Logical Operations Certified CyberSec First Responder CFR-210 CFR Exam Practice Test
A malicious attacker has compromised a database by implementing a Python-based script that will automatically establish an SSH connection daily between the hours of 2:00 am and 5:00 am. Which of the following is the MOST common motive for the attack vector that was used?
Answer : D
A system administrator needs to analyze a PCAP file on a Linux workstation where the use of GUI-based applications is restricted. Which of the following command line tools can the administrator use to analyze the PCAP?
Answer : A
A company website was hacked via the SQL query below:
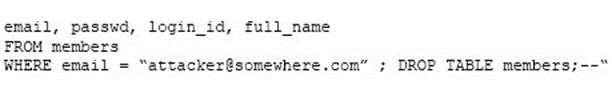
Which of the following did the hackers perform?
Answer : D
An attacker has decided to attempt a brute force attack on a UNIX server. In order to accomplish this, which of the following steps must be performed?
Answer : C
A system administrator is informed that a user received an email containing a suspicious attachment. Which of the following methods is the FASTEST way to determine whether the file is suspicious or not?
Answer : D
A security professional has been tasked with the protection of a specific set of information essential to a corporation's livelihood, the exposure of which could cost the company billions of dollars in long-term revenue. The professional is interested in obtaining advice for preventing the theft of this type of information. Which of the following is the BEST resource for finding this material?
Answer : A
A logfile generated from a Windows server was moved to a Linux system for further analysis. A system administrator is now making edits to the file with vi and notices the file contains numerous instances of Ctrl-M (^M) characters. Which of the following command line tools is the administrator MOST likely to use to remove these characters from the logfile? (Choose two.)
Answer : A, C