Page: 1
/ 14
Total 64 questions
Linux Foundation Certified Kubernetes Security Specialist CKS Exam Questions
Question 1
SIMULATION
Context
A default-deny NetworkPolicy avoids to accidentally expose a Pod in a namespace that doesn't have any other NetworkPolicy defined.
Task
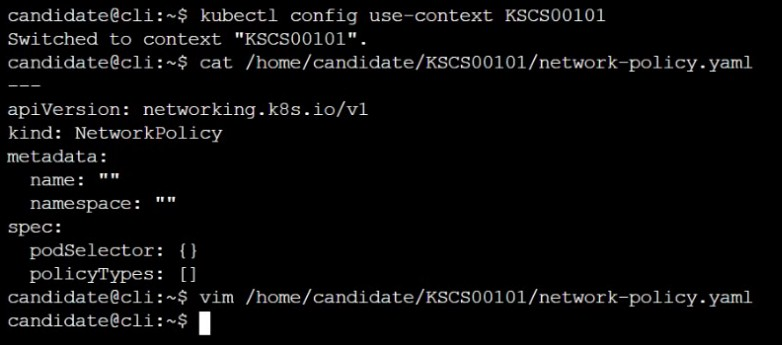
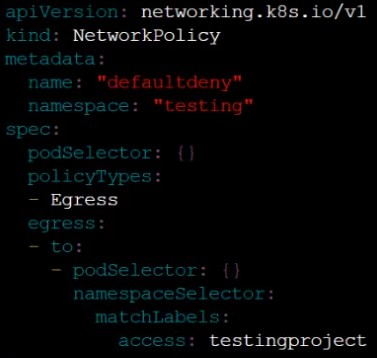
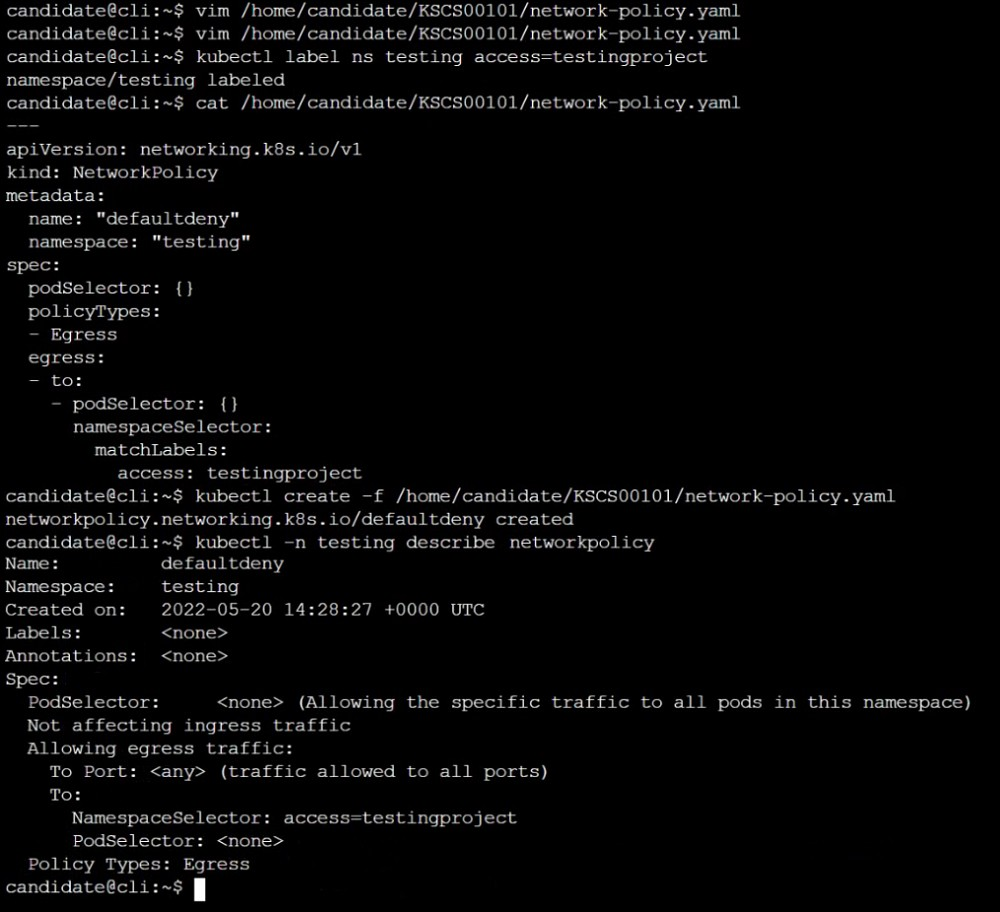
Create a new default-deny NetworkPolicy named defaultdeny in the namespace testing for all traffic of type Egress.
The new NetworkPolicy must deny all Egress traffic in the namespace testing.
Apply the newly created default-deny NetworkPolicy to all Pods running in namespace testing.

Answer : A