HP Aruba Certified Campus Access Mobility Expert Written HPE7-A07 Exam Practice Test
Your customer added third-party USB dongles to the USB ports of their AOS 10 access points. The customer uses AP-615 and AP-635 Each AP is connected with a Cat 6A cable to a CX 6300F Class 4 PoE switch All APs are in the same group in HPE Aruba Networking Central and share the same configuration However, many of the dongles do not come up.
Which option will solve this issue?
Answer : A
USB dongles often require additional power, which may exceed the power delivery capabilities of Class 4 PoE switches. Aruba AP-615 and AP-635 are designed to work with USB dongles that require additional power for proper operation. Since the Cat 6A cable can support higher power levels, replacing the Class 4 PoE switches with Class 6 PoE switches, which can deliver higher power, should resolve the issue with the dongles not powering up.
You configured" a bridged mode SSID with WPA3-Enterprise and EAP-TLS security. When you connect an Active Directory joined client that has valid client certificates. ClearPass shows the following error.
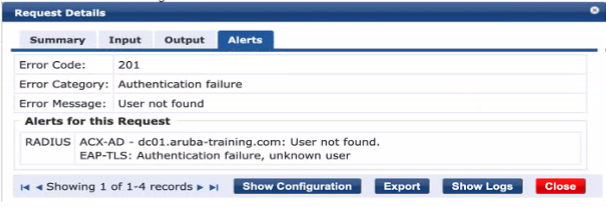
What is needed to resolve this issue?
Answer : C
The error message 'User not found' indicates that the authentication source, in this case, Active Directory (AD), is not able to locate the user account based on the current search parameters. This often occurs when the User Principal Name (UPN) that the client is using to authenticate is not included in the search parameters of the AD authentication source within ClearPass. By modifying the AD authentication source to include the UPN in the search, ClearPass will be able to correctly locate the user account and proceed with the authentication using the valid client certificates.
You configured a WPA3-SAE with the following MAC Authentication Role Mapping in Cloud Authentication and Policy:
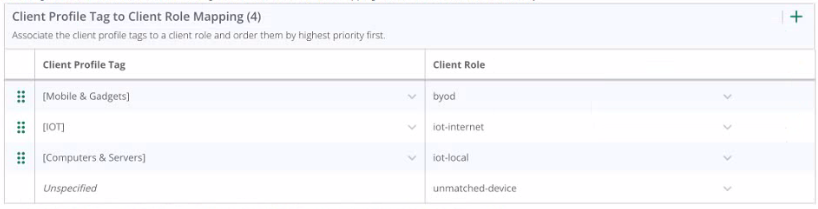
With further default settings assume a new Android phone is connected to the network. Which role will the client be assigned after connecting for the first time?
Answer : D
The configuration shown in the third exhibit details a client role mapping that associates different client profile tags with specific client roles. When a new device, such as an Android phone, connects to the network, it will be profiled and assigned a role based on the mappings defined. If the device does not match any predefined profiles, it would be assigned the 'unmatched-device' role. This is under the assumption that default settings are in place and the client does not match the criteria for any of the specific roles like 'byod', 'iot-internet', or 'iot-local'. Therefore, an Android phone connecting for the first time and not matching any specific profile tag would be assigned to the 'unmatched-device' role.
Which command would allow you to verity receipt of a CoA message on an AOS 10 GW?
Answer : B
The Change of Authorization (CoA) messages are used in network access control scenarios and are typically received by the network access server, in this case, an Aruba AOS 10 Gateway. The correct command to verify the receipt of a CoA message is related to the control path traffic because CoA is a control plane function.
Option B, packet-capture controlpath udp 3799, is the correct answer because it specifies capturing control plane traffic on UDP port 3799, which is the standard port for CoA messages.
Options A, C, and D are incorrect because:
Option A captures data plane traffic, not control plane traffic.
Option C's packet-capture interprocess udp 3799 does not refer to a standard command for capturing CoA messages.
Option D, tcpdump host-port 3799, does not specify the correct syntax for capturing traffic on Aruba devices.
An ACME company employee complained about a recent poor-quality VoIP call while moving around their office environment HPE Aruba Networking Central reported a fair UCC score for this call while your VoIP engineer reported that their systems reported a MOS of 2, 3. The VoIP devices are operating over the 5GHz frequency band.
What are the possible contributing factors? (Select two.)
Answer : A, E
VoIP quality can be negatively impacted by insufficient cell overlap in AP deployment plans, which can cause poor handoffs between APs as a user moves around. This results in a degraded VoIP experience. Additionally, roaming into an area with continuous Zigbee operation can cause interference with the 5GHz frequency band, further contributing to poor VoIP call quality. The Zigbee communication protocol operates on the same frequency band as Wi-Fi and can introduce noise and interference, which leads to a reduced MOS score, as reported by the VoIP engineer.
Which data transmission method provides the most efficient use of airtime for VoIP traffic?
Answer : C
MU-MIMO (Multi-User, Multiple Input, Multiple Output) provides the most efficient use of airtime for VoIP traffic among the options listed. MU-MIMO allows multiple users to receive multiple data streams simultaneously, improving the overall efficiency of the network, especially in dense environments where VoIP applications need consistent and reliable connectivity.
A BGP routing table contains multiple routes to the same destination prefix.
Referring to the table below which route would be marked with a ">" symbol?
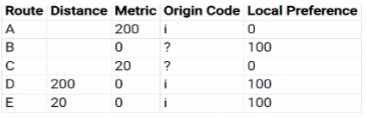
Answer : E
In BGP, the route marked with a '>' symbol is the best route that is chosen based on BGP attributes in the following order: highest weight (Cisco-specific), highest local preference, originated by BGP running on the local router, shortest AS path, lowest origin type, lowest MED, eBGP over iBGP, closest IGP neighbor, and lowest BGP router ID. Based on the table provided, Option E would be marked with a '>' symbol as it has the highest local preference of 100 which is a decisive factor in the BGP best path selection process.