Juniper Security, Professional JN0-636 JNCIP-SEC Exam Practice Test
Your organization has multiple Active Directory domain to control user access. You must ensure that security polices are passing traffic based upon the user's access rights.
What would you use to assist your SRX series devices to accomplish this task?
Answer : A
https://www.juniper.net/documentation/en_US/junos/topics/topic-map/security-user-auth-configure-jims.html
Exhibit
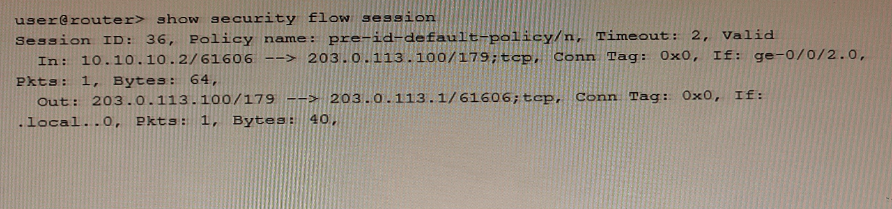
Referring to the exhibit, which type of NAT is being performed?
Answer : D
Source NAT is a type of NAT that is used to translate the source IP address and port number of a packet. This is typically used to allow multiple devices on a private network to access the internet using a single public IP address. In the exhibit, we can see that the source IP address and port number of the packet are being translated from 10.10.10.2/61606 to 203.0.113.100/179. This is a clear indication that Source NAT is being performed.Reference:
Network Address Translation Feature Guide
SRX NAT with Illustrated Examples
In Juniper ATP Cloud, what are two different actions available in a threat prevention policy to deal with an infected host? (Choose two.)
Answer : B, D
In Juniper ATP Cloud, a threat prevention policy allows you to define how the system should handle an infected host. Two of the available actions are:
Close the connection: This action will close the connection between the infected host and the destination to which it is trying to connect. This will prevent the host from communicating with the destination and will stop any malicious activity.
Quarantine the host: This action will isolate the infected host from the network by placing it in a quarantine VLAN. This will prevent the host from communicating with other devices on the network, which will prevent it from spreading malware or exfiltrating data.
Sending a custom message is used to notify the user and administrator of the action taken. Drop the connection silently is not an action available in Juniper ATP Cloud.
The threat prevention policy allows the user to specify different actions for different threat levels. The actions can be applied to the traffic or to the infected host. The actions available for the traffic are:
Permit: Allows the traffic to pass through the SRX Series device without any interruption.
Block: Blocks the traffic and sends a reset packet to the client and the server.
Drop: Drops the traffic silently without sending any reset packet.
Redirect: Redirects the traffic to a specified URL, such as a warning page or a sinkhole server.
The actions available for the infected host are:
None: Does not take any action on the infected host.
Quarantine: Quarantines the infected host by applying a firewall filter that blocks all outbound traffic from the host, except for the traffic to Juniper ATP Cloud or the specified redirect URL.
Custom: Executes a custom script on the SRX Series device to perform a user-defined action on the infected host, such as sending an email notification or triggering an external system.
Therefore, the two different actions available in a threat prevention policy to deal with an infected host are:
Block: This action will block the traffic from or to the infected host and send a reset packet to the client and the server. This will prevent the infected host from communicating with the malicious server or spreading the malware to other hosts.
Quarantine: This action will quarantine the infected host by blocking all outbound traffic from the host, except for the traffic to Juniper ATP Cloud or the redirect URL. This will isolate the infected host from the network and allow the user to remediate the infection.
The following actions are not available or incorrect:
Send a custom message: This is not an action available in the threat prevention policy. However, the user can use the custom action to execute a script that can send a custom message to the infected host or the administrator.
Drop the connection silently: This is an action available for the traffic, not for the infected host. It will drop the traffic without sending any reset packet, which may not be effective in stopping the infection or notifying the user.
Exhibit
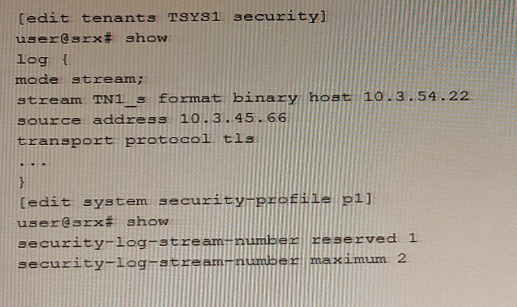
An administrator wants to configure an SRX Series device to log binary security events for tenant systems.
Referring to the exhibit, which statement would complete the configuration?
Answer : D
You want to enforce I DP policies on HTTP traffic.
In this scenario, which two actions must be performed on your SRX Series device? (Choose two )
Answer : A, D
To enforce IDP policies on HTTP traffic on an SRX Series device, the following actions must be performed:
Choose an attacks type in the predefined-attacks-group HTTP-All: This allows the SRX Series device to match on specific types of attacks that can occur within HTTP traffic. For example, it can match on SQL injection or cross-site scripting (XSS) attacks.
Match on application junos-http: This allows the SRX Series device to match on HTTP traffic specifically, as opposed to other types of traffic. It is necessary to properly identify the traffic that needs to be protected.
Disabling screen options on the Untrust zone and specifying an action of None are not necessary to enforce IDP policies on HTTP traffic. The first one is a feature used to prevent certain types of attacks, the second one is used to take no action in case of a match.
Which two statements are correct regarding tenant systems on SRX Series devices? (Choose two.)
Answer : C, D
The following statements are true regarding tenant systems on SRX Series devices:
Each tenant system runs its own instance of the routing protocol process. Each tenant system is isolated, and it has its own routing table, interfaces, and security policies.
A maximum of 500 tenant systems can be configured on a physical SRX device. This allows for a high degree of flexibility and scalability, as each tenant system can be configured with its own set of features and security policies.
A maximum of 32 tenant systems can be configured on a physical SRX device and All tenant systems share a single routing protocol process are not correct statements
Regarding IPsec CoS-based VPNs, what is the number of IPsec SAs associated with a peer based upon?
Answer : D
In IPsec CoS-based VPNs, the number of IPsec Security Associations (SAs) associated with a peer is based on the number of forwarding classes configured for the VPN. The forwarding classes are used to classify and prioritize different types of traffic, such as voice and data traffic. Each forwarding class requires a separate IPsec SA to be established between the peers, in order to provide the appropriate level of security and quality of service for each type of traffic.