Juniper Security, Specialist JN0-335 Exam Practice Test
You are asked to implement IPS on your SRX Series device.
In this scenario, which two tasks must be completed before a configuration will work? (Choose two.)
Answer : A, C
The two tasks that must be completed before a configuration for IPS on an SRX Series device will work are downloading the IPS signature database and installing the IPS signature database. The Security, Specialist (JNCIS-SEC) Study guide provides further information on how to download and install the IPS signature database. Enrolling the SRX Series device with Juniper ATP Cloud is not necessary to make a configuration work, and rebooting the SRX Series device is not required either.
Exhibit
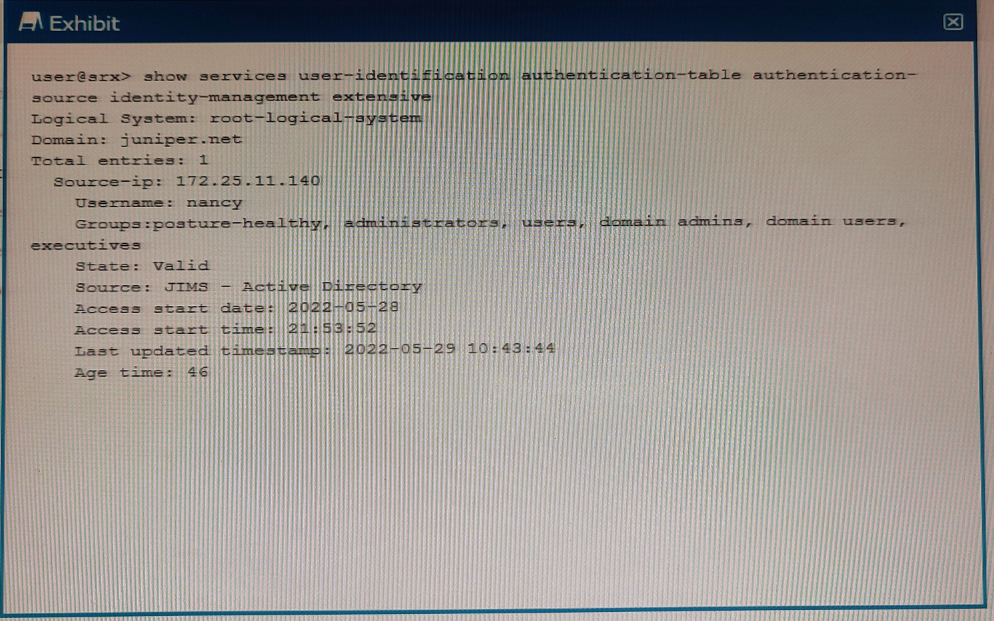
Referring to the exhibit, which two statements are true? (Choose two.)
Answer : C
You want to use IPS signatures to monitor traffic.
Which module in the AppSecure suite will help in this task?
Answer : C
The AppFW module in the AppSecure suite provides IPS signatures that can be used to monitor traffic and detect malicious activities. AppFW also provides other security controls such as Web application firewall, URL filtering, and application-level visibility.
You have deployed an SRX300 Series device and determined that files have stopped being scanned.
In this scenario, what is a reason for this problem?
Exhibit
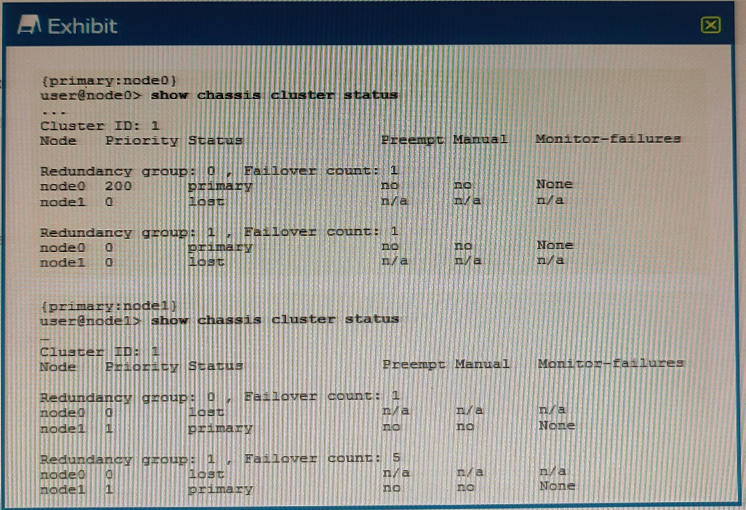
Referring to the exhibit, what do you determine about the status of the cluster.
Answer : C
You are asked to reduce the load that the JIMS server places on your Which action should you take in this situation?
Answer : D
You enable chassis clustering on two devices and assign a cluster ID and a node ID to each device.
In this scenario, what is the correct order for rebooting the devices?
Answer : C
when enabling chassis clustering on two devices, the correct order for rebooting them is to reboot the primary device first, followed by the secondary device. It is not possible for either device to assign itself the correct cluster and node ID, so both devices must be rebooted to ensure the proper configuration is applied.