Juniper Mist AI, Specialist JN0-451 JNCIS-MistAI Exam Questions
You have received a Marvis Actions Missing VLAN notification.
In this scenario, where is the problem?
You are deploying multiple Mist APs across many sites in your network. You must ensure that you apply consistent WxLAN and WLAN policies across all sites within the same organization.
Which configuration object should be used to accomplish this behavior?
You must define VLANs as untagged, tagged, or using VLAN pooling.
In this scenario, where would you accomplish this task in the Juniper Mist UI?
What is the impact of adding more SSIDs to a radio?
Answer : A
The impact of adding more SSIDs to a radio is beacon overhead.So,the correct answer is A.beacon overhead
Click the Exhibit button.
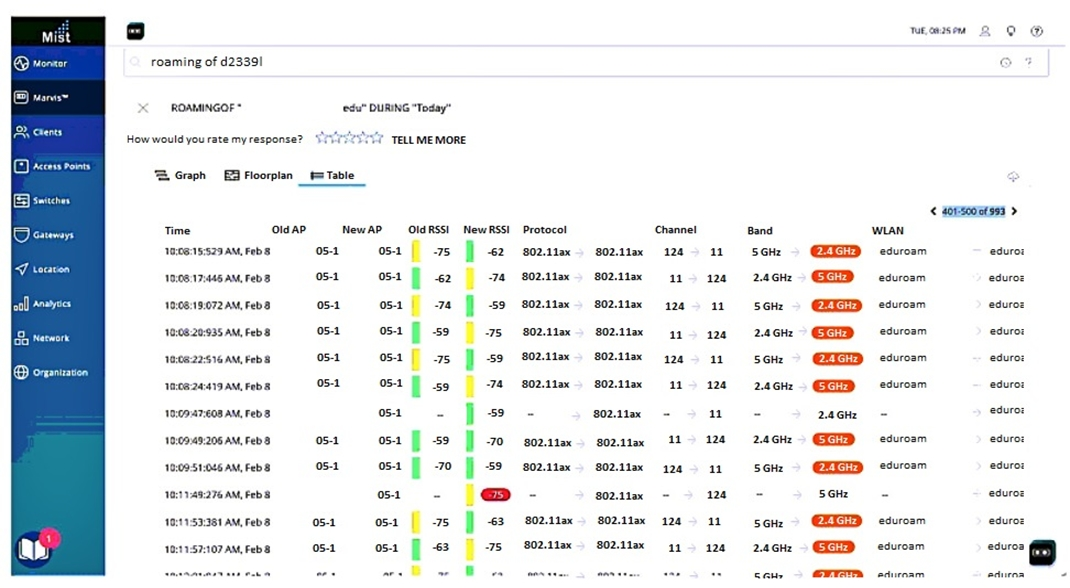
A user opened a ticket. Upon troubleshooting, you determine that frequent roaming is the root cause of the problem.
Referring to the exhibit, which statement describes the roaming issue that the client is experiencing?
Answer : D
The exhibit shows a graph of the client's roaming history over time. The x-axis represents the time and the y-axis represents the access point ID. Each dot on the graph indicates a roam event where the client switched from one access point to another.
The graph shows that the client roamed between different access points multiple times within a short period of time. This indicates that the client was experiencing frequent roams between different access points, which could affect its network performance and user experience.
You are deploying multiple Mist APs across many sites in your network. You must ensure that you can group similar devices together to easily apply consistent WxLAN policies across multiple sites.
Which configuration object should be used to accomplish this behavior?
Answer : B
When deploying multiple Mist APs across many sites in your network and grouping similar devices together to easily apply consistent WxLAN policies across multiple sites, you should use device profiles.
Which two Mist Aps would be used for BLE location? (Choose two.)