Juniper Data Center, Associate JN0-281 Exam Practice Test
Which Junos OS routing table stores IPv6 addresses?
Answer : D
In Junos OS, routing information is stored in different routing tables depending on the protocol and address family. For IPv6 addresses, the routing table used is inet6.0.
Step-by-Step Explanation:
Routing Tables in Junos:
inet.0: This is the primary routing table for IPv4 unicast routes.
inet6.0: This is the primary routing table for IPv6 unicast routes.
inet.3: This routing table is used for MPLS-related routing.
Other routing tables, like inet.1, inet.2, are used for multicast and other specific purposes.
inet6.0 Routing Table:
When IPv6 is enabled on a Juniper router, all the IPv6 routes are stored in the inet6.0 table. This includes both direct routes (connected networks) and learned routes (from dynamic routing protocols like OSPFv3, BGP, etc.).
Verification:
To view IPv6 routes, the command show route table inet6.0 is used. This will display the contents of the IPv6 routing table, showing the network prefixes, next-hop addresses, and protocol information for each route.
Juniper Reference:
Junos Command: Use show route table inet6.0 to check IPv6 routing entries.
IPv6 Routing: Ensure that the IPv6 protocol is enabled on interfaces and that routing protocols like OSPFv3 or BGP are properly configured for IPv6 traffic handling.
You are troubleshooting a downed BGP session.
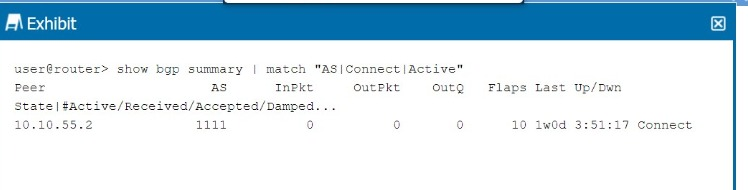
Referring to the exhibit, what is the cause of the problem?
Answer : C
The BGP session in the exhibit shows the state as Connect, which indicates that the TCP session between the BGP peers has not been fully established.
Step-by-Step Breakdown:
BGP State 'Connect':
The Connect state is the second stage in the BGP finite state machine (FSM). At this stage, BGP is trying to establish a TCP session with the peer, but the session has not yet been successfully established.
A successful TCP three-way handshake (SYN, SYN-ACK, ACK) is required before BGP can progress to the OpenSent state, where the peers exchange BGP Open messages.
Possible Causes:
A firewall blocking TCP port 179.
Incorrect IP addresses or network connectivity issues between the BGP peers.
Juniper Reference:
BGP Troubleshooting: In Junos, if a BGP session is stuck in the Connect state, the issue is likely due to a failure in establishing the underlying TCP connection.
Exhibit:
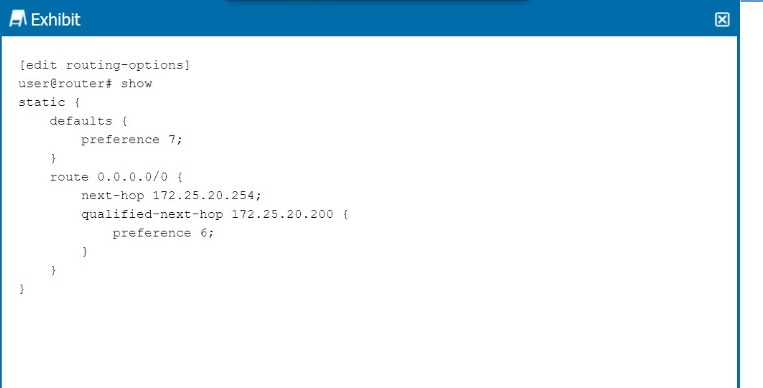
Referring to the exhibit, which next hop will be preferred in the routing table?
Answer : C
In the exhibit, we see a static route configuration with two possible next hops for the default route (0.0.0.0/0):
next-hop 172.25.20.254 with the default preference of 7.
qualified-next-hop 172.25.20.200 with a preference of 6.
Step-by-Step Breakdown:
Preference Value:
In Junos OS, the preference value is used to determine which route should be preferred in the routing table. The lower the preference value, the higher the priority for the route.
Comparison:
In this case:
The next hop 172.25.20.254 has a preference of 7.
The qualified-next-hop 172.25.20.200 has a preference of 6.
Preferred Next Hop:
Since 172.25.20.200 has a lower preference (6) compared to 172.25.20.254 (7), it will be the preferred next hop in the routing table, assuming both next hops are reachable.
Juniper Reference:
Qualified Next Hop: In Junos, static routes with multiple next-hop options are selected based on the preference value, with the lower value being preferred.
What is the behavior of the default export policy for OSPF?
Answer : B
In Junos, the default export policy for OSPF is to reject all routes from being exported.
Step-by-Step Breakdown:
Default Export Policy:
By default, OSPF in Junos does not export any routes to other routing protocols or neighbors. This is a safety mechanism to prevent unintended route advertisements.
Custom Export Policies:
If you need to export routes, you must create a custom export policy that explicitly defines which routes to advertise.
Example: You can create an export policy to redistribute static or connected routes into OSPF.
Juniper Reference:
OSPF Export Behavior: In Juniper devices, the default policy for OSPF is to reject route advertisements unless explicitly configured otherwise through custom policies.
MACsec provides protection against which two types of threats? (Choose two.)
Answer : B, D
MACsec (Media Access Control Security) provides data confidentiality, integrity, and origin authenticity at Layer 2, protecting against several types of threats.
Step-by-Step Breakdown:
Man-in-the-Middle Attack Protection:
MACsec encrypts traffic at Layer 2, preventing man-in-the-middle attacks where an attacker intercepts and manipulates traffic between two communicating devices. Since the data is encrypted, any intercepted packets are unreadable.
Protection Against Playback Attacks:
MACsec also protects against playback attacks by using sequence numbers and timestamps to ensure that old, replayed packets are not accepted by the receiver.
Juniper Reference:
MACsec Configuration: Juniper devices support MACsec for securing Layer 2 communications, ensuring protection against replay and man-in-the-middle attacks in sensitive environments.
Referring to the exhibit, why are the BGP routes hidden?
Answer : C
In the exhibit, the BGP routes are marked as hidden. This typically happens when the routes are not considered valid for use, but they remain in the routing table for reference. One common reason for BGP routes being hidden is that the next hop for these routes is unreachable.
Step-by-Step Breakdown:
BGP Next Hop:
In BGP, when a route is received from a neighbor, the next hop is the IP address that must be reachable for the route to be used. If the next hop is unreachable (i.e., the router cannot find a path to the next-hop IP), the route is marked as hidden.
Analyzing the Exhibit:
The exhibit shows that the BGP next hop for all hidden routes is 10.4.4.4. If this IP is unreachable, the BGP routes from that neighbor will not be considered valid, even though they appear in the routing table.
Verification:
Use the command show route 10.4.4.4 to check if the next-hop IP is reachable.
If the next-hop is not reachable, the BGP routes will be hidden. Resolving the next-hop reachability issue (e.g., fixing an IGP route or an interface) will allow the BGP routes to become active.
Juniper Reference:
Junos Command: show route hidden displays routes that are not considered for forwarding.
Troubleshooting: Check the next hop reachability for hidden BGP routes using show route <next-hop>.
Which statement is correct about areas in OSPF?
Answer : C
In OSPF (Open Shortest Path First), areas are used to segment a network into smaller, more manageable pieces to improve scalability. By dividing a network into areas, OSPF can reduce the size of the link-state database (LSDB), which helps routers process updates more efficiently.
Step-by-Step Breakdown:
Purpose of OSPF Areas:
OSPF areas allow for hierarchical routing within the OSPF domain. Routers in the same area have identical LSDBs, but routers in different areas do not exchange full link-state information. Instead, they exchange summarized routes, which reduces the LSDB size and CPU/memory usage.
Benefits:
Reducing the LSDB size improves scalability and ensures faster convergence in larger networks. Area 0 is the backbone area, and all other areas must connect to it, forming a hierarchical structure.
Juniper Reference:
OSPF Configuration: Areas in OSPF are configured to optimize network performance by limiting the scope of link-state advertisements (LSAs) to within an area.