Juniper Cloud, Associate JN0-214 JNCIA-Cloud Exam Questions
Click to the Exhibit button.
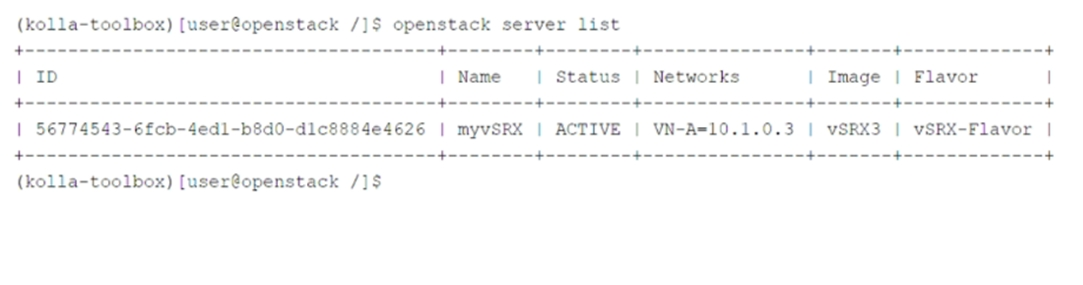
Referring to the exhibit, which two statements are correct? (Choose two.)
Answer : C, D
The openstack server list command provides information about virtual machine (VM) instances in the OpenStack environment. Let's analyze the exhibit and each statement:
Key Information from the Exhibit:
The output shows details about the myvSRX instance:
Status: ACTIVE (indicating the instance is running).
Networks: VN-A-10.1.0.3 (indicating the instance is part of a specific network).
Image: vSRX3 (indicating the instance was created using a custom image).
Flavor: vSRX-Flavor (indicating the instance was created using a custom flavor).
Option Analysis:
A . The myvSRX instance is using a default image.
Incorrect: The image name vSRX3 suggests that this is a custom image, not the default image provided by OpenStack.
B . The myvSRX instance is a part of a default network.
Incorrect: The network name VN-A-10.1.0.3 indicates that the instance is part of a specific network, not the default network.
C . The myvSRX instance is created using a custom flavor.
Correct: The flavor name vSRX-Flavor indicates that the instance was created using a custom flavor, which defines the CPU, RAM, and disk space properties.
D . The myvSRX instance is currently running.
Correct: The ACTIVE status confirms that the instance is currently running.
Why These Statements?
Custom Flavor: The vSRX-Flavor name clearly indicates that a custom flavor was used to define the instance's resource allocation.
Running Instance: The ACTIVE status confirms that the instance is operational and available for use.
JNCIA Cloud Reference:
The JNCIA-Cloud certification emphasizes understanding OpenStack commands and outputs, including the openstack server list command. Recognizing how images, flavors, and statuses are represented is essential for managing VM instances effectively.
For example, Juniper Contrail integrates with OpenStack Nova to provide advanced networking features for VMs, ensuring seamless operation based on their configurations.
OpenStack CLI Documentation: openstack server list Command
Juniper JNCIA-Cloud Study Guide: OpenStack Compute
Which cloud service model provides access to networking, storage, servers, and virtualization in a cloud environment?
Answer : C
Cloud service models define how services are delivered and managed in a cloud environment. The three primary models are:
Infrastructure as a Service (IaaS): Provides virtualized computing resources such as servers, storage, networking, and virtualization over the internet. Customers manage their own operating systems, applications, and data, while the cloud provider manages the underlying infrastructure.
Platform as a Service (PaaS): Provides a platform for developers to build, deploy, and manage applications without worrying about the underlying infrastructure. Examples include Google App Engine and Microsoft Azure App Services.
Software as a Service (SaaS): Delivers fully functional applications over the internet, eliminating the need for users to install or maintain software locally. Examples include Salesforce CRM, Google Workspace, and Microsoft Office 365.
Database as a Service (DaaS): A specialized subset of PaaS that provides managed database services.
In this question, the focus is on access to networking, storage, servers, and virtualization , which are the core components of IaaS . IaaS allows customers to rent infrastructure on-demand and build their own environments without investing in physical hardware.
Why IaaS?
Flexibility: Customers have full control over the operating systems, applications, and configurations.
Scalability: Resources can be scaled up or down based on demand.
Cost Efficiency: Pay-as-you-go pricing eliminates upfront hardware costs.
JNCIA Cloud Reference:
The JNCIA-Cloud certification emphasizes understanding the different cloud service models and their use cases. IaaS is particularly relevant for organizations that want to leverage cloud infrastructure while maintaining control over their applications and data.
For example, Juniper Contrail integrates with IaaS platforms like OpenStack to provide advanced networking and security features for virtualized environments.
NIST Cloud Computing Reference Architecture
Juniper JNCIA-Cloud Study Guide: Cloud Service Models
Which two statements are correct about cloud computing? (Choose two.)
Answer : B, D
Cloud computing is a model for delivering IT services where resources are provided over the internet on-demand. Let's analyze each statement:
A . Cloud computing eliminates operating expenses.
Incorrect: While cloud computing can reduce certain operating expenses (e.g., hardware procurement, maintenance), it does not eliminate them entirely. Organizations still incur costs such as subscription fees, data transfer charges, and operational management of cloud resources. Additionally, there may be costs associated with training staff or migrating workloads to the cloud.
B . Cloud computing has the ability to scale elastically.
Correct: Elasticity is one of the key characteristics of cloud computing. It allows resources (e.g., compute, storage, networking) to scale up or down automatically based on demand. For example, during peak usage, additional virtual machines or storage can be provisioned dynamically, and when demand decreases, these resources can be scaled back. This ensures efficient resource utilization and cost optimization.
C . Cloud computing increases the physical control of the data resources.
Incorrect: Cloud computing typically reduces physical control over data resources because the infrastructure is managed by the cloud provider. For example, in public cloud models, the customer does not have direct access to the physical servers or data centers. Instead, they rely on the provider's security and compliance measures.
D . Cloud computing allows access to data any time from any location through the Internet.
Correct: One of the core advantages of cloud computing is ubiquitous access. Users can access applications, services, and data from anywhere with an internet connection. This is particularly beneficial for remote work, collaboration, and global business operations.
JNCIA Cloud Reference:
The Juniper Networks Certified Associate - Cloud (JNCIA-Cloud) curriculum highlights the key characteristics of cloud computing, including elasticity, scalability, and ubiquitous access. These principles are foundational to understanding how cloud environments operate and how they differ from traditional on-premises solutions.
For example, Juniper Contrail, a software-defined networking (SDN) solution, leverages cloud elasticity to dynamically provision and manage network resources in response to changing demands. Similarly, the ability to access cloud resources remotely aligns with Juniper's focus on enabling flexible and scalable cloud architectures.
NIST Definition of Cloud Computing
Juniper JNCIA-Cloud Study Guide: Cloud Characteristics
Your organization manages all of its sales through the Salesforce CRM solution.
In this scenario, which cloud service model are they using?
Answer : B
Cloud service models define how services are delivered and managed in a cloud environment. The three primary models are:
Infrastructure as a Service (IaaS): Provides virtualized computing resources such as servers, storage, and networking over the internet. Examples include Amazon EC2 and Microsoft Azure Virtual Machines.
Platform as a Service (PaaS): Provides a platform for developers to build, deploy, and manage applications without worrying about the underlying infrastructure. Examples include Google App Engine and Microsoft Azure App Services.
Software as a Service (SaaS): Delivers fully functional applications over the internet, eliminating the need for users to install or maintain software locally. Examples include Salesforce CRM, Google Workspace, and Microsoft Office 365.
In this scenario, the organization is using Salesforce CRM, which is a SaaS solution. Salesforce provides a complete customer relationship management (CRM) application that is accessible via a web browser, with no need for the organization to manage the underlying infrastructure or application code.
Why SaaS?
No Infrastructure Management: The customer does not need to worry about provisioning servers, databases, or networking components.
Fully Managed Application: Salesforce handles updates, patches, and maintenance, ensuring the application is always up-to-date.
Accessibility: Users can access Salesforce CRM from any device with an internet connection.
JNCIA Cloud Reference:
The JNCIA-Cloud certification emphasizes understanding the different cloud service models and their use cases. SaaS is particularly relevant in scenarios where organizations want to leverage pre-built applications without the complexity of managing infrastructure or development platforms.
For example, Juniper's cloud solutions often integrate with SaaS platforms like Salesforce to provide secure connectivity and enhanced functionality. Understanding the role of SaaS in cloud architectures is essential for designing and implementing cloud-based solutions.
Juniper JNCIA-Cloud Study Guide: Cloud Service Models
Salesforce CRM Documentation
You are asked to run a container in a Kubernetes environment.
What should you do to accomplish this task?
Answer : C
Kubernetes uses declarative configuration files to define and manage resources like containers, pods, and services. Let's analyze each option:
A . Create a JINJA2 template for the container and its resources.
Incorrect: JINJA2 is a templating language often used in automation tools like Ansible. While it can generate Kubernetes manifests, Kubernetes itself does not use JINJA2 templates natively.
B . Create a WYSYG definition for the container and its resources.
Incorrect: 'WYSYG' (What You See Is What You Get) is not a recognized format for Kubernetes configurations. Kubernetes relies on structured formats like YAML or JSON.
C . Define a YAML manifest for the container and its resources.
Correct: Kubernetes uses YAML (or JSON) manifests to define the desired state of resources, including containers, pods, and services. A YAML manifest specifies details like container images, resource limits, environment variables, and networking.
D . Define an XML configuration for the container and its resources.
Incorrect: Kubernetes does not use XML for defining resources. YAML is the standard format due to its readability and simplicity.
Why YAML Manifests?
Declarative Configuration: YAML manifests allow you to describe the desired state of your resources in a human-readable format.
Standard Practice: Kubernetes natively supports YAML for defining and deploying resources, making it the correct choice for this task.
JNCIA Cloud Reference:
The JNCIA-Cloud certification emphasizes Kubernetes resource management, including YAML manifests. Understanding how to define and apply manifests is essential for deploying and managing containerized applications.
For example, Juniper Contrail integrates with Kubernetes to provide advanced networking features, relying on YAML manifests to configure resources.
Kubernetes Documentation: YAML Manifests
Juniper JNCIA-Cloud Study Guide: Kubernetes Resource Management
What is the name of the Docker container runtime?
Answer : B
Docker is a popular containerization platform that relies on a container runtime to manage the lifecycle of containers. The container runtime is responsible for tasks such as creating, starting, stopping, and managing containers. Let's analyze each option:
A . docker_cli
Incorrect: The Docker CLI (Command Line Interface) is a tool used to interact with the Docker daemon (dockerd). It is not a container runtime but rather a user interface for managing Docker containers.
B . containerd
Correct: containerd is the default container runtime used by Docker. It is a lightweight, industry-standard runtime that handles low-level container management tasks, such as image transfer, container execution, and lifecycle management. Docker delegates these tasks to containerd through the Docker daemon.
C . dockerd
Incorrect: dockerd is the Docker daemon, which manages Docker objects such as images, containers, networks, and volumes. While dockerd interacts with the container runtime, it is not the runtime itself.
D . cri-o
Incorrect: cri-o is an alternative container runtime designed specifically for Kubernetes. It implements the Kubernetes Container Runtime Interface (CRI) and is not used by Docker.
Why containerd?
Industry Standard: containerd is a widely adopted container runtime that adheres to the Open Container Initiative (OCI) standards.
Integration with Docker: Docker uses containerd as its default runtime, making it the correct answer in this context.
JNCIA Cloud Reference:
The JNCIA-Cloud certification emphasizes understanding containerization technologies and their components. Docker and its runtime (containerd) are foundational tools in modern cloud environments, enabling lightweight, portable, and scalable application deployment.
For example, Juniper Contrail integrates with container orchestration platforms like Kubernetes, which often use containerd as the underlying runtime. Understanding container runtimes is essential for managing containerized workloads in cloud environments.
Docker Documentation: Container Runtimes
Open Container Initiative (OCI) Standards
Juniper JNCIA-Cloud Study Guide: Containerization
Which command would you use to see which VMs are running on your KVM device?
Answer : C
KVM (Kernel-based Virtual Machine) is a popular open-source virtualization technology that allows you to run virtual machines (VMs) on Linux systems. The virsh command-line tool is used to manage KVM VMs. Let's analyze each option:
A . virt-install
Incorrect: The virt-install command is used to create and provision new virtual machines. It is not used to list running VMs.
B . virsh net-list
Incorrect: The virsh net-list command lists virtual networks configured in the KVM environment. It does not display information about running VMs.
C . virsh list
Correct: The virsh list command displays the status of virtual machines managed by the KVM hypervisor. By default, it shows only running VMs. You can use the --all flag to include stopped VMs in the output.
D . VBoxManage list runningvms
Incorrect: The VBoxManage command is used with Oracle VirtualBox, not KVM. It is unrelated to KVM virtualization.
Why virsh list?
Purpose-Built for KVM: virsh is the standard tool for managing KVM virtual machines, and virsh list is specifically designed to show the status of running VMs.
Simplicity: The command is straightforward and provides the required information without additional complexity.
JNCIA Cloud Reference:
The JNCIA-Cloud certification emphasizes understanding virtualization technologies, including KVM. Managing virtual machines using tools like virsh is a fundamental skill for operating virtualized environments.
For example, Juniper Contrail supports integration with KVM hypervisors, enabling the deployment and management of virtualized network functions (VNFs). Proficiency with KVM tools ensures efficient management of virtualized infrastructure.
KVM Documentation: virsh Command
Juniper JNCIA-Cloud Study Guide: Virtualization