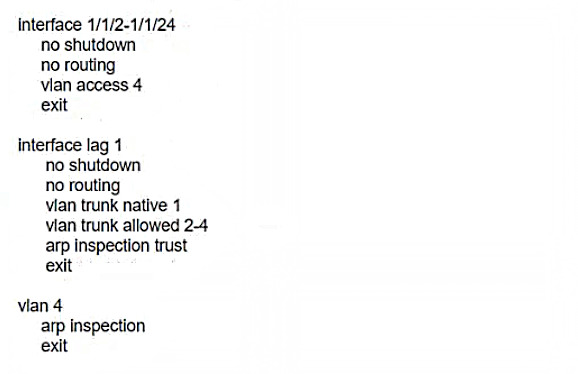
What is one issue with this configuration?
Answer : D
B) LAG 1 is configured as trusted for ARP inspection but should be untrusted. This is not an issue because LAG 1 connects to the core switch, which is a trusted device that does not send forged ARP packets.
Refer to the scenario.
A customer requires these rights for clients in the ''medical-mobile'' AOS firewall role on Aruba Mobility Controllers (MCs):
External devices should not be permitted to initiate sessions with ''medical-mobile'' clients, only send return traffic.
The exhibits below show the configuration for the role.
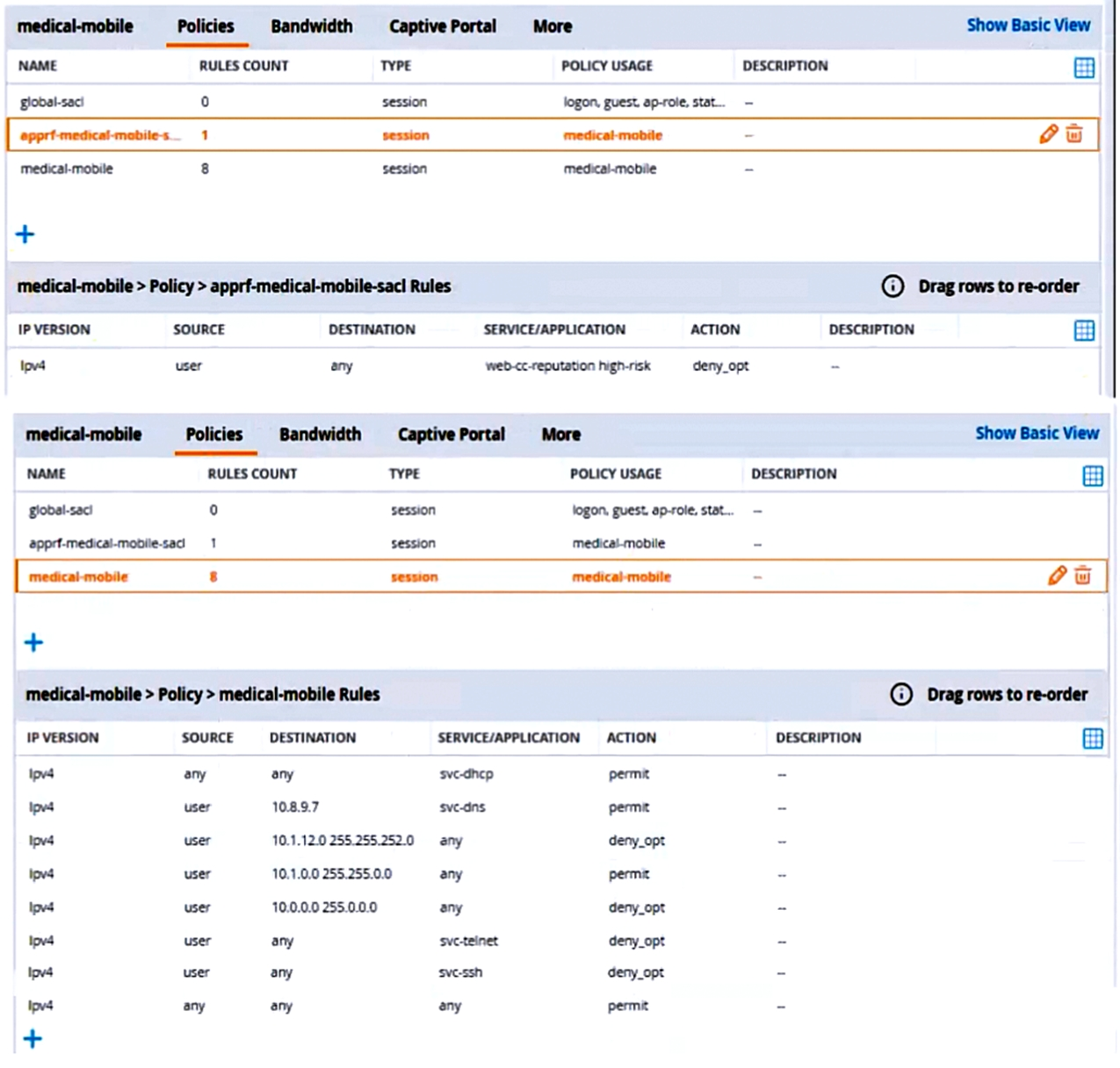
There are multiple issues with this configuration. What is one change you must make to meet the scenario requirements? (In the options, rules in a policy are referenced from top to bottom. For example, ''medical-mobile'' rule 1 is ''ipv4 any any svc-dhcp permit,'' and rule 8 is ''ipv4 any any any permit''.)
Answer : B
Refer to the exhibit.
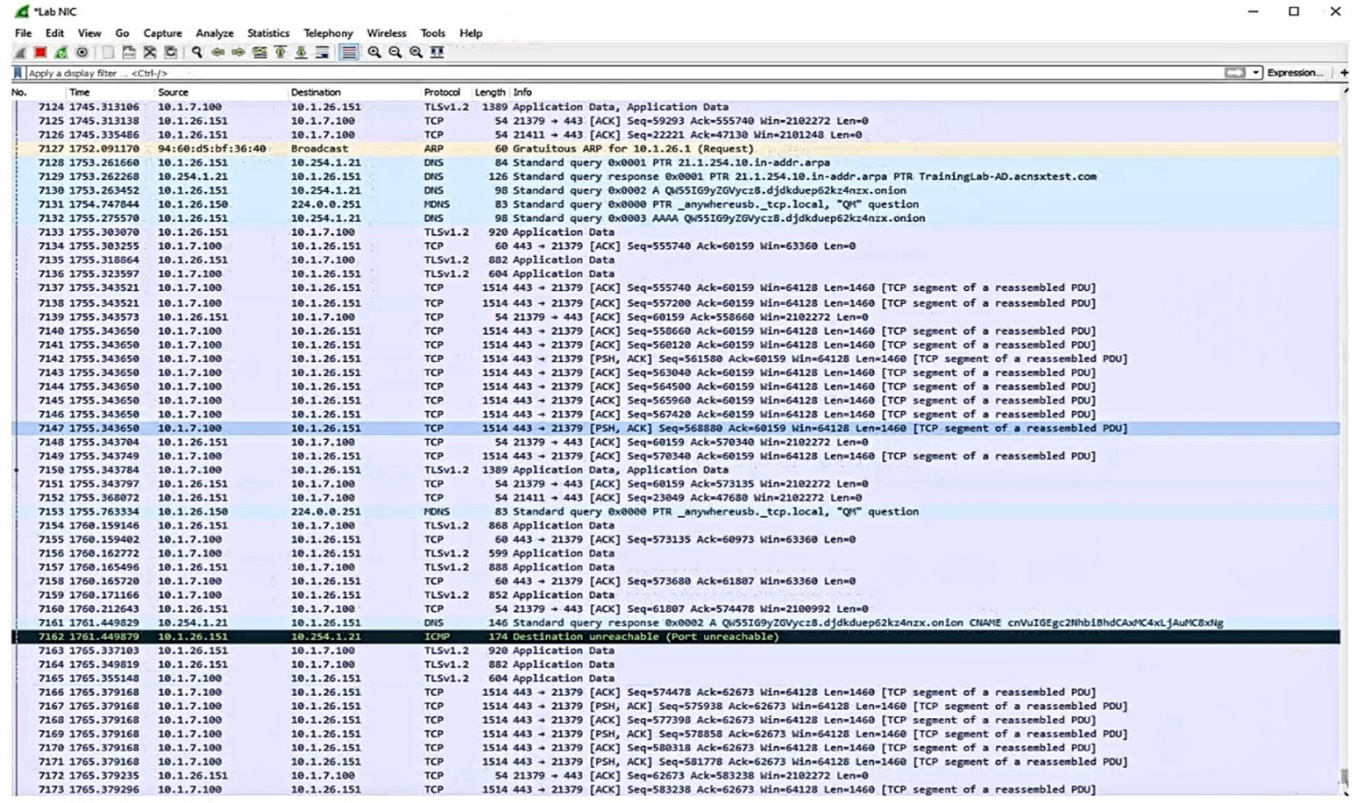
Which IP address should you record as a possibly compromised client?
Answer : A
The exhibit shows a screenshot of a Malwarebytes alert that indicates that a website was blocked due to compromise. The alert contains the following information:
The type of protection: Web Protection
The website that was blocked: 10.254.1.21
The port that was used: 80
The process that initiated the connection: C:\Program Files (x86)\Google\Chrome\Application\chrome.exe
The IP address of the device that initiated the connection: 10.1.26.151
The IP address of the device that initiated the connection is the one that should be recorded as a possibly compromised client, as it indicates that the device tried to access a malicious website that could infect it with malware or steal its data. In this case, the IP address of the possibly compromised client is 10.1.26.151.
You are designing an Aruba ClearPass Policy Manager (CPPM) solution for a customer. You learn that the customer has a Palo Alto firewall that filters traffic between clients in the campus and the data center.
Which integration can you suggest?