Huawei HCIP-Security-CISN V3.0 H12-721 HCIP-Security-CISN Exam Practice Test
By default, GigabitEthernet0/0/0 can be used as an out-of-band management interface in the USG2200 series.
Answer : B
Note: Can be used as an in-band management interface. In-band management: The management control information of the network and the bearer service information of the user network are transmitted through the same logical channel. Out-of-band management: The management control information of the network and the bearer service information of the user network are transmitted on different logical channels.
Accessing the headquarters server through the IPSec VPN from the branch computer. The IPSec tunnel can be established normally, but the service is unreachable. What are the possible reasons?
Answer : A
A user wants to limit the maximum bandwidth of the 192.168.1.0/24 network segment to 500M, and limit all IP addresses in the network segment to maintain a bandwidth of 1M. How should I configure a current limiting policy for this requirement?
Answer : D
In dual-system hot backup, the backup channel must be the primary interface on the interface board. Which type is not supported?
Answer : C
The PC A in the Trust zone is 192.168.3.1. You cannot access the Internet server in the Untrust zone. The configuration between the Trust zone and the Untrust zone is as follows. What are the most likely causes of the following faults?
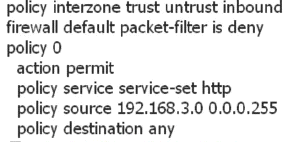
Answer : A
With regard to the Radius agreement, what are the following statements correct?
Answer : A, B, D
As shown in the figure, the Eth-trunk function is required to bind the interface. On this basis, if you need to implement the load balancing function of each interface, you need to add the following configuration command?
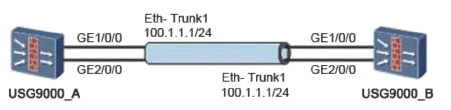
Answer : B