Juniper Security, Professional JN0-637 JNCIP-SEC Exam Practice Test
You have configured the backup signal route IP for your multinode HA deployment, and the ICL link fails.
Which two statements are correct in this scenario? (Choose two.)
Answer : A, C
You are asked to see if your persistent NAT binding table is exhausted.
Which show command would you use to accomplish this task?
Answer : D
The command show security nat source persistent-nat-table all provides a comprehensive view of all entries in the persistent NAT table, enabling administrators to monitor and manage resource exhaustion. Refer to Juniper NAT Monitoring Guide for more.
In Junos OS, when persistent NAT is configured, a binding table is created to keep track of NAT sessions and ensure that specific hosts are allowed to initiate sessions back to internal hosts. To check if the persistent NAT binding table is full or exhausted, the correct command must display the entire table.
Correct Command (D):
The command show security nat source persistent-nat-table all will display the entire persistent NAT binding table. This allows you to check whether the table is exhausted or if there is space available for new persistent NAT sessions.
Incorrect Options:
Option A: The command show security nat source persistent-nat-table summary provides a summary view but does not give detailed insights into whether the table is exhausted.
Option B and Option C: These commands deal with general NAT source summaries or pools, which are not related specifically to persistent NAT bindings.
Juniper Reference:
Juniper Persistent NAT Documentation: Describes the persistent NAT binding table and the commands used to monitor its status.
Exhibit:

Your company uses SRX Series devices to establish an IPsec VPN that connects Site-1 and the HQ networks. You want VoIP traffic to receive priority over data traffic when it is forwarded across the VPN.
Which three actions should you perform in this scenario? (Choose three.)
Answer : B, C, E
Click the Exhibit button.
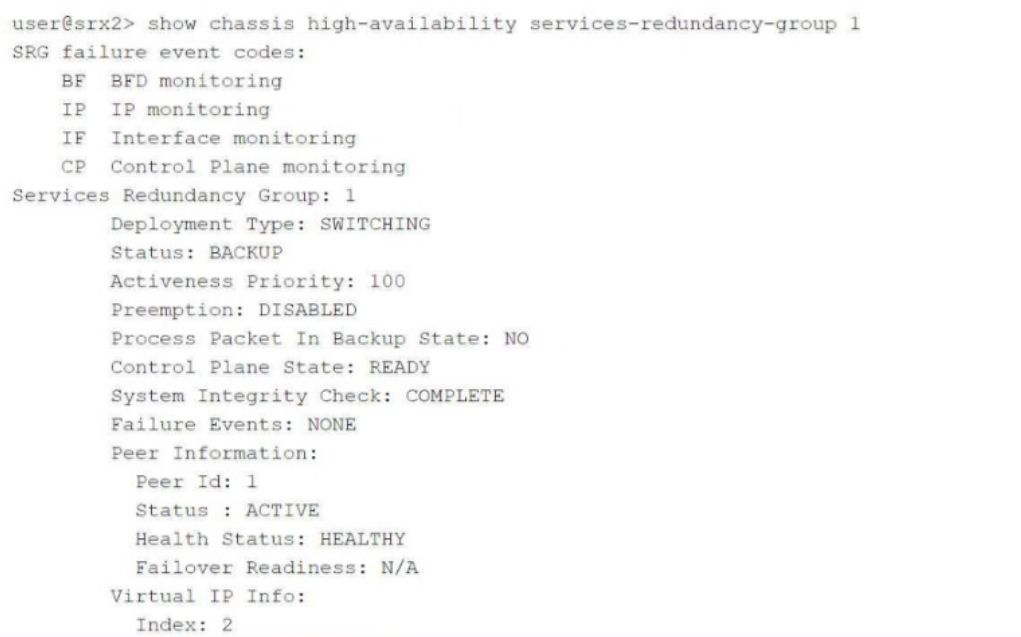
Referring to the exhibit, which two statements are correct? (Choose two.)
Answer : C, D
A company has acquired a new branch office that has the same address space of one of its local networks, 192.168.100/24. The offices need to communicate with each other.
Which two NAT configurations will satisfy this requirement? (Choose two.)
Answer : A, D
The problem describes two offices needing to communicate, but both share the same IP address space, 192.168.100.0/24. To resolve this, NAT must be configured to translate the conflicting address spaces on each side. Here's how each of the configurations works:
Option A (Correct):
This source NAT rule translates the source address of traffic from Office B to Office A. By configuring source NAT, the source IP addresses from Office B (192.168.210.0/24) will be translated when communicating with Office A (192.168.200.0/24). This method ensures that there is no overlap in address space when packets are transmitted between the two offices.
Option D (Correct):
This is a source NAT rule configured on Office B, which translates the source addresses from Office A to prevent address conflicts. It ensures that when traffic is initiated from Office A to Office B, the overlapping address range (192.168.100.0/24) is translated.
Options B and C (Incorrect):
These options involve static NAT rules that map address ranges between the two offices, but they do not resolve the overlapping IP address space issue effectively. Static NAT is not the optimal solution in this scenario since the problem involves address space conflict, which requires translation of source addresses during communication.
Juniper Reference:
Juniper NAT Configuration Guide: Detailed instructions on how to configure source NAT and resolve address conflicts between networks.
Referring to the exhibit,
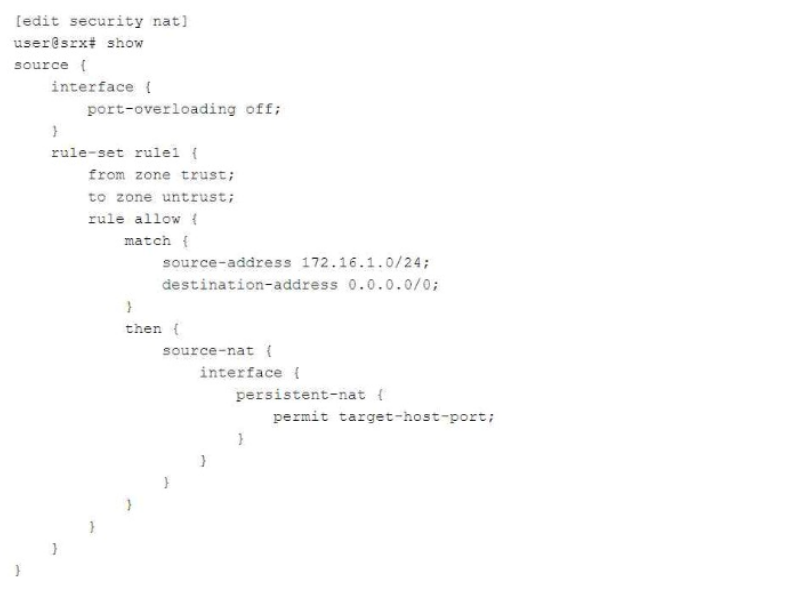
which two statements are correct about the NAT configuration? (Choose two.)
Answer : B, D
Persistent NAT with target-host restricts session initiation to specific addresses, enhancing security. Reflexive NAT supports multiple connections by preserving the original port. Refer to Juniper NAT Configuration Documentation.
Referring to the NAT configuration shown in the exhibit:
Specific Host Can Initiate a Session (Answer B): The configuration uses persistent NAT with the permit target-host-port statement. This allows a specific external host (based on the target host and port used in the initial session) to initiate a session back to the internal host after the initial session has been established.
Persistent NAT ensures that the translation state is maintained, allowing external hosts to connect back only under specific conditions (e.g., the same target host and port as used in the original connection).
Original Destination Port (Answer D): The original destination port used by the internal host is retained as the source port when the session is established from outside to inside. This behavior is a result of how persistent NAT binds the internal and external sessions, ensuring that communication occurs over the same port used for the initial session.
Which role does an SRX Series device play in a DS-Lite deployment?
Answer : A