Huawei H12-722 HCIP-Security-CSSN V3.0 HCIP-Security-CSSN Exam Practice Test
Which of the following descriptions about the black and white lists in spam filtering is wrong? c
Answer : D
The realization of content security filtering technology requires the support of the content security combination license.
Answer : A
155955cc-666171a2-20fac832-0c042c0426
Abnormal detection is to establish the normal behavior characteristic profile of the system subject through the analysis of the audit data of the system: check if the audit data in the system
If there is a big discrepancy with the normal behavior characteristics of the established subject, it is considered an intrusion. Nasu must be used as the system subject? (multiple choice)
Answer : A, B, C, D
Which of the following threats cannot be detected by IPS?
Answer : C
Which of the following options is not a special message attack?
Answer : D
Regarding HTTP behavior, which of the following statements is wrong?
Answer : D
An enterprise administrator configures the Web reputation system as shown in the figure. Regarding the configuration, which of the following statements is correct?
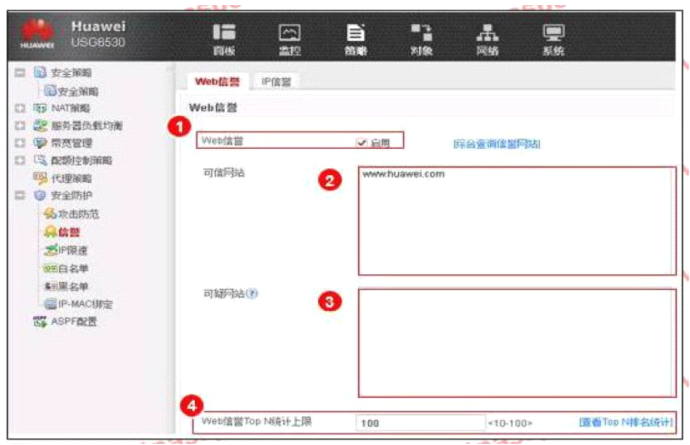
Answer : B