Microsoft Designing and Implementing a Server Infrastructure 70-413 Exam Practice Test
You need to generate the required report
Which tool should you use?
Answer : C
Scenario: Consolidation reports
The company requires a report that describes the impact of consolidation. The report must provide the following information:
* An inventory of the existing physical server environment
* Visual charts that show the reduction of physical servers
You implement and authorize the new DHCP servers. You import the server configurations and the scope configurations from PA1 and AM1.
You need to ensure that clients can obtain DHCP address assignments after you shut down PA1 and AM1. The solution must meet the technical requirements.
What should you do?
Answer : B
You plan to simplify the organizational unit (OU) structure for a company. You must consolidate all member servers in the domain to a single OU named MemberServers.
You must apply Group Policy settings for servers that meet the following criteria:
Server operating systems: Windows Server 2012
Server hardware platform: 64-bit
Server memory: less than 16 GB of RAM
Solution: You create a WMI filter action that includes the following query:

Does this meet the goal?
You need to recommend a remote access solution that meets the VPN requirements.
Which role service should you include in the recommendation?
Answer : B
Scenario:
A server that runs Windows Server 2012 will perform RADIUS authentication for all of the VPN connections.
Ensure that NAP with IPSec enforcement can be configured.
Network Policy Server
Network Policy Server (NPS) allows you to create and enforce organization-wide network access policies for client health, connection request authentication, and connection request authorization. In addition, you can use NPS as a Remote Authentication Dial-In User Service
(RADIUS) proxy to forward connection requests to a server running NPS or other RADIUS servers that you configure in remote RADIUS server groups.
NPS allows you to centrally configure and manage network access authentication, authorization, are client health policies with the following three features: RADIUS server. NPS performs centralized authorization, authorization, and accounting for wireless, authenticating switch, remote access dial-up and virtual private network (VNP) connections. When you use NPS as a RADIUS server, you configure network access servers, such as wireless access points and VPN servers, as RADIUS clients in NPS. You also configure network policies that NPS uses to authorize connection requests, and you can configure RADIUS accounting so that NPS logs accounting information to log files on the local hard disk or in a Microsoft SQL Server database.
Your company has a main office and a branch office.
The network contains an Active Directory domain named contoso.com. The domain contains three domain controllers. The domain controllers are configured as shown in the following table.
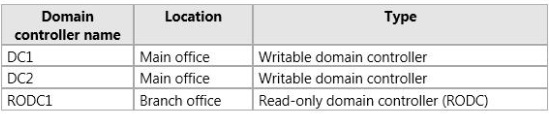
The domain contains two global groups. The groups are configured as shown in the following table.

You need to ensure that the RODC is configured to meet the following requirements:
Cache passwords for all of the members of Branch1Users.
Prevent the caching of passwords for the members of Helpdesk.
What should you do?
Answer : A
The Password Replication Policy acts as an access control list (ACL). It determines if an RODC should be permitted to cache a password. After the RODC receives an authenticated user or computer logon request, it refers to the Password Replication Policy to determine if the password for the account should be cached.
https://technet.microsoft.com/en-us/library/cc730883(v=ws.10).aspx
Your network contains an Active Directory forest named contoso.com. The forest contains a single domain and two sites named Montreal and Vancouver.
Montreal contains an IP Address Management (IPAM) server named Server1 that is used to manage all of the DHCP servers and the DNS servers in the site.
Vancouver contains several DHCP servers and several DNS servers.
In Vancouver, you install the IP Addreontreal contains an IP address Management (IPAM) server named Server1 that ifeature on a server named Server2.
You need to recommend which configurations must be performed to ensure that the DHCP servers and the DNS servers in Vancouver are managed by Server2.
What should you recommend?
Answer : C
Invoke-IpamGpoProvisioning
Creates and links group policies in the specified domain for provisioning required access settings on the servers managed by the computer running the IPAM server.
https://technet.microsoft.com/en-us/library/jj553805(v=wps.630).aspx
Your network contains an Active Directory forest named contoso.com.
You plan to automate the deployment of servers that run Windows Server 2012.
You identify the following requirements for the deployment:
Update the custom images that will be used for the deployment.
Add custom drivers to the images that will be used for the deployment.
Add software packages to the images that will be used for the deployment.
Perform a zero touch bare-metal installation that uses Wake On LAN.
A network consultant recommends using Windows Deployment Services (WDS) and the Windows Assessment and Deployment Kit (Windows ADK) to deploy the servers.
You need to identify which requirements are achieved by using the consultant's recommendations.
Which requirements should you identify? (Each correct answer presents part of the solution. Choose all that apply.)
Answer : A, D
Microsoft Deployment Toolkit 2010
MDT 2010 requires Windows AIK for Windows.
Manage your images, from adding/removing drivers to easily swapping out the operating system you would like to deploy.
Incorrect:
Not C: System Center Configuration Manager (ConfigMgr)
ConfigMgr allows you to push an OSD to the computers of your choice at the time of your choosing due to its built in Wake on LAN (WOL) feature.